The Tor Project team has unveiled a new utility named oniux, designed to enforce network isolation for Linux applications through Tor at the kernel level. Unlike proxy-based solutions, this tool establishes a dedicated network namespace, eliminating even the theoretical risk of traffic leakage that bypasses Tor.
Oniux leverages core capabilities of the Linux kernel: each application is launched within an isolated environment devoid of access to standard network interfaces. Instead, a virtual interface named onion0 is created, ensuring that all traffic is routed exclusively through Tor. This approach eradicates the possibility of accidental or malicious data transmission outside the protected channel.
Developed in Rust, the tool incorporates the Arti and onionmasq libraries. It can be installed via Cargo, and routing any application through Tor requires nothing more than prepending the command with oniux. Both command-line utilities and graphical applications are supported.
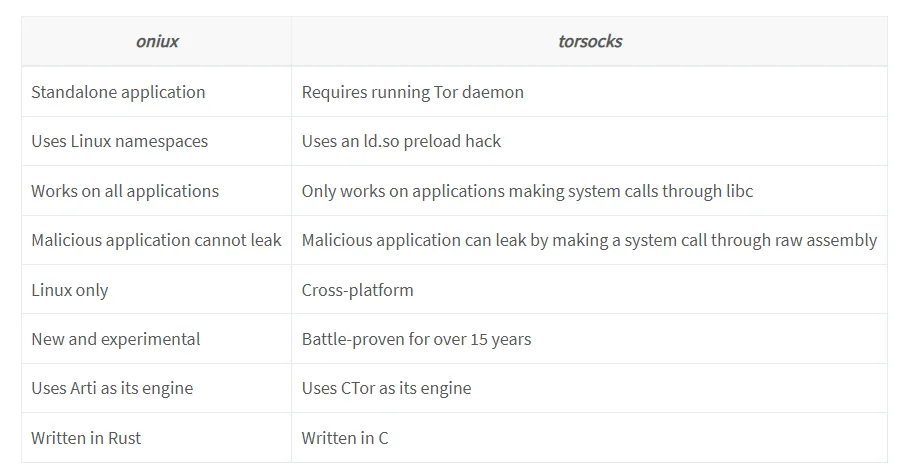
The primary distinction from the conventional torsocks tool lies in the depth of isolation. While torsocks operates by intercepting libc calls—making it vulnerable to statically linked or low-level binaries—oniux functions at the system call level, thereby neutralizing such circumvention.
Internally, oniux spawns a child process within segregated namespaces, configures a dedicated /proc, isolates DNS using a custom resolv.conf, launches a TUN interface, and passes the file descriptor back to the parent process. Once privileges are dropped, the target command is executed within the confined environment.
The developers emphasize that oniux remains experimental and is currently intended for Linux systems. Nevertheless, it already demonstrates stable performance and addresses a critical challenge: ensuring network traffic isolation without relying on potentially untrustworthy proxy wrappers.
The team encourages users to try oniux and provide feedback to help refine the tool into a production-ready solution on par with torsocks.


