A user who had purchased an ASUS motherboard discovered that the driver installation software—automatically triggered via the BIOS—contained a critical vulnerability allowing arbitrary code execution with administrative privileges, all through a single click. The flaw resided in the DriverHub component, which is installed upon the first Windows boot and operates silently in the background without a graphical interface.
DriverHub communicates with driverhub.asus.com via a local RPC service on port 53000, exposing an API to websites that can manage drivers, retrieve device information, reboot the system, and download and execute binaries. The initial security measure was an Origin header check—accepting only requests originating from driverhub.asus.com. However, the implementation relied on substring matching, rendering it vulnerable to bypass using domains like driverhub.asus.com.attacker.com.
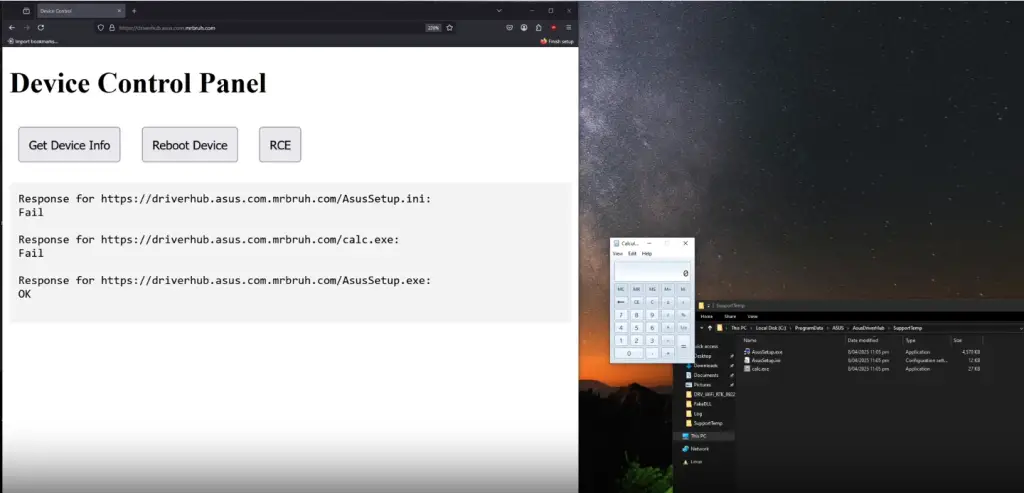
Upon analyzing the code, the researcher identified a particularly interesting endpoint, UpdateApp, which could download and execute any binary signed by ASUS. If the signature failed verification, the file would still be saved to disk—paving the way for an attack chain.
The linchpin of the exploit was the ASUS Wi-Fi driver installer, which included a binary named AsusSetup.exe that parsed its configuration from an AsusSetup.ini file. This file featured a directive—SilentInstallRun—specifying which file to execute during a silent install. The researcher crafted an INI file configured to launch calc.exe, uploaded it via UpdateApp, and then triggered the execution of the signed AsusSetup.exe. As a result, calc.exe launched with administrative privileges, demonstrating full remote code execution.
The attack chain unfolded as follows:
- Visit a webpage hosted on a subdomain like driverhub.asus.com.
- Submit a request to UpdateApp to upload calc.exe (which is not executed due to lack of a valid signature).
- Upload a custom AsusSetup.ini with a directive to launch calc.exe.
- Upload a signed AsusSetup.exe, which is executed with the -s flag and subsequently runs calc.exe with elevated privileges.
The researcher reported the vulnerability on April 8, 2025. ASUS responded the following day with a fixed version, and the patch was publicly released on April 18. The issues were assigned CVE-2025-3462 and CVE-2025-3463, with CVSS scores of 8.4 and 9.4, respectively. The researcher also examined certificate transparency logs to determine whether any suspicious domains had been registered in advance and concluded that the exploit had not been used in the wild prior to disclosure.
ASUS declined to offer a bounty, instead proposing to list the researcher in their “Hall of Fame.” Notably, the CVE descriptions were vague—rather than explicitly acknowledging remote code execution, the advisory merely stated that the flaw “could allow untrusted sources to influence system behavior.”
One curious detail: when the researcher attempted to submit the vulnerability report via ASUS’s online form, it was blocked as “malicious” by the CloudFront CDN platform. Ultimately, they had to submit a video link instead of a proof-of-concept file. It was also revealed that the “Install All” button in DriverHub silently installed ASUS ArmouryCrate, Norton360, and even WinRAR—yet Wi-Fi still failed to work, prompting the user to purchase an external adapter.


