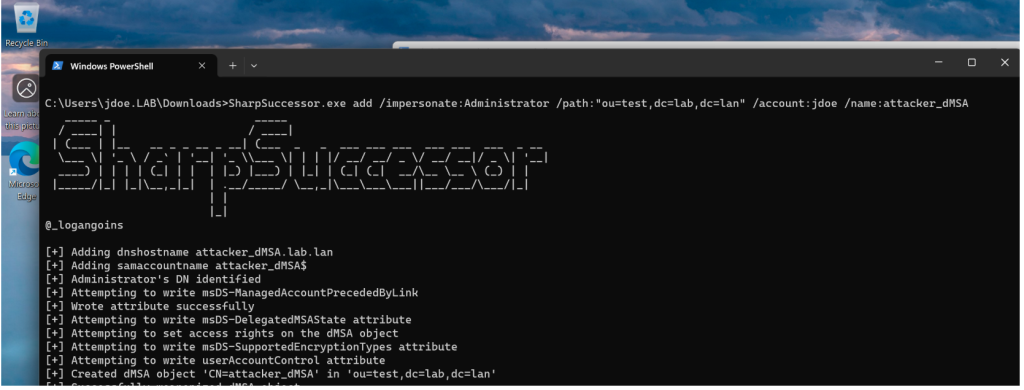
A fully functional exploit tool has been released for the previously discovered critical vulnerability in Windows Server 2025, known as BadSuccessor. Developed by security researcher Logan Goins, the SharpSuccessor exploit fully automates the attack, transforming what was once a complex privilege escalation technique into an accessible script usable by virtually anyone. Now, attackers need only minimal permissions in Active Directory to seize domain administrator privileges.
The emergence of SharpSuccessor marks a shift from a theoretical attack vector to a tangible threat. As the vulnerability affects the architecture of the new delegated Managed Service Account (dMSA) feature—and with Microsoft yet to release an urgent fix—enterprises are left exposed. The exploit requires just a single permission: the right to create objects within any Organizational Unit container, a setting commonly enabled across most domains.
BadSuccessor was first disclosed approximately a week ago by Akamai researcher Yuval Gordon. It exploits the dMSA migration mechanism to generate rogue accounts capable of fully mimicking legitimate users. This is achieved by manipulating two Active Directory object attributes: msDS-ManagedAccountPrecededByLink and msDS-DelegatedMSAState. As a result, an attacker-crafted dMSA inherits the permissions of a targeted user, including those with domain administrator rights.
SharpSuccessor automates this entire process. It enables the creation of a fraudulent dMSA by specifying a user to impersonate and an OU path where the attacker holds minimal privileges. The attack continues with Rubeus, a Kerberos ticketing tool that facilitates the sequential acquisition of TGT and service tickets with elevated privileges. The chain culminates in gaining access to domain controllers, including support for SMB connections.
What raises particular alarm is the scale of potential abuse: in 91% of tested environments, regular users were found to possess sufficient privileges to exploit BadSuccessor. This stems from the exploit’s reliance on standard Active Directory delegation configurations, rather than elevated permissions.
Despite acknowledgment of the issue, Microsoft has categorized it as a “moderate severity” vulnerability and has not yet issued a timely patch. Until a fix becomes available, experts advise using Akamai’s detection script—Get-BadSuccessorOUPermissions.ps—to identify vulnerable Organizational Units, and to restrict dMSA creation to trusted administrators only.
The arrival of SharpSuccessor underscores how dangerous delays in addressing infrastructure-level vulnerabilities can be. What once required deep expertise and intricate manipulation of Active Directory objects and Kerberos tickets is now reduced to a one-click utility.


