Today, most antivirus and EDR systems monitor which commands are executed within a system. These security solutions often rely on the content of the command line to determine whether a process is benign or malicious. However, it has emerged that attackers can easily deceive such mechanisms by altering the appearance of a command without changing its underlying functionality—a technique known as command-line obfuscation.
In the past, security tools primarily searched for threats in malicious files such as viruses and trojans. Nowadays, however, many attacks are entirely fileless. Instead of deploying malware, attackers exploit legitimate system utilities like PowerShell, curl, msiexec, or taskkill. These so-called malwareless intrusions mimic normal user behavior and are thus less likely to trigger suspicion.
To filter out such suspicious activity, security systems have begun analyzing command arguments. For example, taskkill /f /im winword.exe might be harmless, whereas taskkill /f /im security_process.exe could signal an attempt to disable protective measures. Yet attackers have found a way around this too—by modifying the commands to look different while retaining the same behavior. This is the essence of obfuscation.
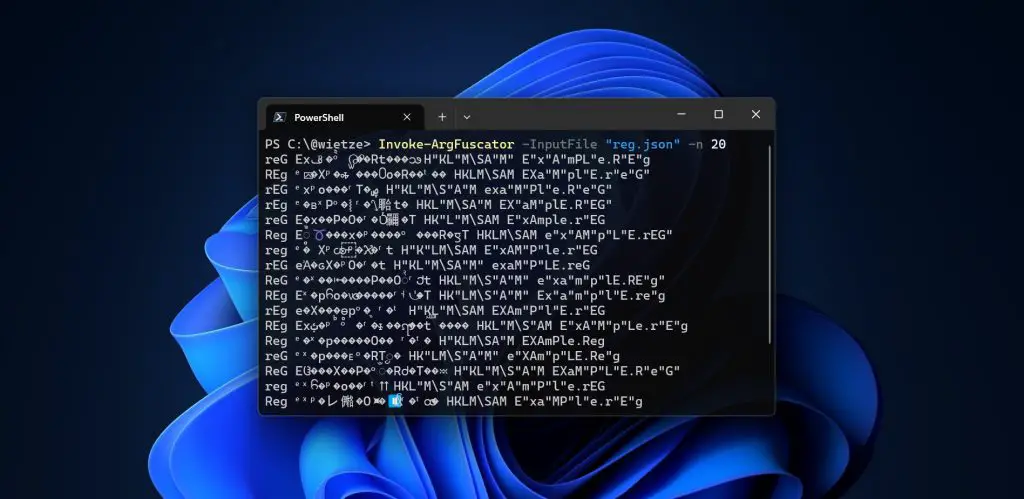
Such obfuscation does not depend on the shell itself but exploits how individual programs parse their arguments. Techniques include substituting characters, inserting extraneous symbols, using unusual quotation marks, or altering letter case. As a result, a command like reg export HKLM\SAM out.reg may be rewritten as rEg "e"xP"o"rT HK"L"M\S"A"M ouT.ReG, yet still execute correctly—often without triggering antivirus alerts.
Windows, in particular, offers fertile ground for these tricks. Examples include:
- Replacing
/fwith-f; - Swapping standard characters with Unicode lookalikes (e.g.,
ˣforx); - Injecting invisible or obscure Unicode symbols;
- Reordering command arguments;
- Obscuring paths using
..\patterns.
While Linux and macOS have fewer such vectors, they are not immune. One may, for instance, truncate long arguments or represent IP addresses in unconventional formats, such as using 2130706433 in place of 127.0.0.1.
To assess the susceptibility of system utilities to such techniques, the project’s author examined 68 popular Windows tools—including curl, taskkill, reg, powershell, and msiexec. A dedicated tool, analyse_obfuscation, was developed to automatically test whether obfuscated commands still function as intended. If a command executed successfully in its obfuscated form, the method was deemed effective.
Each tested utility was paired with a unique configuration file, detailing which obfuscation techniques succeeded and which did not. Based on these models, the author created Invoke-ArgFuscator, a tool that generates obfuscated commands according to specified rules and with varying degrees of randomness, ensuring a unique result each time.
All findings are compiled on a dedicated website, where users can select from the 68 utilities, input a command, and receive an obfuscated variant. The platform also allows users to customize obfuscation settings or build their own models.
Although these methods pose a serious challenge for defenders, there are countermeasures. For instance, analysts can scan command lines for abnormal Unicode symbols, excessive quotation marks, or abrupt case changes. Another strategy is to normalize commands prior to analysis—removing extraneous characters to expose their true intent. However, the most effective defense lies not in text analysis alone but in behavioral monitoring: for example, if msiexec attempts to access the internet, it is suspicious, regardless of how innocuous the command line may appear.


