In September 2024, NVIDIA released a security update addressing the critical vulnerability CVE-2024-0132 in its Container Toolkit. The issue stemmed from a time-of-check to time-of-use (TOCTOU) race condition, which enabled attackers to orchestrate a so-called “container escape” and gain unauthorized access to host system resources. The flaw received a high CVSS severity score of 9.0. However, it was later discovered that the mitigation was incomplete, and by early 2025, security researchers observed methods to circumvent it.
An in-depth analysis conducted by Trend Micro confirmed that NVIDIA’s patch failed to fully eliminate the vulnerability. Moreover, their investigation uncovered an additional performance-related flaw affecting Docker on Linux, capable of triggering denial-of-service (DoS) conditions. This dual threat—compromising both security and system stability—poses a particularly grave concern for server environments.
The newly identified vulnerability has been cataloged as CVE-2025-23359 and assigned the same critical CVSS score of 9.0. It is rooted in the mount_files function, which manages file system mounting. Researchers discovered the absence of proper locking mechanisms during the mount operation, allowing for the underlying object to be modified mid-process. If an attacker already has code execution capabilities within a container, this flaw could be exploited to escalate privileges and execute arbitrary code on the host machine.
Interestingly, as early as February 2025, the security firm Wiz had warned of a potential bypass for the original vulnerability. Their concerns have now been substantiated through technical validation. Both flaws have been addressed in version 1.17.4 of the NVIDIA Container Toolkit, though the effectiveness of the patch depends on enabling certain runtime parameters—such as allow-cuda-compat-libs-from-container.
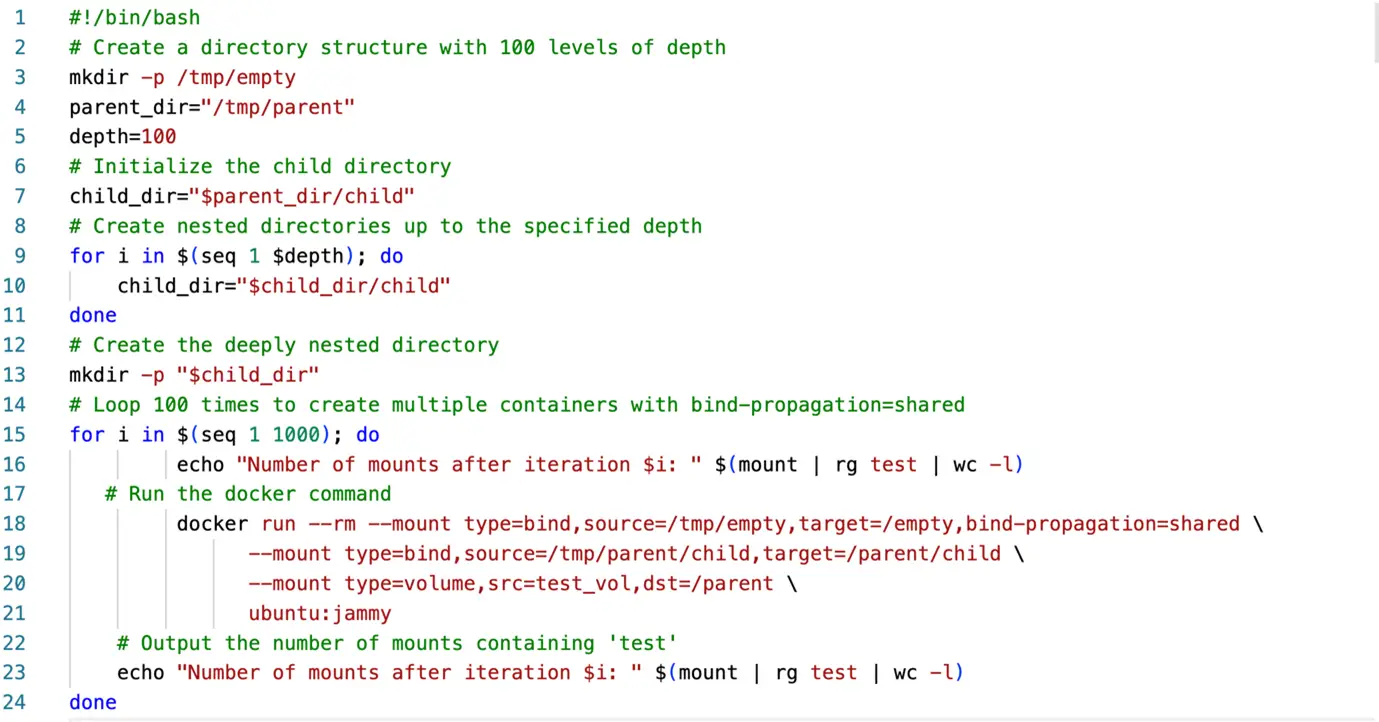
In addition to the escape risk, researchers identified a subtler yet significant threat: resource leakage due to persistent entries in the Linux mount table. When containers are launched with multiple mount points and the bind-propagation=shared setting, residual entries may linger after container deletion. This leads to unchecked growth of the mount table and depletion of file descriptors, eventually preventing Docker from launching new containers or allowing users to connect to the host—even via SSH.
To mitigate these risks, experts recommend implementing regular monitoring of the mount table, restricting Docker API access, enforcing strict access controls, and auditing volumes and container-to-host bindings. These precautions are especially vital for environments that employ CUDA libraries in isolated containerized settings.
The existence of two concurrent critical issues—one affecting security and the other performance—underscores the necessity of adopting a multi-layered security strategy for containerized infrastructure. Even when official patches are issued, their thoroughness and efficacy must be independently verified through robust defensive measures.


