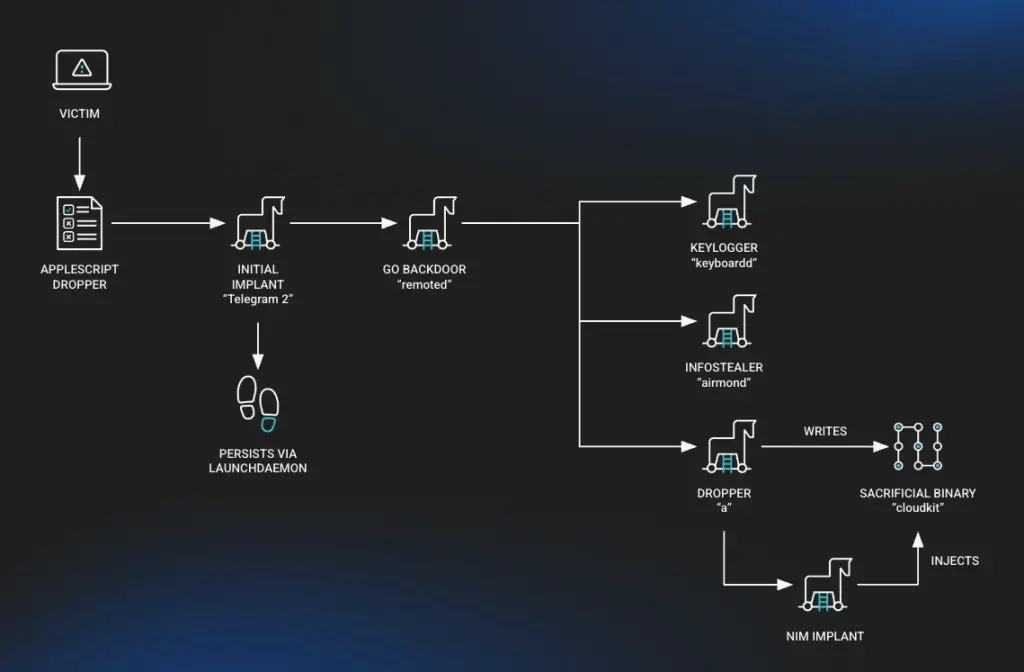
Visualization of attack chain
The North Korea-linked hacking group BlueNoroff has begun leveraging deepfake technology to impersonate senior executives during Zoom video calls, persuading company employees to install macOS-targeted malware. This emerging tactic showcases a sophisticated blend of social engineering and custom-developed malware tailored for cryptocurrency theft.
The incident was uncovered on June 11, 2025, by researchers at Huntress. As with previous BlueNoroff campaigns, the primary objective was the exfiltration of digital assets. The attack bore clear hallmarks consistent with findings from SentinelLabs, Microsoft, Jamf, and Kaspersky Lab, all of whom have been tracking similar operations.
The victim was an employee of a tech firm who was approached via Telegram by threat actors posing as external consultants. They invited him to a meeting via a Calendly link, ostensibly for a Google Meet session. In reality, the link redirected to a counterfeit Zoom page hosted on attacker-controlled infrastructure—an approach reminiscent of techniques used by another North Korean group known as Elusive Comet.
During the virtual meeting, the victim was presented with deepfaked video feeds of familiar company executives, heightening the illusion of legitimacy. Citing a malfunctioning microphone on the victim’s end, the “executives” urged him to install a Zoom extension purportedly designed to resolve the issue. The download link, sent via Telegram, led to an AppleScript file named zoom_sdk_support.scpt.
Upon execution, the script opened Zoom’s genuine SDK page—but not before processing 10,500 blank lines and then executing a malicious command that fetched a secondary payload from a spoofed domain (support.us05webzoom.biz). Although the attackers had already removed the core payload from their servers at the time of investigation, a sample was located on VirusTotal, enabling researchers to reverse-engineer its capabilities.
The script disabled bash command history, checked for the presence of Rosetta 2—Apple’s translation layer for x86_64 code—and silently installed it if absent. It then created a hidden file .pwd and downloaded a malicious component into the /tmp directory under the guise of icloud_helper.
Huntress identified eight distinct malicious binaries on the infected Mac. The primary components included:
- Telegram 2: A Nim-based implant masquerading as a Telegram update. It operated on a scheduled basis, maintaining persistence and initiating the loading of other malware components. Remarkably, it was signed with a legitimate Telegram developer certificate, allowing it to evade suspicion.
- Root Troy V4: A Go-based backdoor facilitating remote command execution, the deployment of additional payloads, and full post-exploitation control. It preserved configuration states and orchestrated the broader malicious infrastructure.
- a (InjectWithDyld): A second-stage loader responsible for decrypting implants and injecting them into memory. It utilized macOS APIs for process injection and self-deletion post-execution.
- XScreen (keyboardd): A surveillance module capturing keystrokes, screen activity, and clipboard content, all relayed to a command-and-control server.
- CryptoBot (airmond): An infostealer focused on over 20 cryptocurrency wallets. It exfiltrated sensitive data, storing it in an encrypted local cache for later retrieval by the attackers.
This attack underscores the escalating technical sophistication of BlueNoroff, now exploiting AI-generated deepfakes alongside bespoke macOS malware. According to Huntress, many macOS users mistakenly believe their systems are inherently secure. Yet, as macOS adoption rises in corporate environments, threat actors are increasingly adapting their arsenals accordingly. These campaigns target not only large-scale cryptocurrency theft but also precise intrusions into enterprise infrastructure—demanding heightened awareness and advanced defense strategies from end users.


