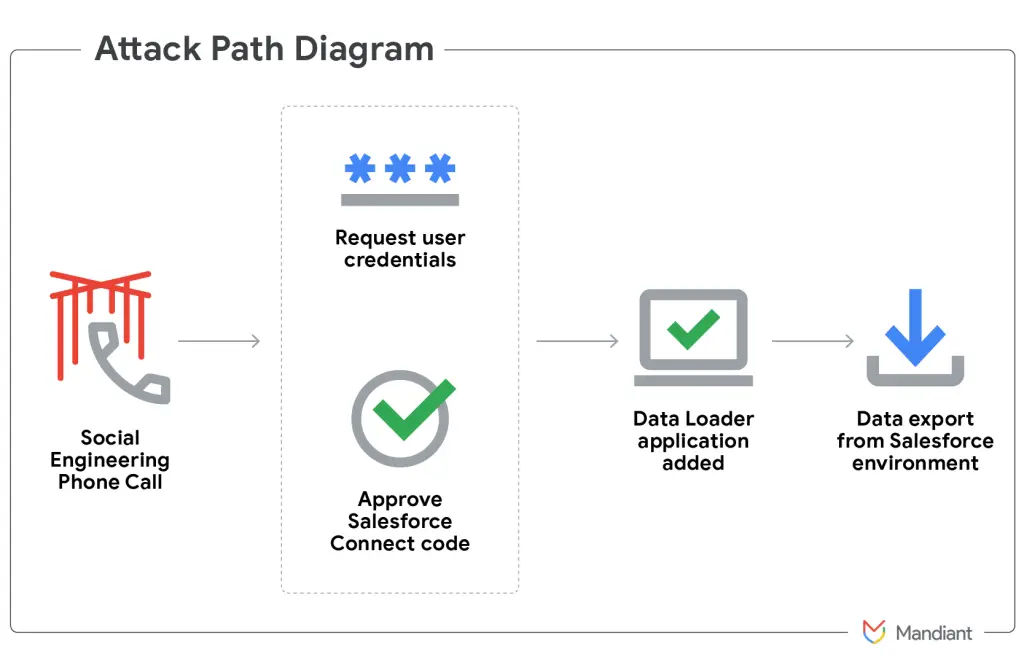
Hackers affiliated with the group UNC6040, tracked by Google’s Threat Intelligence Group, have been implicated in a series of targeted attacks against corporate Salesforce clients. Their primary tactic is voice phishing—or “vishing”—in which they deceive employees via phone calls into installing a counterfeit version of the legitimate Data Loader tool, used for bulk data uploads within the Salesforce environment.
The attack scheme hinges on social engineering: the victim receives a call and is directed to a seemingly official website for connecting Salesforce applications. There, a malicious application masquerading as Data Loader is hosted. If the employee proceeds with the installation, the attackers gain direct access to the organization’s Salesforce environment—enabling them to execute queries, exfiltrate sensitive information, and deepen their foothold within the infrastructure.
This initial access often serves as a gateway into the company’s broader internal networks and other integrated cloud services. As noted by the Mandiant team (a division of Google), UNC6040 is a financially motivated threat group specializing in compromising Salesforce accounts to orchestrate large-scale data theft.
Researchers describe UNC6040’s technical infrastructure as bearing similarities to the decentralized cybercriminal ecosystem known as The Com—a loosely connected constellation of smaller, semi-autonomous groups.
According to Google, UNC6040 has targeted approximately 20 organizations in recent months. In several instances, the attackers succeeded in extracting data. Among the victims was Coca-Cola Europacific Partners, one of the largest Coca-Cola distributors in the United Kingdom, from which 64 GB of data was reportedly stolen. However, it is believed that the company’s IT infrastructure itself was not directly breached.
Salesforce issued a warning in March 2025 regarding the potential for such attacks. Company representatives emphasized that the threat is not linked to any vulnerabilities within the Salesforce platform itself. Rather, the attacks rely entirely on social engineering and the cybersecurity unawareness of individual employees. Such threats to cloud security, they noted, demand a holistic and multilayered approach to protecting enterprise systems.
Salesforce declined to disclose the precise number of affected clients, but affirmed that the incidents were limited in scope and do not represent a widespread compromise.


