A critical vulnerability has been discovered in the enterprise solution Netwrix Password Secure, enabling authenticated attackers to execute arbitrary code on other users’ systems. The flaw affects all versions up to and including 9.2.2, including build 9.2.0.32454, across both client and server components.
The issue was identified by experts at 8com and officially disclosed on May 22, 2025. The vulnerability resides in the document-sharing functionality: improper validation of file paths allows executables—such as PowerShell—to be disguised as seemingly benign file types like PDFs or DOCX documents.
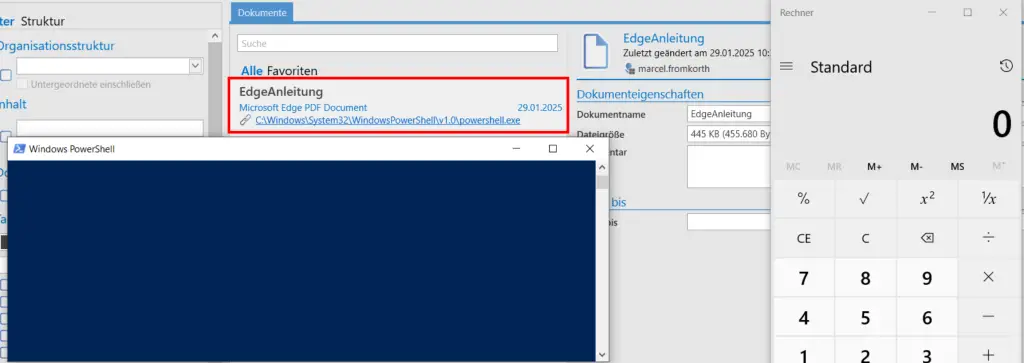
Upon examination, researchers found that the OpenInDefaultProgram method in the DocumentsHelper class launches files based on system-associated extensions using the ProcessFileInfo object. While the initial upload process enforces restrictions by excluding formats such as .exe, subsequent updates to document links bypass thorough validation, checking only the document type while neglecting the integrity of the file path.
This loophole allows an attacker to alter the DocumentPath to point to “PowerShell.exe” or another executable file, while preserving metadata that suggests the document is safe. The DocumentParams parameter poses an additional threat, as it permits arbitrary arguments to be passed to the command. Exploiting this vector, researchers successfully executed arbitrary code—such as launching the Windows Calculator—immediately after a victim clicked the spoofed link.
Though the exploit requires authenticated access and user interaction, it can be easily disguised as a harmless link or desktop shortcut. An alternative attack scenario involves leveraging executables hosted on network resources, though local path manipulation to PowerShell has proven more practical.
Netwrix developers were notified of the issue on January 28, 2025, and received a working proof-of-concept the following day. Upon validation, the vulnerability was acknowledged on February 11, and a patch was released in all versions beyond 9.2.2. Full details were published in Security Bulletin ADV-2025-009 on April 1, 2025.
Users are strongly urged to update their software without delay to mitigate the risk of remote code execution, which could lead to the compromise of sensitive data or unauthorized access within the organization.
This incident underscores the critical importance of rigorous input validation and secure file-handling mechanisms in systems designed to safeguard vital information.


