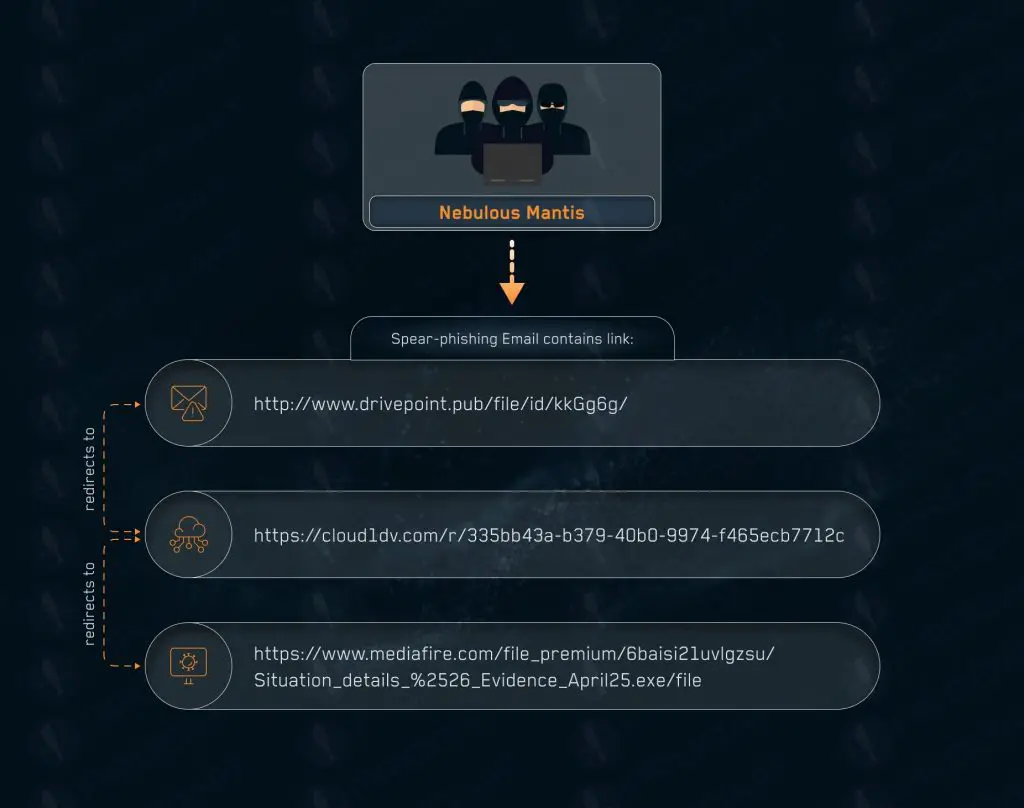
The cyber-espionage group known as Nebulous Mantis has once again drawn the attention of information security experts. According to intelligence from PRODAFT, the threat actors possess a sophisticated remote access trojan, RomCom RAT, which has been actively deployed since at least mid-2022.
What sets this malware apart is its use of advanced evasion techniques — including stealth operations via native operating system functions, encrypted communications with command-and-control servers, and a resilient infrastructure built on hosting services immune to takedown efforts. The technical backend has been attributed to a cybercriminal operating under the alias LARVA-290.
Active since 2019, the group is also known by various aliases, including Cuba, Void Rabisu, Storm-0978, among others. Its targets include government institutions, critical infrastructure, political figures, and entities linked to NATO defense sectors. The malware is typically distributed via phishing emails containing malicious attachments. Command-and-control domains are hosted by providers such as LuxHost and Aeza, both known for offering bulletproof hosting services.
At the core of the attack lies a DLL library that downloads additional modules through the InterPlanetary File System (IPFS), enabling the execution of commands, deployment of the final payload, and establishment of persistent communication with the control server. The concluding stage involves downloading supplementary components designed to exfiltrate data from browsers and various other sources.
RomCom also gathers detailed system information, including time zone settings, to align its activity with the victim’s working hours or to bypass time-based defenses. Additionally, the trojan modifies the Windows Registry, employs COM object hijacking for persistence, maps out the network and Active Directory environment, moves laterally through the infrastructure, and exfiltrates sensitive content such as documents and Outlook backups.
The attackers control compromised machines through a dedicated panel that provides system insights and supports the execution of over 40 distinct commands. According to PRODAFT, Nebulous Mantis follows a multi-phased intrusion strategy encompassing initial compromise, malware deployment, system persistence, and data exfiltration.
This revelation comes shortly after PRODAFT also disclosed operations linked to another group — Ruthless Mantis — known for employing double extortion tactics and maintaining affiliations with affiliate programs such as Ragnar Locker and INC Ransom.
The group’s leader, identified as LARVA-127, utilizes both legitimate and proprietary tools throughout every stage of the attack — from initial breach to the use of post-exploitation frameworks like Brute Ratel and Ragnar Loader. The group comprises both seasoned operators and emerging recruits, allowing it to scale its campaigns rapidly and increase the efficiency of its intrusions.


