The ONEKEY Research Lab team has uncovered a critical vulnerability in the firmware of MeteoBridge—a compact device designed to connect personal weather stations to public services such as Weather Underground. The flaw affects firmware versions 6.1 and below, allowing unauthenticated attackers to execute arbitrary commands with root privileges. Designated as CVE-2025-4008, the vulnerability carries a CVSS severity score of 8.7.
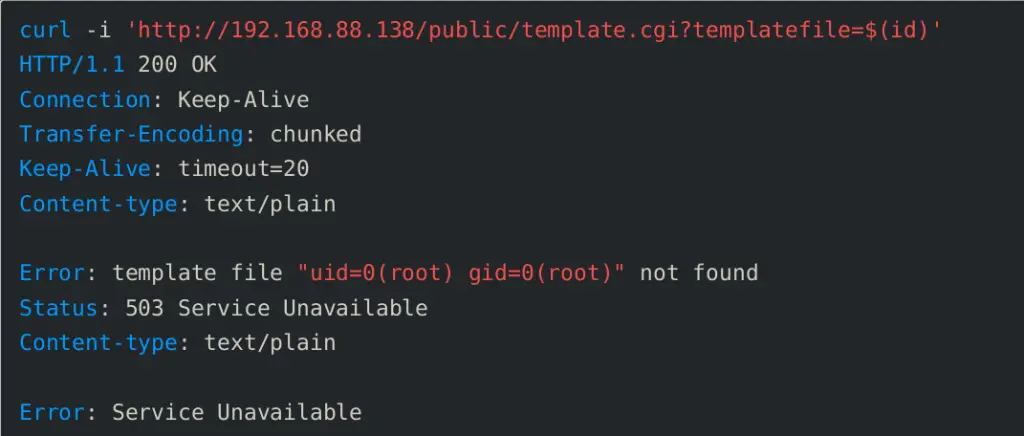
The root of the issue lies in the CGI script /cgi-bin/template.cgi, which processes input directly from the $QUERY_STRING variable without any form of sanitization and passes it directly into an eval function—a practice long condemned as catastrophic from a security standpoint. Any request in the form of http://[target]/public/template.cgi?templatefile=$(command) can lead to arbitrary code execution.
Exacerbating the situation is a misconfiguration in the uhttpd web server: while the /cgi-bin directory requires authentication, the vulnerable script is also mirrored in the /public folder, which does not enforce any authentication. As a result, the attack can be carried out without the need for login credentials.
According to data from Shodan, between 70 and 130 such devices are discoverable online, highlighting the high likelihood of real-world exploitation. The risk is particularly acute in social engineering scenarios: an attacker could embed a malicious link within an image or HTML element, triggering unauthorized code execution upon user interaction.
Exploitation is trivial—requiring nothing more than a single HTTP GET request. ONEKEY demonstrated how to leverage curl to send a command and receive its output directly in the response body, streamlining attack automation and significantly enhancing exploitation efficiency.
The vulnerability was identified using a newly integrated static analysis module for Bash scripts within the ONEKEY platform. According to the research team, the discovery underscores the power of automated solutions in firmware auditing.
The disclosure process was far from seamless: MeteoBridge’s administrators initially deleted the vulnerability report and banned the researcher’s account from the forum. However, following persistent disclosures—some involving Germany’s Federal Office for Information Security (BSI)—the developer eventually released a patch on May 14, 2025.
Users are strongly advised to upgrade immediately to version 6.2. Organizations operating in the IoT space should consider adopting automated firmware verification tools—this incident demonstrates how inconspicuous, yet perilous, such vulnerabilities can be.
The MeteoBridge case underscores a sobering truth: even a seemingly innocuous weather gateway can serve as an entry point for cyberattacks. As the Internet of Things continues to weave itself into daily life, the security of these “invisible” firmware layers becomes ever more critical.


