Cybersecurity researchers have uncovered a large-scale, meticulously orchestrated phishing campaign aimed at cryptocurrency theft. Over the span of several years, threat actors succeeded in building a resilient infrastructure comprising more than 38,000 subdomains designed to target digital wallet owners. The investigation, conducted by SentinelOne and Validin, has been codenamed FreeDrain.
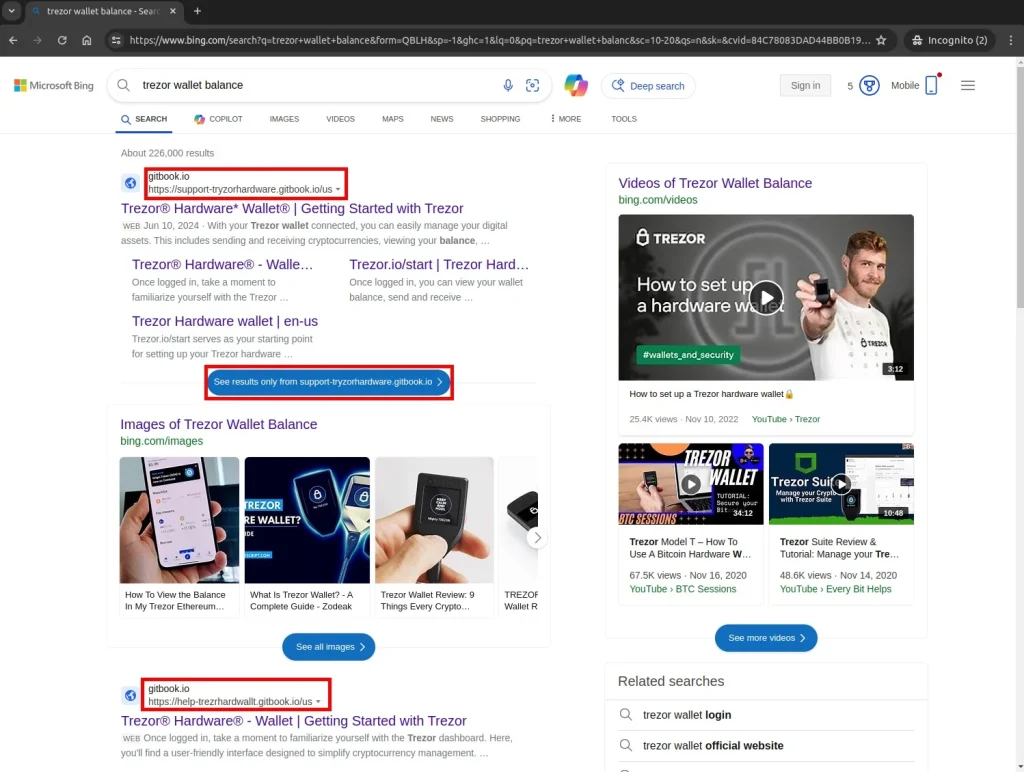
At the core of the attack lies a sophisticated blend of search engine manipulation, abuse of free hosting platforms such as gitbook.io, webflow.io, and github.io, and a multi-layered redirection system. Users searching for information related to their crypto wallets—for example, queries like “Trezor wallet balance”—were lured into counterfeit websites that closely mimicked legitimate wallet interfaces. The ensuing interaction followed one of three scenarios: redirection to a genuine site, diversion to an intermediary page, or presentation of a full-fledged phishing replica prompting the user to enter their seed phrase.
Every component of the attack was crafted with seamless precision—from the visual design to the perceived trustworthiness of the hosting platforms. Upon submission of the seed phrase, the automated infrastructure would drain the victim’s wallet almost instantaneously. Some of the fake sites were generated using large language models such as GPT-4o, enabling attackers to mass-produce textual content without human involvement.
A notable indicator of the campaign’s origin was its activity pattern: GitHub commits were predominantly made on weekdays during IST business hours, pointing to operators following a conventional work schedule aligned with Indian Standard Time.
To boost the visibility of their malicious pages in search results, attackers employed spamdexing—flooding poorly protected websites with thousands of fake comments containing links to phishing traps. Similar tactics were documented as early as 2022 by researchers at Netskope, where attackers impersonated brands like MetaMask, Phantom, Bitbuy, Coinbase, and Trezor.
FreeDrain stands as a textbook example of scalable phishing operations built on free infrastructure and engineered for resilience. Its distributed architecture and rapid adaptability to takedowns ensure the campaign’s persistence and ease of reconstitution.
In parallel, Check Point Research reported renewed activity from another theft mechanism—Drainer-as-a-Service, known as Inferno Drainer. Although this infrastructure was officially “shut down” in 2023, recent attacks suggest the service remains operational. It employs disposable smart contracts, encrypted configurations stored on the blockchain, and proxy networks to bypass security systems and blacklists.
Victims are lured via Discord, where outdated invitation links are hijacked, and OAuth2 authorization is used for obfuscation. Users are led to a fake bot and subsequently to a phishing page where they are prompted to sign a malicious transaction. According to researchers, between September 2024 and March 2025, Inferno Drainer compromised more than 30,000 cryptocurrency wallets, resulting in losses exceeding $9 million.
Additionally, Bitdefender researchers identified a malvertising campaign leveraging Facebook* ads that impersonated prominent crypto exchanges such as Binance, Bybit, and TradingView. These ads directed users to malicious websites posing as official download pages. Depending on whether the visitor was a genuine user or an analysis system, the site would serve either harmful content or a benign placeholder. The installer displayed a fake login screen through the msedge_proxy.exe browser process, while covertly launching background components ranging from data collection to extended sleep functions—delaying activity by hundreds of hours in the presence of sandbox environments.
Together, these findings underscore the remarkable sophistication and resilience of modern phishing operations—from link spoofing and AI-generated content to the emulation of trusted services and evasion of analytical detection.


