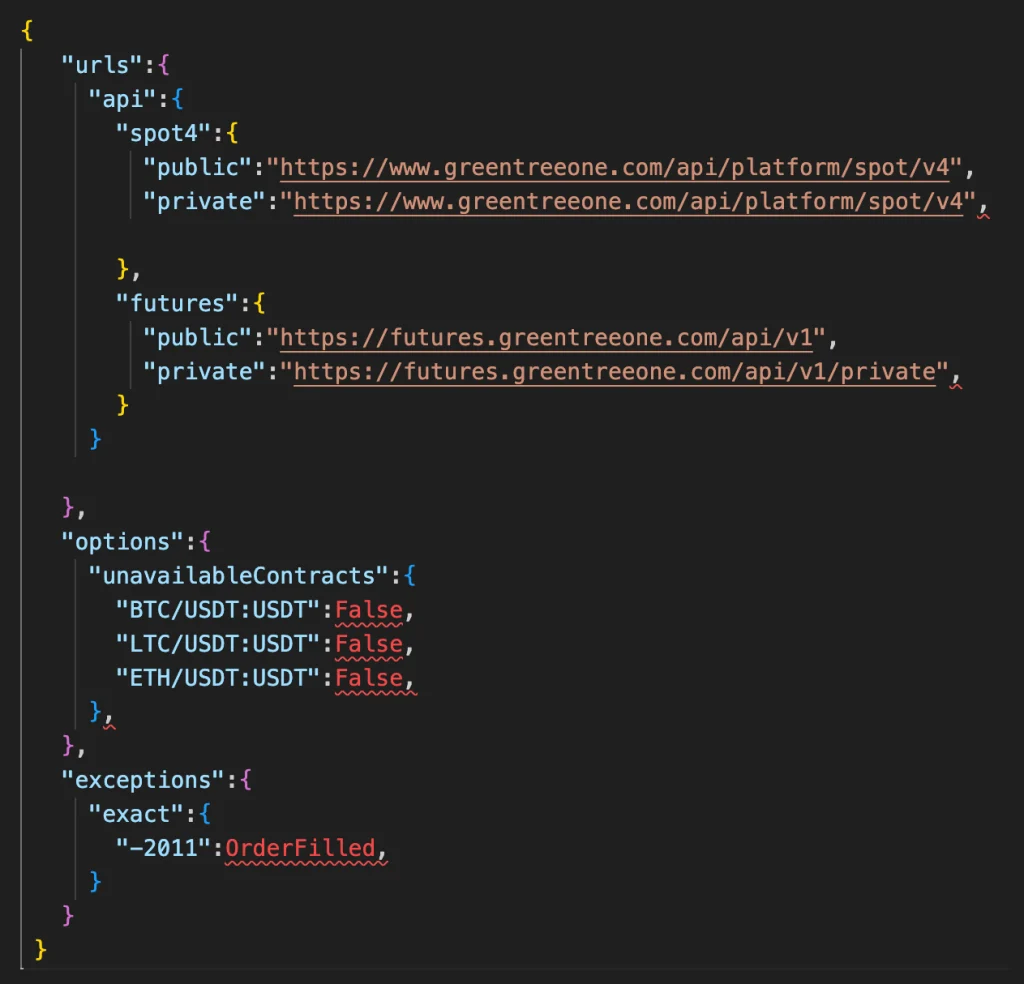
The JSON settings downloaded by the malicious package
Researchers at JFrog have uncovered a malicious package hosted on the official Python Package Index (PyPI). Its primary objective was to intercept trading orders submitted to the MEXC cryptocurrency exchange, redirect them to an external server, and exfiltrate user tokens. The package, deceptively named “ccxt-mexc-futures,” masqueraded as an extension of the widely used “ccxt” library, which facilitates automated interactions with various cryptocurrency platforms.
At first glance, the package purported to enable futures trading support on the MEXC platform. In its README file, the threat actors falsely claimed that their code enhanced the existing functionality of ccxt. However, deeper analysis revealed that the package maliciously replaced critical API methods—including contract_private_post_order_submit and contract_private_post_order_cancel—and introduced a new method titled spot4_private_post_order_place.
These manipulations enabled the attackers to deceive developers: API calls intended to open, cancel, or place orders on MEXC were, in reality, being silently rerouted to a rogue server. Additional modifications were made to key functions such as describe, sign, and prepare_request_headers, present in the original library. This allowed the malicious code to execute locally, retrieving configurations from a spoofed domain: v3.mexc.workers[.]dev.
This domain, crafted to resemble an authentic MEXC resource, funneled traffic to greentreeone[.]com, a server fully controlled by the attackers. As a result, all trading activity and transmitted API keys were funneled directly to the malicious infrastructure, granting attackers full control over users’ trading operations and sensitive data.
Upon discovery, the package was promptly removed from PyPI. However, download statistics from pepy[.]tech indicate that it had already been downloaded at least 1,065 times. Developers who integrated “ccxt-mexc-futures” into their projects are strongly urged to delete it immediately and revoke all associated API keys and tokens to prevent further compromise and unauthorized access.
This incident is emblematic of a growing trend involving the deployment of counterfeit packages across ecosystems such as npm, PyPI, Go, and Maven. Threat actors increasingly embed remote shells into these packages, securing persistent access and enabling covert data exfiltration. According to cybersecurity firm Socket, such tactics often evade detection by mimicking legitimate software dependencies.
A further cause for concern lies in the vulnerabilities introduced through the software supply chain by generative AI. Large language models may “hallucinate” non-existent package names and suggest them to developers. Exploiting this, malicious actors register the suggested names and populate them with harmful code—a technique now known as Slopsquatting.
A recent study revealed that such fabricated packages account for up to 5.2% of suggestions by commercial AI models and 21.7% by open-source models. In total, more than 205,000 unique, AI-generated names have been registered and used maliciously, underscoring the vast scale of the threat and the urgent need for vigilance within the development community.


