Malicious actors have once again targeted the npm ecosystem, this time through a package named “os-info-checker-es6”, which masquerades as a utility for retrieving operating system information. This deceptive appearance allowed the malicious code to evade detection until it was uncovered by researchers at Veracode and Aikido.
The package was first published to the repository on March 19, 2025, and has since been downloaded over 2,000 times. It was uploaded by a user under the alias “kim9123”, who also released another package, “skip-tot”, which listed “os-info-checker-es6” as a dependency. That package was downloaded 94 times. In its initial iterations, no malicious behavior was observed—the first five versions appeared benign, with no signs of data exfiltration or suspicious activity.
However, starting with the version released on May 7, the preinstall.js file began to exhibit obfuscated content. The malicious code was concealed using a novel steganographic technique that employed Unicode characters from the Private Use Area. This tactic effectively hid instructions to initiate the next stage of the attack chain.
Security is not optional—it is imperative.
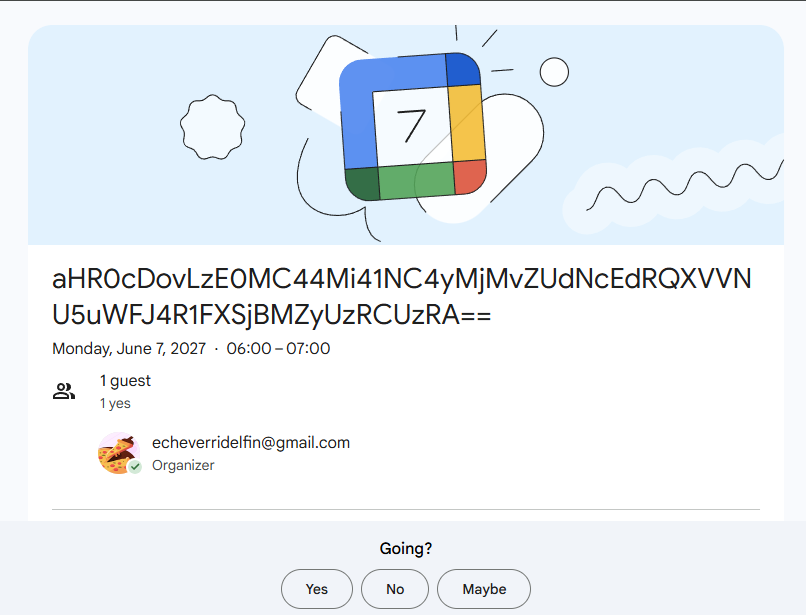
In the second stage, the attack leveraged a Google Calendar link disguised as a shortened URL—“calendar.app[.]google/”. The event title contained a Base64-encoded string, which, when decoded, revealed the IP address of a remote server: “140.82.54[.]223”. In this way, Google Calendar functioned as a covert communication channel to the command-and-control infrastructure, significantly complicating early detection and blocking efforts.
At present, no additional payloads have been identified. This may indicate that the operation is still under development, has already concluded, or is triggered only under specific conditions. It is also possible that the C2 server selectively responds only to designated targets.
Beyond “skip-tot,” three additional npm packages—“vue-dev-serverr,” “vue-dummyy,” and “vue-bit”—list “os-info-checker-es6” as a dependency. According to researchers, these packages are likely part of the same malicious campaign. Analysis of the commit history for “os-info-checker-es6” reveals a gradual shift from benign test uploads to a fully developed, multi-stage malicious framework.
Veracode underscores that the use of legitimate services like Google Calendar as a launch point for malicious code represents a sophisticated evasion technique that undermines traditional security systems and filtering mechanisms. Experts at Socket echoed this view, highlighting six prevalent attacker techniques in 2025: typosquatting, manipulation of Go repository caches, obfuscation, multi-stage payload delivery, slopsquatting, and the exploitation of legitimate developer tools.
To counter such threats, security professionals recommend vigilant monitoring of package behavior: the appearance of suspicious postinstall scripts, unauthorized file modifications, and unsolicited outbound connections. It is also critical to rigorously audit third-party dependencies, lock version numbers, perform both static and dynamic code analysis, and maintain close scrutiny of CI/CD logs.


