The threat of software supply chain compromise has once again resurfaced: the Ripple-recommended library “xrpl.js”, used for interacting with the XRP blockchain via JavaScript, has been compromised. Malicious code was injected through official updates published on NPM, enabling attackers to exfiltrate seed phrases and private keys from cryptocurrency wallets.
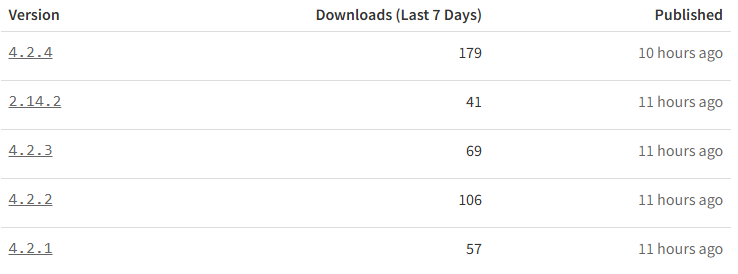
The issue affects versions 2.14.2, 4.2.1, 4.2.2, 4.2.3, and 4.2.4, published on April 21 between 4:46 PM and 5:49 PM EST. Although these compromised versions account for only 452 downloads, the scale of risk is far more significant — in the past week alone, the library was downloaded over 140,000 times, suggesting it may have been widely used to manage numerous wallets.
Analysis revealed that a new function, checkValidityOfSeed, had been appended to the /src/index.ts file. While it appeared to perform benign data validation, it in fact transmitted private keys, mnemonics, and seed phrases via HTTP POST requests to a domain under attacker control. To evade detection, the traffic was disguised with a forged User-Agent header labeled “ad-refferal,” mimicking advertising traffic.
Research conducted by Aikido confirmed that this malicious function was invoked from multiple areas within the codebase, enabling a silent and widespread leak of sensitive information without the developers’ knowledge. This exfiltrated data allowed attackers to import wallets onto their own systems and drain them instantly.
The compromise was limited to NPM releases — no traces of malicious commits were found in the GitHub repository. This indicates the tampering occurred either during the publishing process or via stolen credentials belonging to a Ripple-associated developer. The attack is a textbook case of a software supply chain breach, akin to recent incidents involving Ethereum and Solana libraries.
All compromised versions have now been removed from NPM, and a secure release, version 4.2.5, is available for installation. The XRP Ledger Foundation, which maintains the library, strongly urges all users to immediately upgrade to the latest version, regenerate their private keys, and disable master keys in the event of suspected compromise. Comprehensive instructions for these actions are available in the official XRPL documentation.
This incident serves as a sobering reminder of the inherent fragility of even the most trusted and widely adopted open-source tools. Any update — even one delivered through an official channel — can become an attack vector if control over a developer’s account is lost.


