A phishing campaign disguised as official Microsoft system alerts has shifted its focus and is now targeting macOS users. Initially aimed at Windows device owners, the campaign altered its vector in early 2025, as observed by researchers at LayerX, a platform specializing in browser security. The operation had been gaining momentum throughout 2024, reaching a peak in its final months.
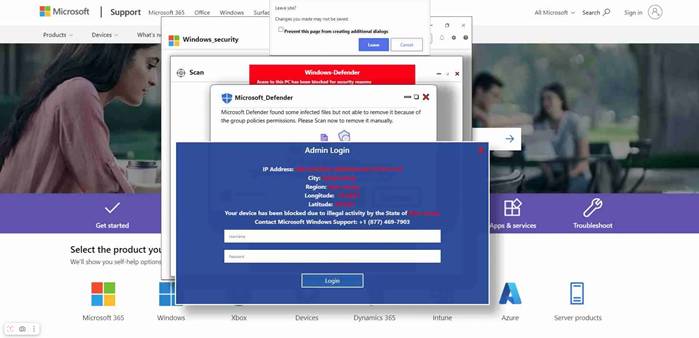
The early waves of the attack relied on presenting potential victims with counterfeit websites crafted to mimic legitimate Microsoft security warnings.
Users were informed that their device had allegedly been “locked” and “compromised,” prompting them to enter their Windows credentials. Simultaneously, the browser would appear to freeze, heightening a sense of urgency and panic. This psychological manipulation often led victims to surrender their information hastily.
What made the campaign particularly insidious was the use of subdomains on the windows.net platform—domains owned by Microsoft itself. This lent a false sense of authenticity, successfully deceiving even cautious users. Additionally, the attackers exploited legitimate hosting services to circumvent traditional filters and security measures designed to block suspicious domains.
An extra layer of obfuscation was achieved through the rapid rotation of subdomains. Each one remained active only briefly before being replaced, allowing the campaign to maintain its momentum even when specific URLs were flagged and blacklisted. According to LayerX, this tactic enabled the attackers to sustain a high level of operational effectiveness over time.
By early 2025, however, attacks on Windows users had declined by nearly 90%, a drop attributed by LayerX to improved defenses in mainstream browsers. Chrome and Firefox enhanced their phishing protection mechanisms, while Microsoft Edge introduced a new feature to counter “scareware”—software designed to simulate threats and coerce users into action.
With diminishing returns on the Windows front, the perpetrators pivoted toward Apple device owners. The campaign adopted a new aesthetic tailored to macOS while retaining its core structure: counterfeit system warnings and UI freezes intended to provoke user interaction. LayerX notes that despite the change in appearance, the essence of the attack remains the same.
An analysis of the campaign’s infrastructure and distribution methods suggests that the current phase is merely a prelude to a renewed offensive. Experts warn that a resurgence of attacks is imminent, particularly in light of newly identified vulnerabilities within Microsoft’s latest security features. The attackers’ use of a scalable, resilient, and adaptive architecture underscores a highly sophisticated and coordinated operation.
At present, the specific macOS browsers targeted have not been disclosed, nor have concrete figures on affected users been released. However, based on the structure and history of the campaign’s previous phases, it is presumed that all major browsers lacking supplemental security extensions remain at risk.
The identity of the group orchestrating the campaign has yet to be determined. No domains or registered accounts associated with the operation have been named. Nonetheless, the strategic deployment of legitimate tools and infrastructure signals a campaign meticulously designed for long-term persistence.


