The research team at CYFIRMA has uncovered a new strain of malware — Lyrix Ransomware — developed in Python and compiled using PyInstaller to operate as a standalone executable on Windows. This compilation method bundles all dependencies into a single file, significantly streamlining the malware’s distribution. Lyrix employs robust encryption techniques and sophisticated evasion methods, rendering it particularly dangerous to targeted systems and challenging to eradicate. Its activity was first observed on April 20, 2025.
According to experts, the malware conceals its malicious behavior, bypasses signature-based defenses, encrypts user files, and threatens to leak data. Each encrypted file is appended with the extension “.02dq34jROu,” while the corresponding encryption keys are stored in the ProgramData system directory under matching filenames. Decryption without the attackers’ private key is impossible.
Lyrix Ransomware is deployed under the guise of a file named Encryptor.exe (20.43 MB in size), utilizing the standard Win32 EXE format with an “MZ” header. It lacks a digital signature, complicating detection and blocking by antivirus solutions. Upon execution, the malware scans common user directories — Downloads, Documents, Desktop, Pictures, Music, and Videos — selectively encrypting widely used file formats such as DOCX, PDF, XLS, and JPG. Executable files, DLLs, and shortcuts are deliberately excluded to preserve system functionality and delay detection.
To manage and store encryption keys, Lyrix generates a unique AES key and secures it using a built-in RSA public key. It then deletes all system shadow copies using the commands vssadmin delete shadows /all /quiet and wmic shadowcopy delete, effectively thwarting data recovery attempts. The ransomware further alters the Windows boot configuration, disabling error messages (bcdedit /set {default} bootstatuspolicy ignoreallfailures) and deactivating Windows Recovery Environment (bcdedit /set {default} recoveryenabled no).
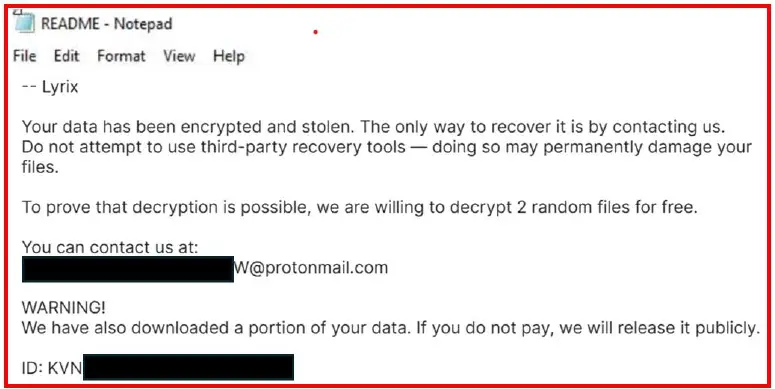
After encryption is complete, a “Readme.txt” file is placed in each affected directory, containing ransom instructions. The message claims that the victim’s data has been both exfiltrated and encrypted. As proof, the attackers offer to decrypt two files free of charge. The threat of data exposure is used as additional leverage. The contact address provided is a ProtonMail account registered in April 2025.
Technical analysis revealed that Lyrix incorporates an arsenal of anti-virtualization and anti-analysis techniques, including VirtualProtect, Sleep, GetCurrentProcess, TerminateProcess, GetStartupInfoW, GetWindowLongPtrW, and ShutdownBlockReasonCreate. These measures are designed to obscure malicious activity and complicate automated forensic investigation. Within the MITRE ATT&CK framework, documented tactics span from script execution and process injection to artifact concealment and credential manipulation.
To mitigate this threat, specialists recommend the following measures:
- Block execution of executables from temporary directories using AppLocker or SRP;
- Restrict access to critical utilities such as
vssadmin,wmic, andbcdedit; - Enhance email security and attachment filtering mechanisms;
- Deploy modern EDR solutions capable of detecting mass file renaming or encryption activities;
- Conduct regular employee training, including simulated phishing campaigns;
- Maintain and routinely test incident response plans;
- Immediately isolate infected systems upon detecting suspicious activity;
- Preserve forensic artifacts and refrain from deleting encrypted files;
- Avoid paying ransom, as it offers no guarantee of data recovery.
Additionally, it is advised to utilize YARA rules and Indicators of Compromise (IoCs) provided by CYFIRMA to fine-tune detection systems. Emphasis is placed on maintaining frequent backups stored securely and offline to ensure resilience against data loss.


