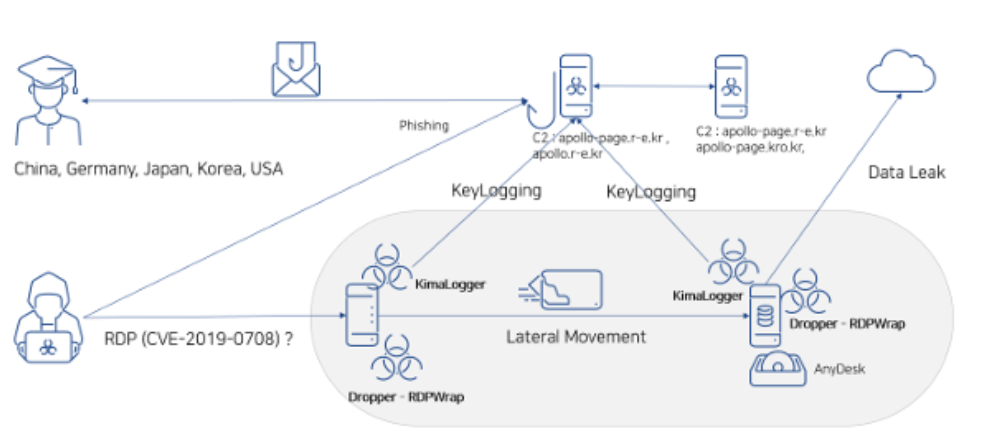
A cybercriminal campaign linked to the North Korean threat group Kimsuky has once again drawn the attention of security researchers due to its exploitation of the long-known yet persistently dangerous BlueKeep vulnerability (CVE-2019-0708) in Windows Remote Desktop Services. Although Microsoft patched this flaw in 2019, attackers continue to discover systems that remain unprotected, using the exploit as an initial access vector.
Analysts at the South Korean cybersecurity firm AhnLab have designated this attack as Larva-24005. In several documented incidents, Kimsuky actors gained control over targeted machines by issuing specially crafted RDP requests, allowing them to execute arbitrary code on remote systems without prior authentication. While an RDP vulnerability scanner was discovered on some compromised devices, there is currently no conclusive evidence of its active use.
In addition to BlueKeep, the attackers also leveraged another aged vulnerability — CVE-2017-11882 — associated with the Equation Editor component in Microsoft Office. By distributing malicious emails with embedded files, they bypassed security mechanisms through social engineering to infiltrate target systems.
Upon gaining access, the attackers deployed the MySpy malware, designed to collect environmental intelligence about the host system. They also installed the RDPWrap utility to enable or modify remote access capabilities. System configurations were further altered to establish a persistent communication channel for ongoing control of the infected machines.
The final phase of the operation involved deploying keyloggers KimaLogger and RandomQuery, which recorded every keystroke. This enabled the adversaries to intercept credentials, messages, and other sensitive information vital to their broader campaign objectives.
The campaign has shown heightened activity in South Korea since October 2023, targeting organizations in the energy, finance, and software sectors. Entities in Japan were also impacted, and the campaign’s reach spans globally — from the United States and China to Poland and South Africa.
The persistent exploitation of vulnerabilities long since patched underscores systemic issues in software updating and vulnerability management within affected infrastructures. Such oversights render even outdated exploits potent weapons in the hands of seasoned adversaries like Kimsuky.


