UAC Bypass Done by Katz InfoStealer Malware
Amid intensifying competition among cybercriminals for the theft of confidential data, a new player emerged in 2025—Katz Stealer. This Malware-as-a-Service (MaaS) platform offers capabilities on par with full-fledged cyber-espionage frameworks, now accessible to virtually anyone—for a price.
Katz Stealer exemplifies a comprehensive and sophisticated approach to data exfiltration, seamlessly blending rapid information filtering with an intricate system of obfuscation and a modular, adaptive architecture for payload delivery. It is chiefly propagated through phishing emails and counterfeit software installers, though its ingenuity extends far beyond these vectors.
Upon execution, the infection unfolds in multiple phases, each meticulously designed to evade conventional antivirus mechanisms. It begins with GZIP archives containing JavaScript droppers cloaked through common obfuscation tactics such as type coercion and polymorphic string concatenation. The script discreetly triggers PowerShell to retrieve what appears to be a benign image from Archive.org—yet hidden within lies base64-encoded malicious code embedded via steganography.
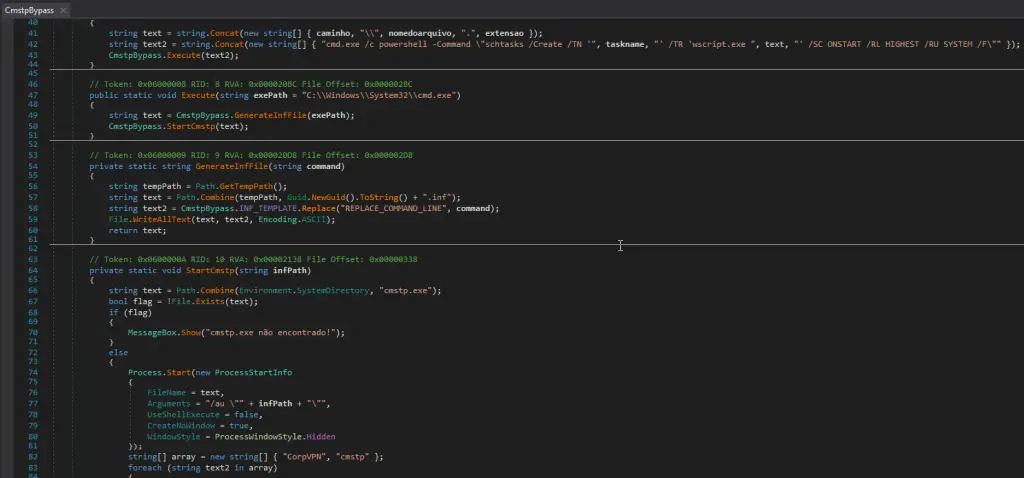
According to a report by Picus Security, the next phase involves a .NET-based loader that performs geofencing and virtual environment checks to avoid activation within sandbox or analysis environments. The malware then escalates privileges by exploiting cmstp.exe to bypass User Account Control (UAC).
The final payload is injected into legitimate system processes such as MSBuild.exe using Process Hollowing, enabling stealth execution under the guise of trusted operations. Simultaneously, a connection is established with the command-and-control (C2) server, observed at 185.107.74[.]40.
At this stage, Katz Stealer initiates full-scale surveillance operations. It does not merely extract saved credentials from browsers—it decrypts master keys from Chromium’s “Local State” and siphons session data from Firefox profiles. In total, it targets 78 different browsers, including obscure forks of mainstream engines.
Particular emphasis is placed on cryptocurrency wallets. The malware actively searches for desktop clients like Exodus and browser-based extensions such as MetaMask. All harvested assets are prepared for exfiltration via TCP or HTTPS, with traffic marked by a distinctive User-Agent header: katz-ontop, making it identifiable to advanced network detection systems.
Going further, Katz Stealer injects malicious code into Discord’s JavaScript bundles, effectively weaponizing the messenger as a remote command execution platform. Upon the next launch, Discord becomes a covert gateway for subsequent intrusions, aided by auto-start behavior.
To frustrate forensic efforts, the malware purges all temporary files post-execution. Its MaaS infrastructure allows criminals to generate tailored builds through an intuitive web interface—choosing components, defining targets, and exporting stolen data, all within a few clicks.
This suite of capabilities elevates Katz Stealer far beyond the realm of typical malware. It represents a formidable threat—demanding not only heightened vigilance but a fundamental reassessment of endpoint defense strategies and network security paradigms.


