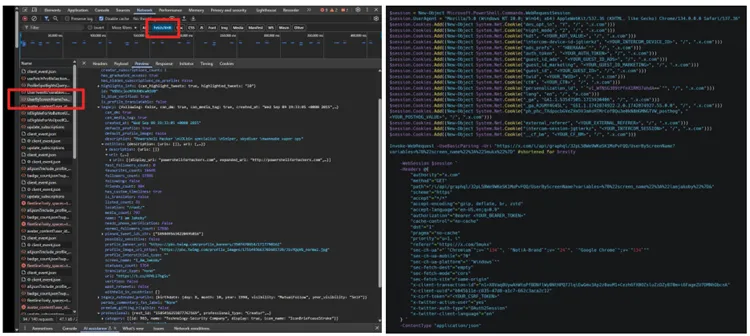
Despite the limitations imposed by Twitter’s official API, users continue to discover alternative methods for extracting internal data about their own accounts and others’. One such technique has sparked considerable discussion within the community after a user revealed an intriguing observation: by utilizing browser developer tools, it is possible to access a trove of hidden information otherwise unavailable via the API.
By opening the developer tools and filtering network requests by fetch/XHR, one can locate a response labeled UserByScreenName, which returns a comprehensive dataset for any public account. When this request is copied as a PowerShell command, current authorization and CSRF tokens are automatically embedded, allowing the query to be executed without any additional configuration.
The resulting payload provides far more than just standard profile attributes—it includes sensitive metadata such as whether the user is flagged as NSFW, subject to regional restrictions, or designated as a “protected” account. While the latter designation remains ambiguous, it may indicate elevated privacy settings or internal moderation status.
What drew particular attention was the access to direct messages (DMs). Using similar network calls, one can retrieve the full structure of personal messages—from unread threads and reactions to granular metadata. Notably, this functionality isn’t confined to active accounts—data from blocked or deleted users, if previously connected to the current session, can also be surfaced.
Although no overt vulnerabilities with immediate security implications have yet been identified, the sheer volume of accessible data raises concerns. Especially troubling is that much of this information is undocumented and inaccessible through official API channels. This suggests that Twitter’s internal services transmit far more data than is commonly understood.
At present, these discoveries highlight the nuances of the client-backend interaction more than they expose critical security flaws. However, the original researcher has pledged to utilize the HackerOne bug bounty platform should any actual vulnerabilities emerge. Until then, these revelations serve as a compelling testament to how much can be uncovered about the platform without formal access.


