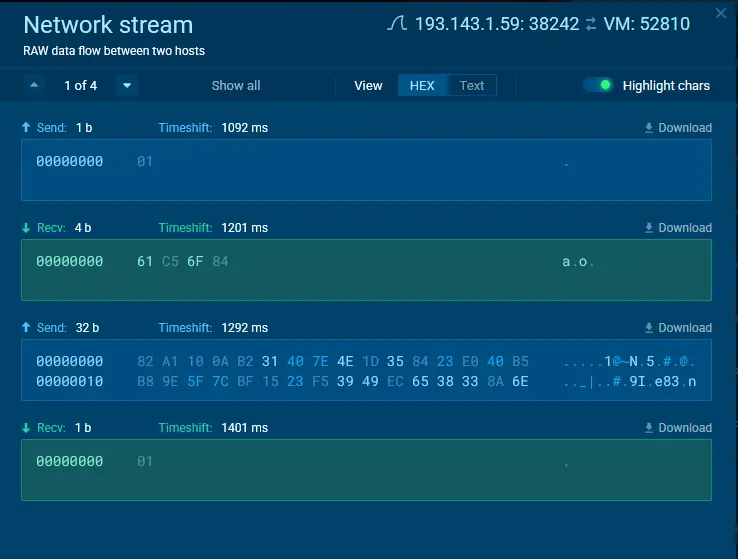
C2 communication shown in ANY.RUN’s Interactive Sandbox
In September, cybersecurity experts at NSFOCUS identified the emergence of a new botnet dubbed GorillaBot. Built upon the aging codebase of Mirai, it managed to orchestrate over 300,000 attacks across 100 countries within just three weeks. Despite its roots in a well-worn architecture, the malware has evolved with sophisticated obfuscation techniques, authentication protocols, and camouflage strategies, rendering it notably difficult to detect and analyze.
According to researchers at ANY.RUN, the core functionality of GorillaBot relies on direct TCP communication with its command-and-control (C2) server. Instead of conventional HTTP requests, it employs raw TCP sockets, encrypting data with a proprietary cipher reminiscent of XTEA. IP addresses of C2 servers are dynamically decrypted, effectively evading static analysis methods.
Particular emphasis has been placed on anti-analysis defenses. The malware inspects the /proc/self/status file to detect the presence of debugging tools and reacts to the SIGTRAP signal by terminating execution. It further assesses its runtime environment by checking for the /proc virtual filesystem and analyzing /proc/1/cgroup for container signatures such as Kubernetes. If such environments are detected, the malware aborts its operation.
The authentication process with the C2 server begins with the exchange of specific tokens. The server initially sends a 4-byte value, which is combined with a 32-byte encrypted array, then hashed using SHA-256. The resulting digest is returned as proof of authenticity. A flag marked “01” from the server signals successful acceptance into the botnet.
Commands for attack are also transmitted in encrypted form. The packet structure includes a SHA-256 hash and the command itself, obfuscated using a basic Caesar cipher. After verifying the integrity of the message, the payload is passed to the attack_parse function—borrowed almost verbatim from the original Mirai—where an attack method is selected and execution is triggered.
Despite its reliance on legacy code, GorillaBot remains a formidable threat. Its incorporation of evasion mechanisms and unconventional C2 communication showcases a striking example of malware evolution.
GorillaBot is a testament to the reality that even well-documented malware strains can be resurrected with ingenuity and a few lines of modern code. In today’s threat landscape, dismissing such “revived” threats can prove more dangerous than ever.


