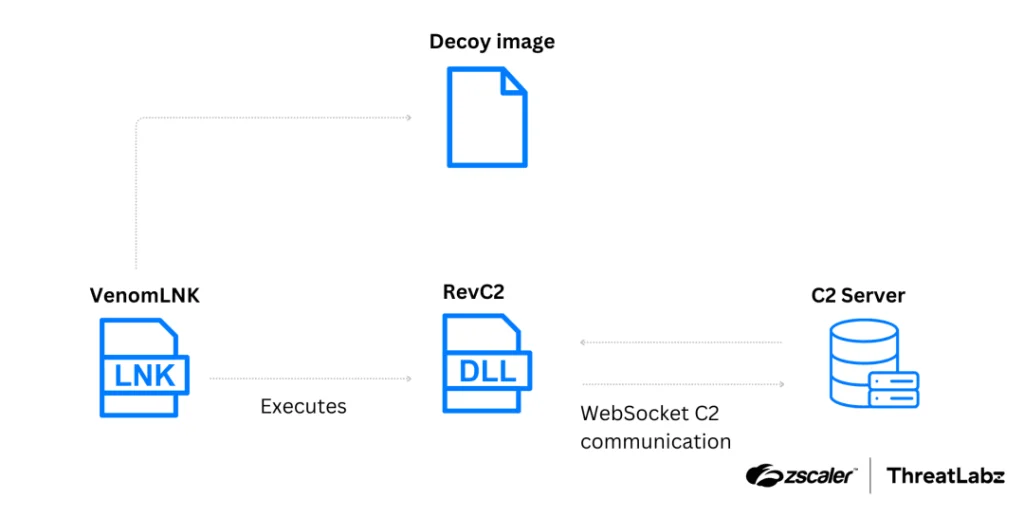
Recent Golden Chickens attack chain used to deliver RevC2 (Source: ZScaler)
Researchers at Insikt Group have uncovered two new digital tools circulating online, both designed to steal passwords and drain cryptocurrency wallets. These tools are attributed to the threat group known as Golden Chickens—also referred to as Venom Spider—which operates under the malware-as-a-service (MaaS) model.
The investigation, conducted between January and April 2025, identified ten samples of malware dubbed TerraStealerV2 and TerraLogger. Both are in their early stages of development and currently lack the stealth sophistication typically associated with Golden Chickens’ offerings.
The first tool, TerraStealerV2, targets Chrome’s “Login Data” database, extracting stored credentials and browser extension data. However, it is presently unable to bypass Chrome’s Application Bound Encryption (ABE)—a security mechanism introduced in mid-2024 that protects credentials at the system level. This limitation suggests either an unfinished development phase or reliance on outdated intrusion techniques.
Once deployed, TerraStealerV2 exfiltrates the harvested data via Telegram and a suspicious file-sharing domain, wetransfers[.]io. The malware is distributed in various formats, including LNK, MSI, DLL, and EXE files. To obscure its presence, it leverages legitimate Windows system utilities such as regsvr32.exe and mshta.exe. This tactic—abusing native administrative and script execution tools—enables it to evade endpoint security controls.
The second tool, TerraLogger, functions as a standalone keylogging module. It installs low-level input interceptors and stores the collected keystrokes locally, without built-in channels for command-and-control communication. Analysts believe this component is designed to be integrated into more complex malware frameworks.
Over its seven-year history, Golden Chickens has cultivated a broad clientele within the cybercriminal underground. Since 2018, their services have been employed by notorious groups including FIN6, Cobalt Group, and the Belarusian collective Evilnum. These actors have orchestrated devastating cyberattacks on the aviation sector, retail chains, and financial institutions across the globe, inflicting damages measured in the billions. Notable victims include British Airways, Newegg, and Ticketmaster UK.
Golden Chickens’ technical arsenal comprises a full suite of specialized tools. For initial system compromise, they use VenomLNK, a weaponized Windows shortcut. Deployment of additional modules is handled by the TerraLoader downloader. TerraTV enables session hijacking of TeamViewer. File encryption for extortion is executed via TerraCrypt. Reconnaissance and data destruction are performed by TerraRecon and TerraWiper, respectively. A key component of the toolkit is the more_eggs backdoor, alongside its lightweight JavaScript variant, Lite_more_eggs.
The threat response unit at eSentire has linked Golden Chickens to a hacker operating under the alias badbullzvenom. Investigators believe this moniker conceals a collective of threat actors based in Moldova and Montreal, Canada.


