The Berlin-based company thinkAwesome GmbH has uncovered a critical vulnerability in the widely used Unitree Go1 quadruped robots. The devices were found to contain a pre-installed and undocumented remote access service.
According to cybersecurity researchers Andreas Makris and Kevin Finisterre, any malicious actor could seize control of the robotic assistant and its onboard cameras. Exploitation requires only a single API key and default credentials—username “pi” and password “123.”
The robots, manufactured by Chinese firm Unitree Robotics, have gained popularity due to their affordability. The base Air model is priced at $2,500, while the Edu version—designed for universities and research institutions—costs around $8,500.
Despite hardware variations, all models run the same software. Higher-tier versions include a developer toolkit enabling both high- and low-level command control.
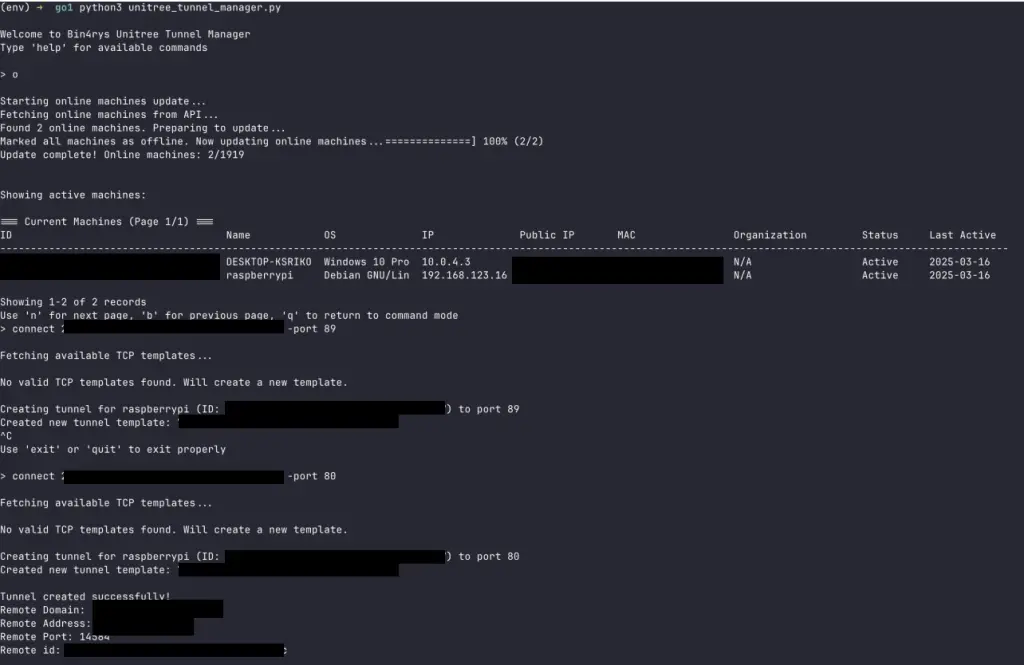
The investigation revealed that the robot’s “brain” is a Raspberry Pi single-board computer. Upon startup, it activates several proprietary services and, once connected to the internet, initiates a tunneling service called CloudSail, developed by Zhexi Technology.
CloudSail, primarily intended for the Chinese market, enables remote access to industrial and networked devices. It facilitates connections across segmented networks—even in the absence of port forwarding or in the presence of strict firewall rules—effectively circumventing such restrictions.
By obtaining the CloudSail API key, the researchers discovered 1,919 vulnerable devices, only two of which were active at the time. Using a custom tunnel management tool, they demonstrated the ability to connect to any operational unit, though they limited testing to their own robot.
A potential attacker could exploit this vulnerability to breach a local network. While the majority of affected devices are located in China, a significant number were found in other countries, including over a dozen universities across the United States, Canada, Germany, New Zealand, Australia, and Japan.
Experts believe the embedded backdoor was likely unintentional—more a result of poor code review and inadequate quality assurance than deliberate malice. Traces of legacy remote access implementations were found in the software.
Nonetheless, the threat posed by a pre-installed tunnel is real. Owners are urged to disconnect the robots from any networks and examine logs for signs of intrusion. Anyone with the API key can gain full control of the robot—manipulating its movements, accessing camera feeds, or connecting via SSH.
What makes the issue even more alarming is that the Unitree Go1 is often marketed for search-and-rescue missions and military applications. In certain contexts, such vulnerabilities could literally become a matter of life and death.
Although newer models like the Go2 and other devices from the manufacturer have yet to be analyzed, researchers caution that similar backdoors may well be present in those as well.


