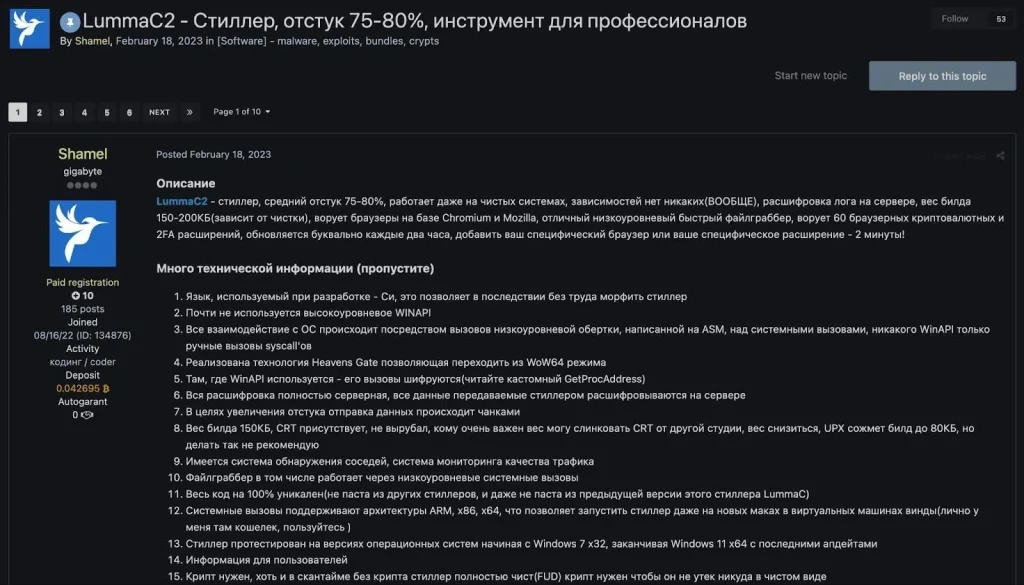
Exploit member Shamel posted the original sales thread for LummaC2
In the first half of May 2025, an international operation aimed at dismantling the infrastructure of Lumma Stealer—one of the most widely deployed infostealer malware services—achieved sweeping results. Through the coordinated efforts of multiple IT companies and law enforcement agencies, approximately 2,300 domains linked to this malicious ecosystem were seized, and portions of Lumma’s command infrastructure were dismantled across the globe.
A pivotal role in the takedown was played by Microsoft, which secured a court order to block the domains on May 13, 2025. Simultaneously, the U.S. Department of Justice took control of the Lumma Stealer command panel—a web interface used by cybercriminals to manage infected machines and traffic in stolen data. Europol, via its European Cybercrime Centre (EC3), and the Japan Cybercrime Control Center (JC3) provided technical assistance in decommissioning Lumma’s servers hosted in Europe and Japan.
According to Microsoft, between mid-March and mid-May 2025, over 394,000 Windows-based machines were identified as infected by Lumma. Following the intervention, the majority of communication channels between the malware infrastructure and its victims were successfully severed.
Cloudflare noted that Lumma’s infrastructure had extensively leveraged its services to obscure the true IP addresses of exfiltration servers. While the deactivated domains were taken offline, the malware still managed to bypass Cloudflare’s interstitial warning pages. In response, the company bolstered its defenses by implementing Turnstile, a verification mechanism designed to prevent automated traffic from evading such warnings.
This operation was the culmination of collaboration between Microsoft, Cloudflare, ESET, CleanDNS, Bitsight, Lumen, GMO Registry, and the international law firm Orrick.
Lumma Stealer (also known as LummaC2) is a malware-as-a-service (MaaS) infostealer, with monthly rental fees ranging from $250 to $1,000. It is capable of exfiltrating data from both Windows and macOS systems—including passwords, cookies, credit card details, cryptocurrency wallets, and browser histories. Among its primary targets are Google Chrome, Microsoft Edge, Mozilla Firefox, and other Chromium-based browsers.
The malware was propagated through malicious comments on GitHub, deepfake content websites, and malvertising campaigns. Once a system was infected, the data was aggregated, archived, and transmitted to command servers, then leveraged in subsequent attacks or sold on underground forums.
Lumma first appeared on cybercriminal platforms in December 2022 and quickly rose to prominence as one of the most prevalent infostealers. According to IBM X-Force’s 2025 report, the volume of data stolen by such tools increased by 12% over the past year, while the delivery of infostealers via phishing surged by 84%, with Lumma leading the pack.
Notable breaches involving Lumma-stolen credentials include incidents affecting PowerSchool, HotTopic, CircleCI, and Snowflake. Beyond corporate intrusions, compromised credentials were also used to manipulate BGP routing and disrupt RPKI configurations, as demonstrated in the hijacking of Orange Spain’s RIPE account.
Additionally, the FBI and CISA issued a joint advisory detailing technical indicators of compromise and attacker tactics associated with Lumma, enabling organizations to swiftly identify signs of infection and remediate vulnerabilities within their infrastructures.


