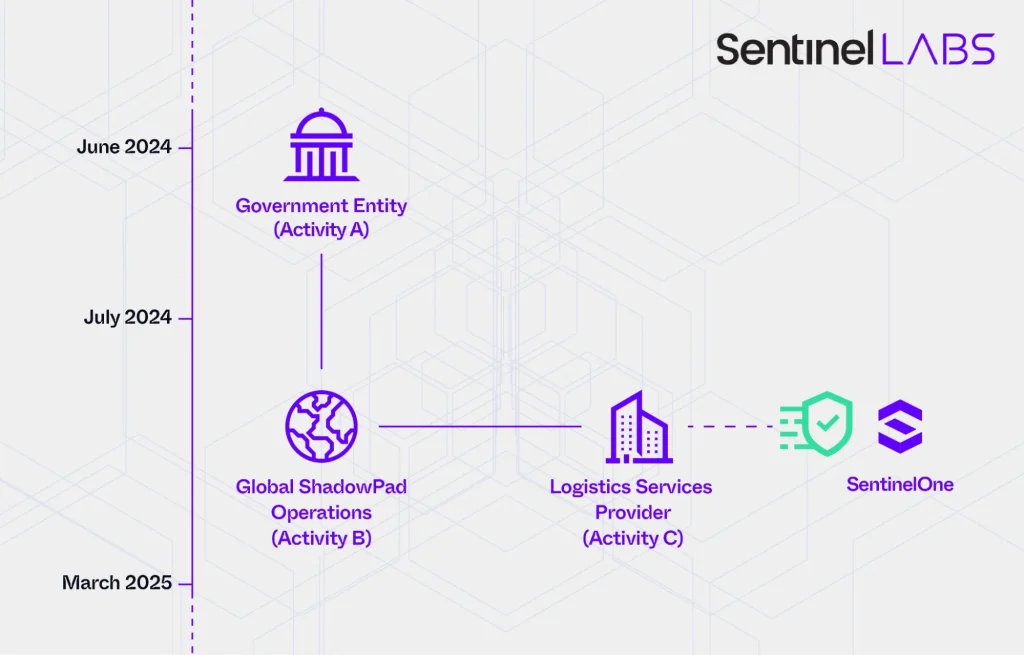
ShadowPad activity, June 2024 – March 2025
A far-reaching espionage campaign targeting the American cybersecurity firm SentinelOne has been revealed as merely one chapter in a broader series of interconnected attacks conducted against dozens of entities worldwide from mid-2024 through the spring of 2025. According to SentinelOne researchers Alexander Milenkoski and Tom Hegel, the list of victims includes not only private enterprises but also governmental institutions.
More than 70 organizations were targeted, including a governmental agency in South Asia, a prominent European media outlet, and various companies in the manufacturing, telecommunications, financial, and research sectors. Notably, an IT firm responsible for handling logistics for SentinelOne personnel was compromised in early 2025.
The perpetrators have been identified as cyber operatives with ties to China. Some of the operations have been attributed to the cluster known as PurpleHaze, which exhibits overlap with the activities of established espionage groups APT15 and UNC5174. The latter, tracked by Mandiant under the alias Uteus (or Uetus), has previously been involved in campaigns leveraging SAP NetWeaver vulnerabilities to deliver the GOREVERSE malware—a variant of GoReShell.
SentinelOne first observed signs of adversarial interest in April 2024, when its publicly exposed servers—intended to support operational functions—were probed by attackers. Analysts believe this reconnaissance phase signaled preparatory steps for subsequent intrusion attempts.
The investigation identified six distinct clusters of activity spanning from June 2024 to March 2025:
- Cluster A — Attack on a South Asian government agency in June 2024.
- Cluster B — A wave of intrusions targeting various global organizations from July 2024 to March 2025.
- Cluster C — Compromise of the IT company linked to SentinelOne logistics in early 2025.
- Cluster D — A second breach of the same South Asian agency in October 2024.
- Cluster E — Reconnaissance of SentinelOne servers in October 2024.
- Cluster F — Attack on a major European media conglomerate in September 2024.
The June 2024 assault involved the deployment of ShadowPad malware, obfuscated using the ScatterBrain tool. Analysts noted strong overlaps with previous campaigns where ShadowPad was utilized to deliver the NailaoLocker payload following the exploitation of vulnerabilities in Check Point gateways.
In October, the attackers revisited the South Asian government agency, implanting the Go-based GoReShell backdoor, which leverages SSH to communicate with compromised systems. The same malware strain was later employed against the European media company in September.
Strikingly, both attacks involved tools developed by The Hacker’s Choice (THC)—a group historically associated with ethical hacking. This marks the first documented instance of THC tools being used in operations that appear to be state-sponsored.
SentinelOne has categorized Clusters D, E, and F as components of the PurpleHaze operation. Available intelligence suggests that the group relied on ORB (Operational Relay Box) infrastructure, which has been previously linked to China. Initial access was reportedly achieved through exploitation of CVE-2024-8963 and CVE-2024-8190—vulnerabilities leveraged mere days before their public disclosure. Following initial compromise, it is believed UNC5174 may have handed off access to affiliated actors for follow-up operations.


