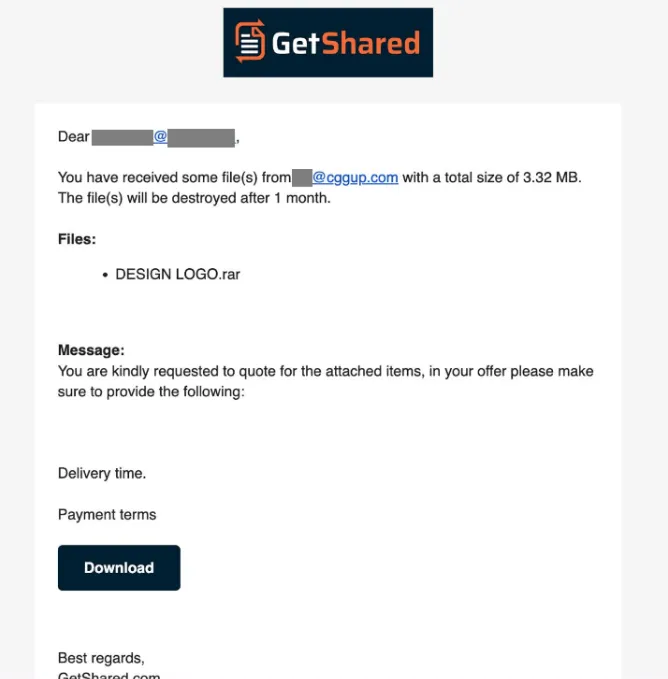
Experts at Kaspersky Lab have issued a warning regarding phishing attacks leveraging the legitimate file-sharing service GetShared. The threat came to light after a former employee of the company received a suspicious notification from the platform. The message included a link to an archive titled DESIGN LOGO.rar, accompanied by text that appeared to reference a business inquiry—specifically, a request for pricing, delivery timelines, and payment terms.
Upon receiving the email, the recipient refrained from clicking the link and forwarded the message to cybersecurity specialists. An investigation confirmed that the notification had indeed been dispatched via GetShared, a service increasingly exploited by cybercriminals to bypass email filters. Messages sent from GetShared closely resemble routine system notifications, containing a file name, a brief message, and a button to access the file. This makes it easier for attackers to disguise their activity as part of legitimate document workflows.
According to analysts, cybercriminals frequently turn to reputable platforms to circumvent email filters and security gateways. Services like Google Calendar, Dropbox, and now GetShared are co-opted for these purposes. As major platforms strengthen their filtering mechanisms and tighten registration requirements, malicious actors continue seeking alternative routes—and GetShared has become their latest focus.
The primary objective of such emails is to draw the recipient into a conversation. Even if the attached file does not contain malware, attackers hope to initiate communication that will later allow them to employ social engineering tactics. In some instances, the link may lead to a malicious file; in others, to a phishing site or an executable payload.
In the case involving the former employee, several red flags were noted. Most notably, there was a clear discrepancy between the file name and the content of the message—the message referenced products and pricing, while the file name suggested a design project. Additionally, the sender’s domain was suspicious; a simple lookup revealed its association with fraudulent activity.
Experts emphasize that the use of a third-party file-sharing service as a first point of contact—without prior business communication—is already cause for suspicion. No legitimate business partner would initiate file transfers through unsolicited notifications from an unfamiliar platform without prior agreement.


