A newly uncovered malicious campaign has emerged online, masquerading as legitimate antivirus software from Bitdefender. Threat actors created a fraudulent website under the domain “bitdefender-download[.]com,” luring users into downloading what appeared to be an official Windows version of the antivirus. Instead of genuine software, victims were served an archive containing the Venom RAT trojan — a remote access tool designed to steal sensitive information.
The deceptive “Download for Windows” button redirected users first to a Bitbucket repository and subsequently to an Amazon S3 storage instance. The Bitbucket account involved has since been taken down. The downloaded archive, named “BitDefender.zip,” included an executable file titled “StoreInstaller.exe,” which analysts found configured to deploy Venom RAT along with modules from the SilentTrinity and StormKitty frameworks.
Venom RAT is a variant of the well-known Quasar RAT and grants attackers persistent remote access to compromised systems. SilentTrinity facilitates post-exploitation operations, while StormKitty specializes in extracting passwords and cryptocurrency wallet data. Together, these tools enable seamless control over the infected environment, silently exfiltrating confidential assets.
According to DomainTools Intelligence, the infrastructure of the fake Bitdefender website shares temporal and technical characteristics with domains previously implicated in phishing attacks targeting users of the Royal Bank of Canada and Microsoft. This correlation suggests a unified operation or a single threat actor group orchestrating these campaigns with precision, motivated by financial gain.
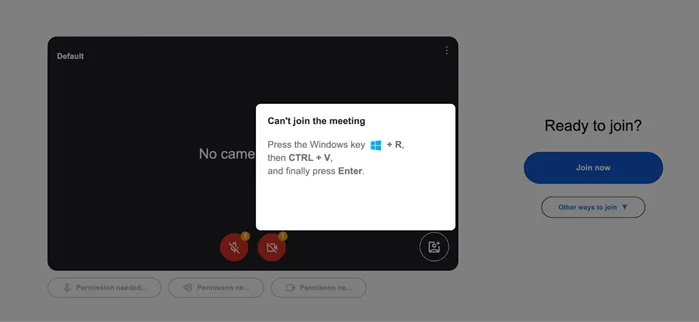
Simultaneously, researchers at Sucuri observed a separate wave of attacks impersonating Google Meet. Victims were presented with a counterfeit error message concerning microphone access, accompanied by instructions to execute a PowerShell command purportedly to resolve the issue.
In reality, executing the command installs a malicious script named “noanti-vm.bat,” disguised as a benign batch file that enables remote control over the victim’s device.
Additionally, analysts from KnowBe4 Threat Lab reported a phishing operation leveraging Google’s AppSheet platform to distribute emails posing as official Meta* support notices. These messages were sent from the legitimate “noreply@appsheet[.]com” domain, allowing them to bypass conventional authentication mechanisms such as SPF, DKIM, and DMARC. The emails warned users of imminent account deletion within 24 hours and urged them to follow a link to submit an “appeal.”
The link redirected recipients to an adversary-in-the-middle (AitM) phishing page, which requested login credentials, passwords, and two-factor authentication codes. Each email was adorned with a uniquely formatted “Case ID,” enhancing the campaign’s evasion capabilities by making it harder to detect using static indicators of compromise.
This string of coordinated attacks highlights a growing trend: cybercriminals increasingly deploy modular, open-source tools and blend them with sophisticated social engineering tactics to enhance stealth and effectiveness. The use of legitimate platforms as vectors for malicious payload delivery is becoming alarmingly prevalent.


