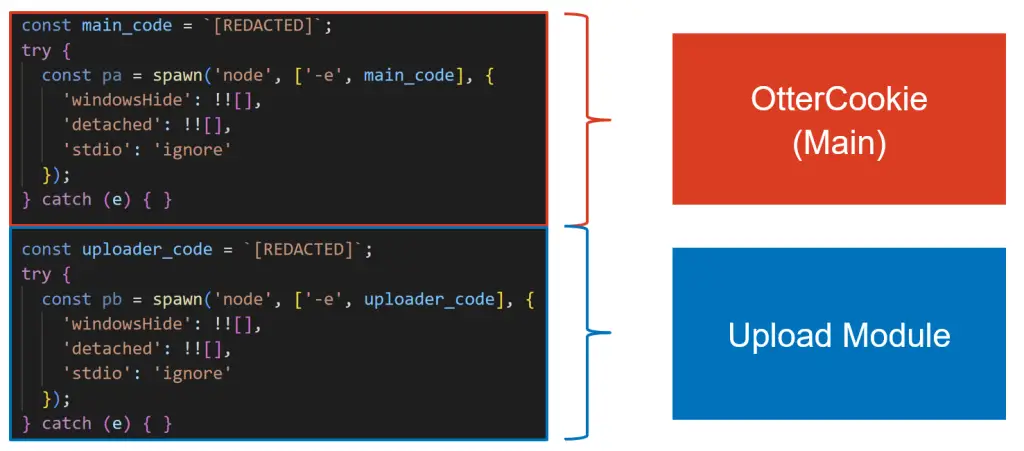
The North Korean cyber-espionage group behind the Contagious Interview campaign continues to evolve its multifunctional malware, OtterCookie—a cross-platform trojan capable of exfiltrating credentials from browsers, documents, and cryptocurrency wallets. According to Japan-based NTT Security Holdings, the third and fourth iterations of OtterCookie were detected in February and April 2025, signaling the persistent and active development of this malicious tool.
NTT tracks the threat actor under the moniker WaterPlum, also known by aliases such as CL-STA-0240, DeceptiveDevelopment, DEVPOPPER, Famous Chollima, PurpleBravo, and Tenacious Pungsan. First identified in September 2024, the malware was initially distributed via tampered npm packages containing embedded JavaScript, fraudulent GitHub and Bitbucket repositories, and counterfeit video conferencing applications. Its primary objective is to establish a connection with a remote command-and-control server and execute arbitrary instructions on the compromised machine.
The third version of OtterCookie introduced a dedicated file exfiltration module capable of harvesting documents, images, plaintext files, and data from cryptocurrency wallets—a task previously handled via shell commands. The fourth version expanded its capabilities further by incorporating two new modules specifically designed to extract sensitive data from the Google Chrome browser, the MetaMask extension in both Chrome and Brave, and Apple’s iCloud Keychain. One module is responsible for decrypting stored Chrome passwords, while the other retrieves encrypted login data. The distinct approaches used in these modules suggest the involvement of multiple developers.
The latest version also includes anti-analysis features, with embedded checks to detect execution within virtualized environments such as VMware, Oracle VirtualBox, Microsoft Hyper-V, and QEMU—complicating efforts to reverse-engineer or debug the malware.
Simultaneously, researchers are observing the evolution of other components tied to the campaign. One notable example is a macOS infostealer written in Go, disguised as a Realtek driver update (WebCam.zip). Victims are tricked into installing an application titled DriverMinUpdate.app, purportedly to fix webcam issues. In reality, it harvests the user’s system password. This approach mirrors tactics seen in the updated ClickFake Interview campaign, where bogus video and audio fixes are deployed during staged interviews.
According to Moonlock researchers, the infostealer’s objectives include establishing a persistent control channel, collecting system information, and exfiltrating sensitive data. Beyond DriverMinUpdate, analysts have identified several similar trojanized applications, including ChromeUpdateAlert, ChromeUpdate, CameraAccess, and DriverEasy.
The campaign is further supported by a newly observed malicious platform dubbed Tsunami-Framework—a .NET-based module featuring credential and wallet theft, keylogging, file harvesting, and an integrated yet incomplete botnet module. This framework is deployed as a second-stage payload following the Python-based backdoor InvisibleFerret.
Security analysts attribute the entire infrastructure to the Lazarus Group—North Korea’s infamous state-sponsored hacking unit known for its espionage and financially motivated operations. Among the group’s recent high-profile heists is the billion-dollar theft from the cryptocurrency exchange Bybit, which has also been linked to this threat actor.


