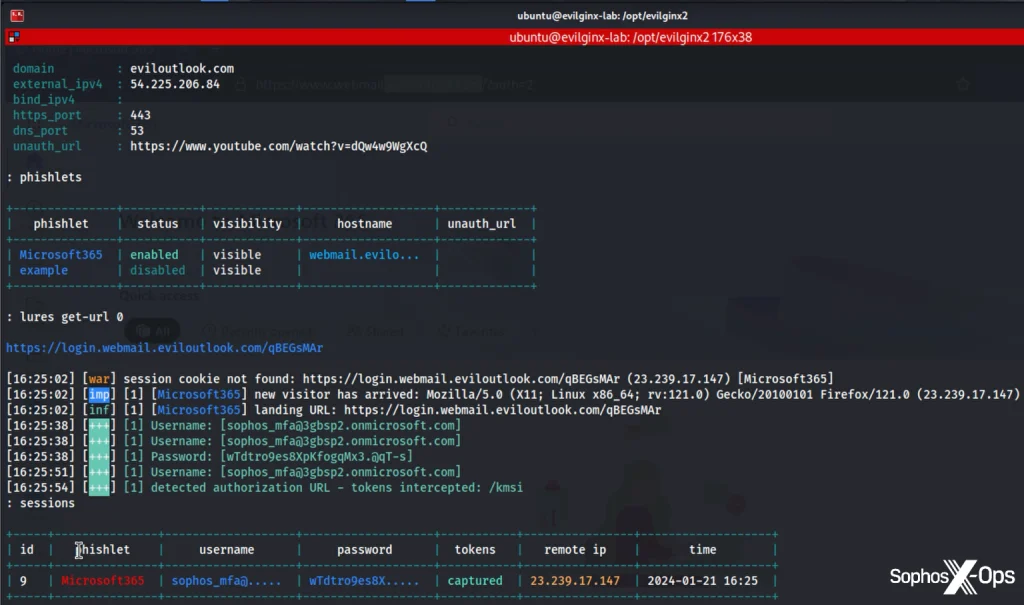
At first glance, Evilginx might appear to be just another tool in an attacker’s arsenal. Yet behind its unassuming name lies one of the most sophisticated implementations of the Adversary-in-the-Middle (AitM) technique, capable of circumventing even multi-factor authentication (MFA). According to researchers at Sophos, this tool—built atop the legitimate nginx web server—transforms a standard reverse proxy mechanism into a powerful session hijacking engine.
Evilginx operates by creating a phishing site that meticulously mirrors the appearance of popular services such as Microsoft 365. To the victim, everything looks authentic: login forms, images, and elements are pulled directly from the legitimate service. However, every user interaction passes through the attacker’s server, where login credentials, passwords, session cookies, and authorization tokens are silently intercepted. This effectively nullifies MFA, including push notifications and one-time passcodes.
At the heart of such an attack lies the session token—particularly valuable when the victim selects the “Stay signed in” option. Once intercepted, the token is logged alongside the user’s IP address, browser user-agent, and other metadata. The attacker can then import this cookie into their own browser, granting them full access to the victim’s account—as though they had signed in themselves.
The consequences of such a breach can be severe: access to emails, creation of mail-forwarding rules, MFA reset, and password changes—all of which can entrench the attacker further within the compromised environment and lay the groundwork for additional exploits.
To counteract this, Microsoft offers several tiers of logging and monitoring. Sign-in logs in Entra ID (formerly Azure AD) and unified audit logs in Microsoft 365 can surface anomalous behaviors such as logins from suspicious IP addresses, MFA device changes, or the creation of unexpected mail rules.
Experts recommend migrating toward more resilient forms of authentication. Protocols like FIDO2, hardware security keys such as Yubikey, and biometric methods including Apple’s Touch ID or Windows Hello provide robust defense against phishing-based compromise. Conditional access policies can further restrict sign-ins to trusted devices rather than relying solely on IP addresses.
Nonetheless, even the most advanced security measures cannot eliminate the risk of human error. No user is immune to phishing, which is why security architectures must be inherently resilient to such failures. In the event of a successful attack, it is essential to promptly revoke all active sessions and tokens through Entra ID and Microsoft 365, reset passwords and MFA configurations, and review audit logs for covert modifications like altered mail rules.
Evilginx underscores the peril of tools that, though built upon legitimate software, are repurposed for malicious intent. Its ability to bypass conventional defenses makes it particularly menacing—but with timely response and a transition to more robust authentication infrastructures, its threat can be effectively mitigated.


