Cybereason has released a new analytical report examining the operations of the PlayBoy Locker Ransomware-as-a-Service (RaaS) platform. This service poses a significant threat to organizations by equipping even non-technical threat actors with ready-made tools to launch sophisticated cyberattacks.
PlayBoy Locker first emerged in September 2024 on a dark web forum, where its creators initially sought beta testers. Shortly thereafter, an affiliate program was launched based on the classic RaaS model: affiliates retain 85% of the ransom, while the platform operators receive 15%. This structure enables inexperienced actors to deploy advanced attacks using preconfigured toolkits, including binary builds, control panels, and technical support.
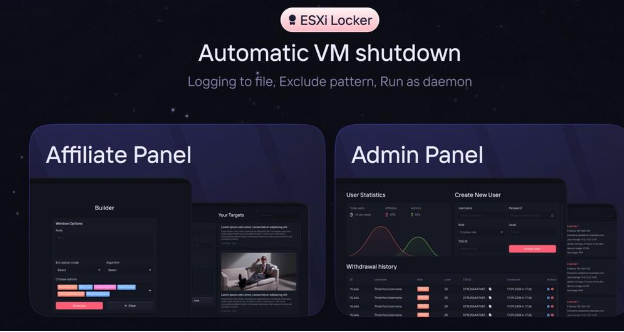
A defining feature of PlayBoy Locker is its malware builder, which allows affiliates to generate customized executables targeting Windows, NAS, and ESXi systems. The builder offers extensive configuration options and receives regular updates, making detection by antivirus solutions increasingly difficult. Affiliates are provided with guidance for malware distribution, technical support, and access to an administrative panel for managing infected systems and communicating with victims.
Technical analysis reveals that the Windows version of PlayBoy Locker is written in C++ and employs a combination of hc-128 and curve25519 for encryption. The malware implements a multithreaded queue to accelerate file encryption, deletes shadow copies via vssadmin, and terminates dozens of processes and services, including those related to popular applications and backup systems. Its targets range from Skype, Chrome, and Firefox to Oracle and Veeam. Furthermore, it features automated lateral movement through Active Directory domains using LDAP, enabling it to launch services on remote hosts.
Dedicated versions have also been developed for NAS and ESXi environments. On ESXi systems, PlayBoy Locker is capable of shutting down virtual machines, operating as a daemon, and excluding specified paths from encryption. The NAS variant allows targeted encryption along designated paths with minimal setup. Executable file sizes remain remarkably small, at around 70 KB.
Upon execution, the malware creates an INSTRUCTIONS.txt ransom note in every unencrypted directory. At the conclusion of its routine, it initiates self-deletion via command-line to conceal its presence.
The report includes hashes of known malicious samples to aid in detection, along with a set of mitigation recommendations, including:
- Monitoring affiliate activity
- Enforcing multi-factor authentication (MFA)
- Regular system backups
- Timely software patching
- Engagement of incident response teams
The growing professionalization of the RaaS ecosystem, as exemplified by PlayBoy Locker, significantly complicates the fight against ransomware. As the threat becomes more commoditized and widespread, it demands not only robust technical defenses but also continuous vigilance, proactive threat analysis, and rapid response capabilities.


