Infection chain overview: From PowerShell to final malware payload delivery
Cybercriminals have devised a cunning method to transform outdated Discord server links into digital traps: a newly uncovered scheme allows attackers to hijack expired invitation URLs and redirect users to malicious sites disguised as familiar communities. This vulnerability, identified by Check Point researchers in June 2025, stems from a flaw in Discord’s invitation system and poses a significant global threat.
The core of the attack lies in the exploitation of expired vanity URLs—custom invite links available to servers with a Boost Level 3 subscription. When such servers lose their premium status or their invites expire, the previously used URLs become available for re-registration. Malicious actors swiftly claim these addresses and bind them to their own nefarious servers, which visually mirror legitimate communities.
Unsuspecting victims, following these outdated links left on forums, social media, or websites, unknowingly land in the attackers’ domain. The malware delivery chain is carefully staged, prioritizing obfuscation and evasion. It begins with the user joining a counterfeit Discord server, where a bot named “Safeguard”—crafted specifically for this campaign—greets them and prompts a fake “verification” process designed to mimic official Discord procedures.
Upon clicking the verification button, the user is redirected to an external webpage that imitates Discord’s interface. A simulated Google CAPTCHA fails to load, prompting the user to manually input commands. At this point, clicking a button secretly copies a malicious PowerShell command into the clipboard.
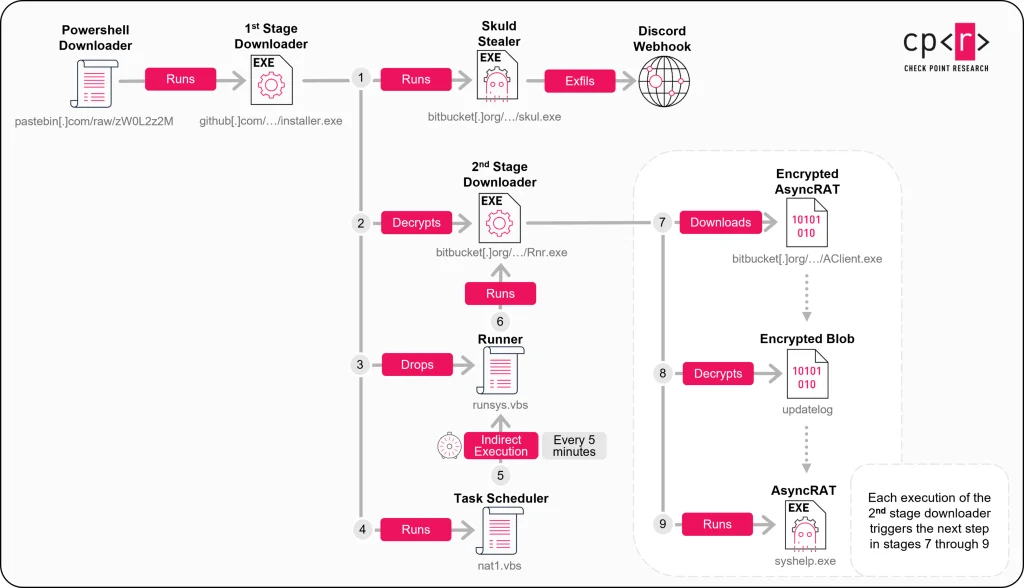
Next, the victim is instructed to open the Windows Run dialog (Win+R), paste the copied command, and press Enter. No file downloads are required, minimizing suspicion and allowing the attack to proceed undetected by most antivirus tools. The embedded command decodes a Base64 string and fetches a script from Pastebin, launching a multi-stage malware installation chain.
The downloaded payload includes the remote access trojan AsyncRAT and a customized variant of the Skuld stealer, optimized for siphoning cryptocurrency assets. Every stage of infection and data exfiltration operates exclusively through legitimate cloud platforms—GitHub, Bitbucket, Pastebin, and Discord itself—ensuring the malicious traffic blends seamlessly into regular network activity.
According to Check Point, at least 1,300 users across various countries—including the United States, Vietnam, France, Germany, and the United Kingdom—have fallen victim to the campaign. All indicators suggest that the attackers are financially motivated, with a primary focus on cryptocurrency wallet holders and digital asset custodians.
The social engineering technique employed, known as ClickFix, reveals a sophisticated psychological design. The malware doesn’t require downloads, masquerades as a routine task, and leverages users’ familiarity with Discord and typical Windows workflows. This quiet, calculated, and scalable method renders the scheme particularly insidious—and alarmingly effective.


