Image: Flashpoint
The world is confronting an unprecedented surge in cyber threats, with their scale and complexity continuing to escalate. A newly released Flashpoint report highlights the key trends shaping cybersecurity in 2025, including the rise of credential theft, the proliferation of infostealers, the exploitation of vulnerabilities, and the intensification of ransomware-driven attacks.
In 2024, cybercriminals compromised over 3.2 billion credentials, marking a 33% increase compared to the previous year. These stolen records are actively traded on the dark web, fueling ransomware operations and other forms of malicious activity. Already, in early 2025, more than 200 million accounts have been pilfered, underscoring the persistent and escalating nature of this threat.
Of particular concern is the rapid expansion of infostealers—a category of malware engineered to siphon confidential data. In 2024, a staggering 75% of the 3.2 billion stolen credentials were acquired through this method. More than 23 million devices worldwide are currently infected, cementing infostealers as a dominant attack vector, facilitating both ransomware deployment and large-scale data breaches.
Throughout 2024, underground forums circulated 24 distinct families of infostealers. The most prevalent was Redline, responsible for infecting 9.9 million devices, accounting for 43% of total infections. Other widely distributed strains—RisePro, SteaC, Lumma Stealer, and Meta Stealer—collectively compromised 7 million systems.
Beyond targeting individual users, infostealers have become a catalyst for major data breaches. In April 2024, cybercriminals leveraged stolen credentials harvested via infostealers to infiltrate 165 customer environments within Snowflake. The breach exposed hundreds of millions of records, affecting major corporations such as AT&T, Ticketmaster, and Advance Auto Parts.
Moreover, the volume of documented vulnerabilities surged by 12% in 2024, reaching a total of 37,302. Alarmingly, over 39% of these flaws have publicly available exploits, enabling adversaries to swiftly weaponize them for system breaches. Amid accelerating digitalization, organizations must reassess their vulnerability management strategies, prioritizing not only severity rankings but also the availability of real-world exploitation methods.
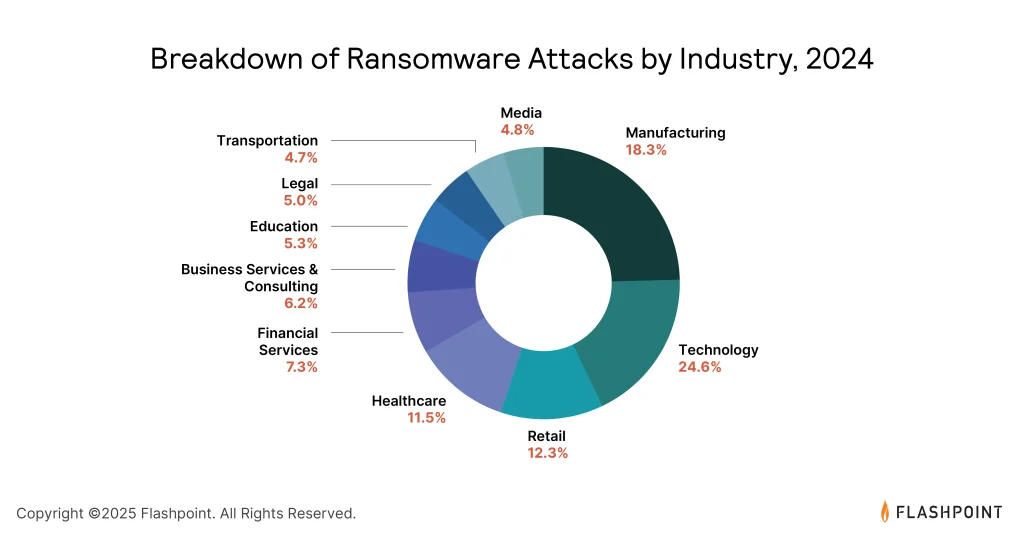
The relentless activity of cybercriminals is further evident in the escalation of ransomware attacks. In 2024, the number of incidents increased by 10%, while data leaks surged by 6%. The most formidable threats stem from Ransomware-as-a-Service (RaaS) operations, with groups such as LockBit, Ransomhub, Akira, Play, and Qilin collectively responsible for 47% of all ransomware incidents in the past year.
Security experts emphasize the urgent need for organizations to adopt a proactive approach to risk management. A comprehensive cybersecurity strategy—encompassing threat intelligence, vulnerability management, and incident response protocols—is imperative in the fight against an increasingly sophisticated cyber threat landscape.


