The critical vulnerability CVE-2025-49113, discovered in the widely used webmail platform Roundcube, found its way into the hands of cybercriminals mere days after a patch was released. Malicious actors swiftly analyzed the changes in the source code, reverse-engineered the vulnerability, and began selling a working exploit on underground forums. The flaw affects Roundcube versions from 1.1.0 through 1.6.10 and remained embedded in the codebase for over a decade.
Roundcube is deeply entrenched in the hosting ecosystem, utilized by leading providers such as GoDaddy, Hostinger, Dreamhost, and OVH. It is also integrated into popular control panels like cPanel and Plesk, making it a staple in educational, governmental, and technological institutions worldwide. Researchers estimate that over 1.2 million active deployments exist.
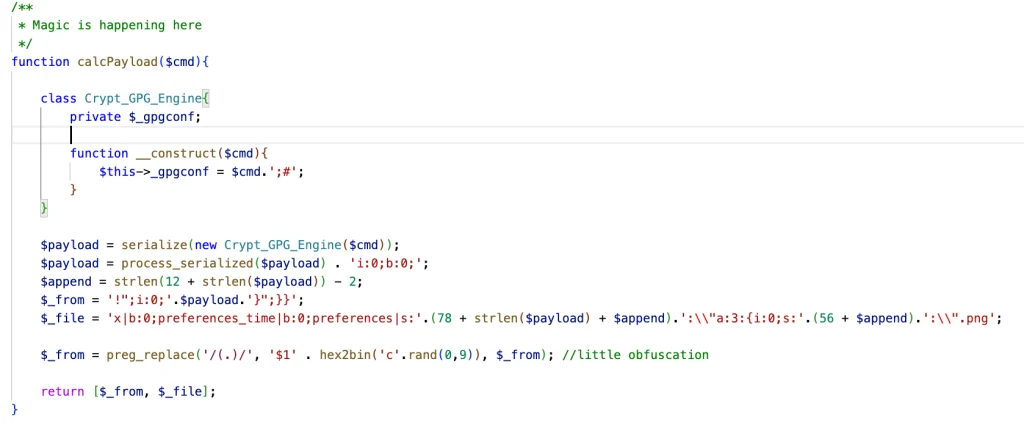
The vulnerability stems from improper handling of the $_GET['_from'] parameter, enabling PHP object deserialization. When the variable follows a specific format, the session becomes corrupted, allowing an attacker to inject a malicious object. Although exploitation requires authentication, this barrier is considered trivial—credentials can be obtained through brute-force attacks, log extraction, or cross-site request forgery (CSRF).
Researcher Kirill Firsov, CEO of FearsOff, disclosed that due to the rapid exploitation in the wild, he chose to publish technical details of the flaw ahead of the responsible disclosure deadline. While a full proof-of-concept (PoC) was not released, the shared information suffices to grasp the vulnerability’s nature and exploitation path.
Firsov emphasized that adversaries needed only a few days to reverse-engineer the patch and craft a functional exploit—underscoring the critical danger posed by the gap between patch release and deployment. On dark web forums, the exploit is already being circulated, marked with the note that valid credentials are required for successful execution.
According to Firsov, a known vulnerability brokerage firm has offered up to $50,000 for a fully operational exploit chain targeting this flaw. He further noted that locating a Roundcube instance during penetration tests is significantly easier than identifying SSL vulnerabilities, due to the platform’s extensive distribution.
Although relatively obscure to the average user, Roundcube is recognized as one of the most versatile and customizable webmail systems, offering support for over 200 configuration parameters and available under an open-source license. Its ubiquity magnifies the potential risk, placing entire sectors at exposure.
Firsov also released a demonstration video of the attack, initially referencing the erroneous CVE-2025-48745, which was later rejected as a duplicate of CVE-2025-49113. However, the attack methodology remains identical.
With the exploit now circulating publicly, the vulnerability has entered an active exploitation phase. Any Roundcube installation lacking prompt updates now constitutes a potential gateway for intrusion.


