Samsung Corporation has released a security update for MagicINFO 9 Server, addressing a critical vulnerability—CVE-2025-4632—that has already been exploited by threat actors in real-world attacks. This flaw, rated 9.8 on the CVSS scale, is linked to a path traversal issue, allowing attackers to write arbitrary files as the system account while bypassing directory constraints.
Of particular concern is the fact that CVE-2025-4632 constitutes a bypass of a previously resolved vulnerability, CVE-2024-7399, which had been identified and patched in August 2024. Despite that remediation, the newly discovered issue re-enabled exploitation through alternate vectors. Following the public release of a proof-of-concept by SSD Disclosure on April 30, 2025, the vulnerability was swiftly weaponized. In certain instances, it was used to deploy components of the Mirai botnet, notorious for its widespread attacks on IoT devices.
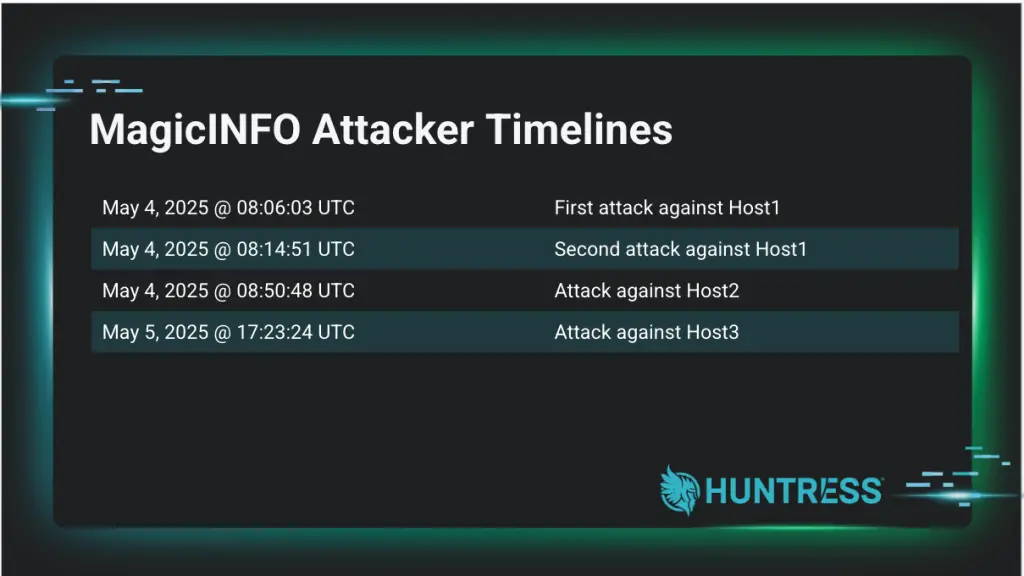
The cybersecurity firm Huntress was the first to detect anomalous behavior on systems running the then-latest version of MagicINFO (21.1050.0), which was believed to have resolved all known vulnerabilities. Their investigation uncovered CVE-2025-4632, which allowed adversaries to execute identical commands across multiple hosts. These included the deployment of executable files such as “srvany.exe” and “services.exe,” as well as activities indicative of reconnaissance efforts.
In a report published on May 9, Huntress detailed three distinct incidents involving the exploitation of CVE-2025-4632. Unidentified groups carried out attacks following an identical playbook, enabling analysts to precisely trace the intrusion vector and the attackers’ methodology.
Samsung has since issued an updated version—MagicINFO 9, build 21.1052.0—that fully addresses the vulnerability. However, upgrading to this release requires first applying the intermediary update 21.1050.0, which may hinder some users from promptly mitigating the risk. Systems running MagicINFO versions from v8 up to v9 21.1050.0 remain particularly vulnerable.
Huntress strongly urges all users to upgrade immediately to version 21.1052.0. According to Jamie Levy, Director of Adversary Tactics, this is the only version that comprehensively neutralizes the CVE-2025-4632 exploit path. Failure to do so may leave systems exposed to arbitrary code execution and deeper infiltration into enterprise infrastructure.


