Credential stuffing remains one of the most prevalent and effective methods of unauthorized access. By leveraging databases of compromised usernames and passwords, cybercriminals gain entry to other platforms where users have recycled the same credentials. Automated tools now allow such attacks to be executed at scale.
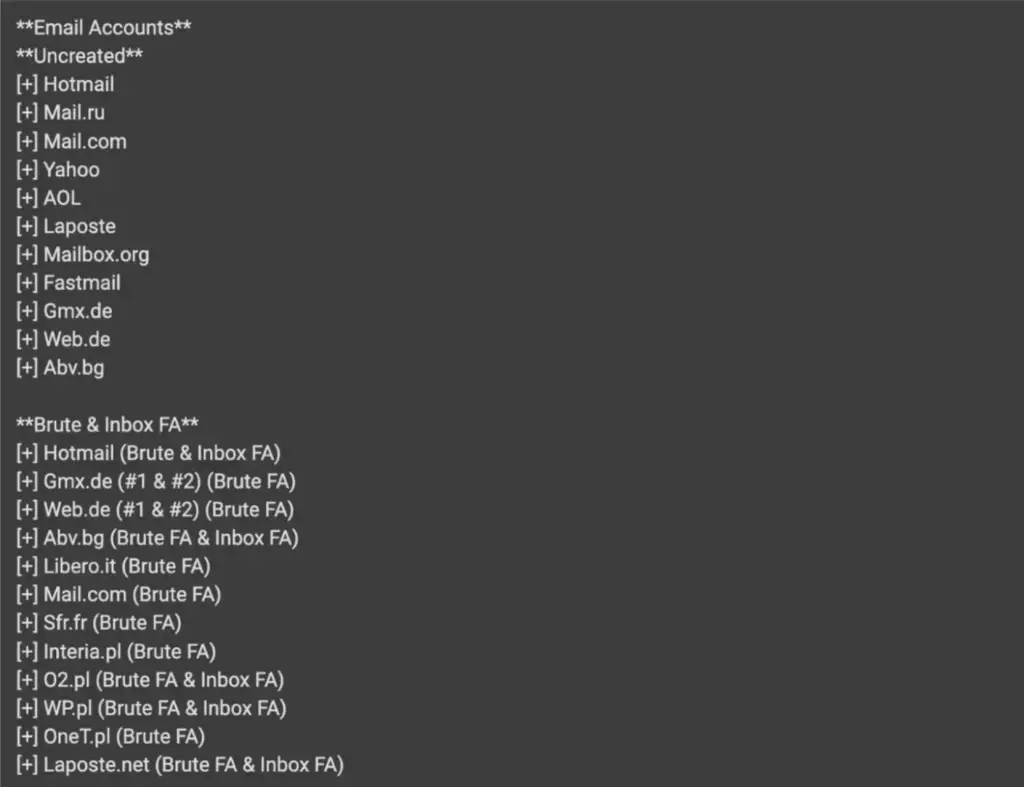
According to research by Abnormal Security, one such tool is Atlantis AIO—a program capable of testing millions of login-password combinations across more than 140 platforms within minutes. It comes equipped with prebuilt modules for widely used online services, particularly email providers such as Hotmail, Yahoo, and AOL.
Atlantis AIO automates the credential-matching process, enabling attackers to hijack accounts without manual effort. Once access is gained, the compromised accounts are exploited for phishing campaigns, data exfiltration, or resale on underground forums.
The tool is built on a modular architecture. Dedicated components target email services, financial platforms, streaming providers, and even delivery apps. Password-cracking modules rapidly brute-force vulnerable accounts, while recovery modules are designed to circumvent CAPTCHAs and other protective barriers.
Compromised login credentials are frequently sold in bulk—often numbering in the tens of thousands—and include both personal and corporate email addresses. This vulnerability is exacerbated by the widespread practice of password reuse across work and personal accounts.
Traditional defenses—such as complex passwords, password managers, and multi-factor authentication—are increasingly insufficient. Malicious actors are evolving tactics to bypass even MFA, continuing to rely on automated systems to orchestrate expansive campaigns.
To counteract credential stuffing, prevention must begin at the earliest stages—before credentials are ever stolen. Modern AI-powered systems are capable of detecting phishing attempts, identifying anomalous behaviors, and proactively blocking account takeover efforts. These advanced solutions are essential in safeguarding enterprise data and neutralizing attacks before access is achieved.


