In early 2025, researchers at Silent Push uncovered a new phishing campaign targeting Counter-Strike 2 players, distinguished by its use of unconventional social engineering tactics—specifically, “browser-in-the-browser” (BitB) attacks. These techniques create visually convincing login pop-ups that mimic legitimate website elements, deceiving users into believing they are interacting with authentic authentication prompts and thereby exposing their Steam credentials to malicious actors.
The primary target of these attackers is the Steam gaming platform, owned by Valve. Special emphasis was placed on exploiting fans of the esports team Natus Vincere (NaVi), leveraging the team’s recognizable branding as bait. The fraudulent websites offered “free cases,” a common lure that capitalizes on gamers’ interest in in-game items. These phishing pages were meticulously crafted to resemble legitimate login interfaces, leaving users unaware of the deception.
The campaign’s infrastructure spanned dozens of domains, such as “caserevs[.]com,” “caseneiv[.]com,” and others. Notably, one site—“simplegive[.]cn”—featured Chinese-language content interspersed with English, suggesting an effort to expand the operation beyond English-speaking users. All domains were hosted on a single dedicated IP address, simplifying their technical analysis and traceability.
The attackers aggressively promoted these phishing sites via YouTube. In January 2025, one such video garnered over 600 likes—likely through artificial inflation. Leveraging highly trusted platforms like YouTube significantly enhances the campaign’s perceived legitimacy and broadens its reach to unsuspecting users.
BitB attacks, while known to the cybersecurity community for some time, remain relatively rare in real-world scenarios. The technique gained prominence following disclosures by a researcher known as “mrd0x,” who published a working proof-of-concept along with a technical breakdown. A similar campaign using Cloudflare’s free hosting domain “pages[.]dev” was observed in June 2024.
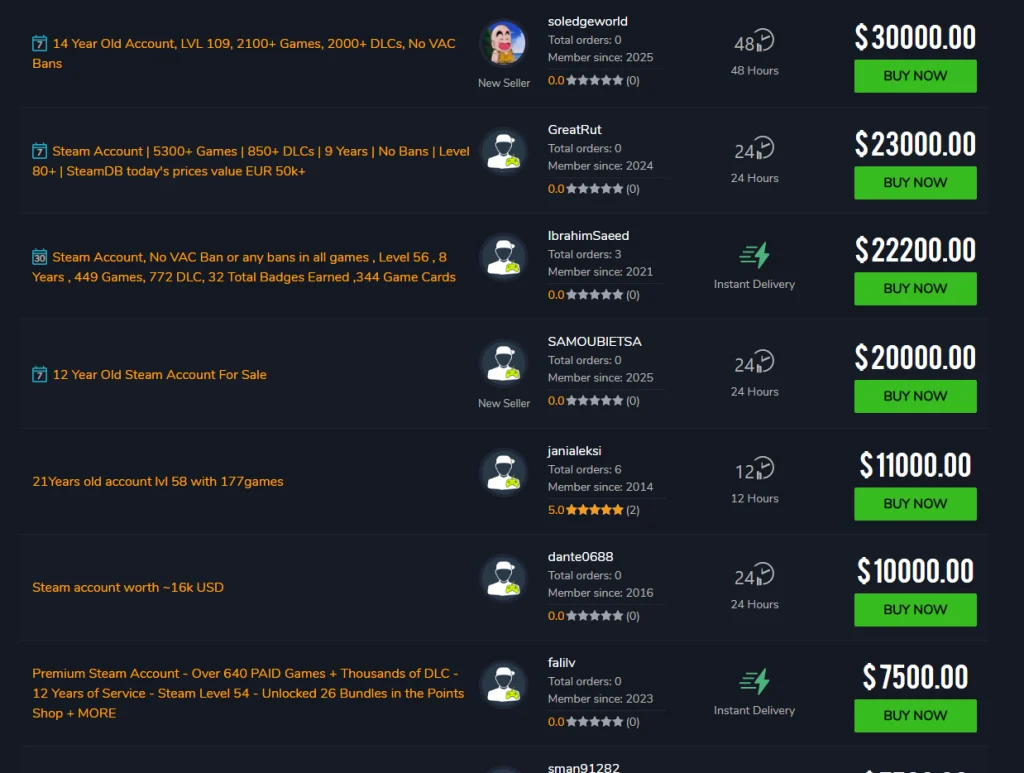
Steam accounts are prized not merely for their monetary value but also for the rare games and in-game items they contain. On black-market platforms such as “playerauctions[.]com,” these accounts can fetch prices in the tens of thousands of dollars. This makes them a lucrative target for cybercriminals, who frequently resell the stolen credentials.
BitB attacks are particularly potent on desktop systems, where the spoofed windows are visually indistinguishable from genuine ones. However, there are subtle indicators—such as the inability to drag the window beyond the browser’s frame—that can reveal their fraudulent nature. This behavioral discrepancy can serve as a telltale sign of a phishing attempt.
Silent Push urges users to remain vigilant and verify the authenticity of login windows. If a window appears suspicious, attempting to drag it outside the browser can help determine its legitimacy. In the event of a suspected compromise, users are advised to promptly change their passwords and review associated account activity.
Given the evolving sophistication of this phishing technique, researchers anticipate that BitB attacks will gain momentum throughout 2025. Future campaigns may adapt these methods to target additional brands and gaming platforms. Silent Push has committed to continuing its investigations and sharing insights with the broader cybersecurity community and law enforcement agencies.


