The ClickFix method, rooted in social engineering, has now extended beyond Windows. Researchers at Hunt.io have uncovered a new wave of attacks in which this technique has been adapted for Linux — marking the first confirmed instance of such a transition.
Previously, ClickFix enabled attackers to coerce Windows users into manually executing PowerShell scripts disguised as system alerts or error messages, ultimately resulting in the installation of malicious software, including infostealers and ransomware.
At its core, the technique involves convincing victims to voluntarily input harmful commands under the guise of resolving a fabricated issue. The adaptation of this method to target Linux users signals not only its growing popularity but also its disturbing versatility.
In the latest campaign, attributed to the Pakistan-linked threat group APT36 (also known as Transparent Tribe), a spoofed website impersonating India’s Ministry of Defence lures users with a supposed official press release. The malicious site first detects the visitor’s operating system, tailoring the attack scenario accordingly.
If the system is identified as Windows, the user is shown a fullscreen warning about access restrictions. JavaScript then activates, copying an MSHTA command to the clipboard, which is intended to launch a .NET-based malware loader. To maintain the illusion, a counterfeit PDF document is opened in the background.
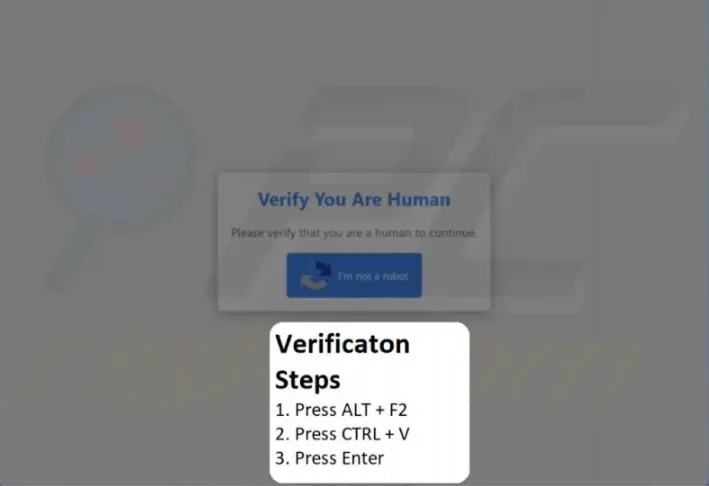
If the visitor is using Linux, they are redirected to a CAPTCHA page. Upon clicking “I’m not a robot,” a shell command is covertly copied to the clipboard. The instructions prompt the user to press ALT+F2 — a standard method to open the run dialog in Linux graphical environments — and paste the script. The script is then saved as a file named mapeal.sh and executed.
According to Hunt.io, the current version of the script performs no malicious actions — it merely downloads and opens a JPEG image from a remote server. However, this apparent harmlessness is likely a placeholder: substituting the image with a fully functional shell script could initiate malware installation, achieve persistence, and establish a connection with a command-and-control server.
There is no evidence yet that the Linux-based script includes persistence mechanisms or lateral movement capabilities. Nevertheless, researchers believe APT36 may be testing the efficacy of social engineering within the Linux environment before escalating to more aggressive operations.
Earlier in 2024, this technique was also observed targeting macOS users through fake Google Meet error messages. The fact that ClickFix has now been deployed across all three major desktop platforms — Windows, macOS, and Linux — underscores its alarming effectiveness.
Researchers emphasize: no command should ever be copied and executed manually from the clipboard without full certainty of its intent. Such actions can result in malware installation and the compromise of sensitive data.


