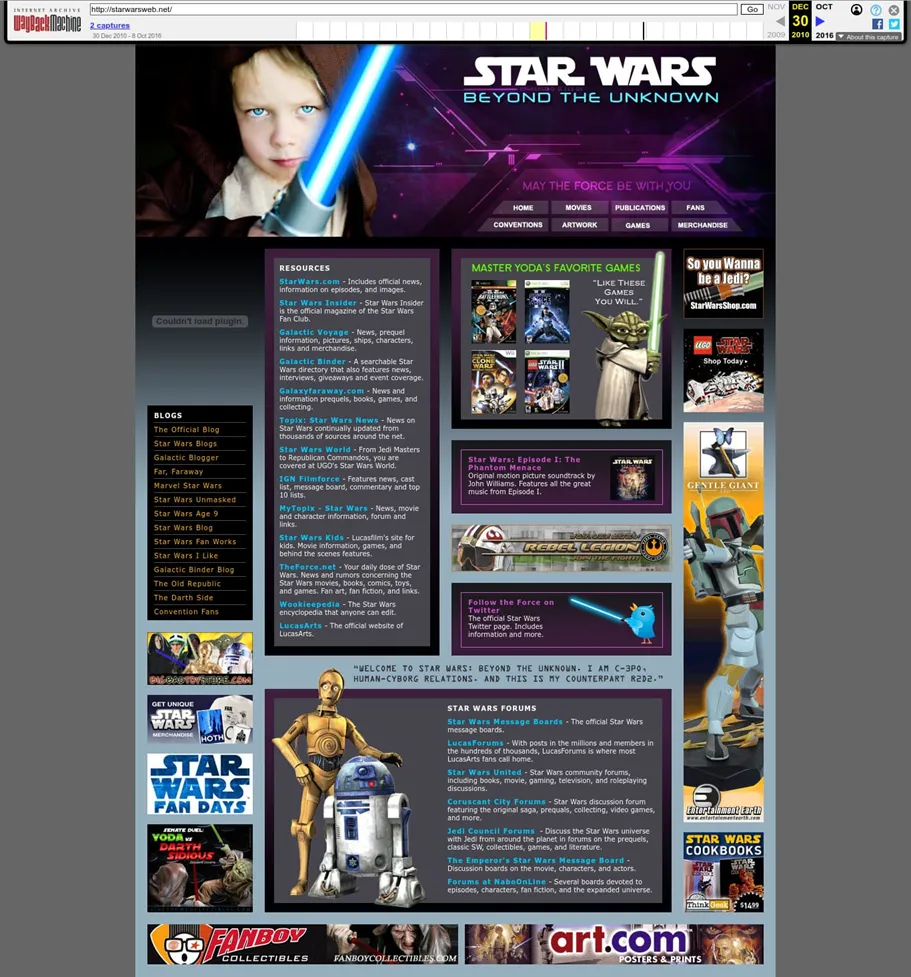
At first glance, starwarsweb.net appears to be a typical fan site from the golden age of the Xbox 360—complete with a Yoda quote (“Like these games you will”), a selection of titles like Star Wars Battlefront II, and ads for Lego Star Wars kits. Yet beneath this seemingly innocent facade lay a far more sinister purpose. It has since come to light that the website was used by the CIA as a covert communication platform for operatives abroad. Disguised as pages about video games, sports, and pop culture, it housed an intricate network of digital dead drops—one of the most consequential intelligence blunders in recent decades.
According to independent researcher Ciro Santilli, starwarsweb.net was merely one node in a broader system of websites functioning as clandestine channels for CIA communications with foreign assets. These sites were crafted to appear completely innocuous—fan pages for comic books, portals about Brazilian music, or extreme sports blogs. But entering a password into the site’s search bar triggered a hidden authentication mechanism, granting access to encrypted correspondence with U.S. intelligence.
The first exposure of this covert scheme occurred more than a decade ago—in Iran. At the time, local intelligence agencies uncovered the network and began targeting suspicious individuals, an effort that ultimately culminated in a wave of arrests and executions of CIA operatives in China during 2011–2012. According to a Yahoo News investigation, the Iranian breach played a pivotal role in the collapse of the entire system. The CIA subsequently dismantled its infrastructure.
Santilli explained that several motivations led him to unearth the CIA’s long-abandoned network: an interest in Chinese politics, the influence of his mother-in-law—a follower of the Falun Gong movement—and a desire to “expose the spies surveilling democracies.” He describes his effort as a hacker-style investigation, built on domain analysis, HTML inspection, use of services like viewdns.info, and trawling through the Wayback Machine—circumventing its limitations by deploying an army of Tor-based bots. All tools, he emphasized, were open-source and freely accessible.
One of the key catalysts for this renewed search was a 2022 Reuters article, which highlighted flaws in the obfuscation of the CIA’s websites—specifically that their IP addresses were sequential, allowing entire clusters of domains to be discovered. On screenshots from Santilli’s research, he identified file names referencing original URLs, breadcrumbs that led to hundreds of additional sites.
According to another independent cybersecurity expert, Zach Edwards, these revelations are entirely consistent with his own understanding of the network’s architecture. He confirmed that the sites were indeed operational and served intelligence functions, and that the developers’ oversights had eventually exposed them to the public eye.
Santilli noted that now, more than fifteen years later, the exposure of these sites no longer poses a critical threat, but rather offers a rare glimpse into the digital relics of a bygone espionage era. He likened the experience to visiting a museum—thanks to archived web pages, anyone can examine the “living” remnants of a failed covert operation. This story is far from unique in the annals of American intelligence; the CIA has previously endured major compromises of its clandestine activities.
The CIA declined to comment.


