Image: ThreatFabric
Cybersecurity researchers have reported the emergence of a new Android banking trojan named Crocodilus, which is actively targeting users in Spain and Turkey. Unlike many nascent threats, Crocodilus has immediately distinguished itself as a sophisticated and technologically advanced piece of malware.
According to ThreatFabric, the trojan leverages a comprehensive arsenal of modern techniques—from remote device control to overlaying fake login screens and harvesting sensitive data via accessibility services. It is capable of completely hijacking the victim’s device and executing financial transactions without their knowledge.
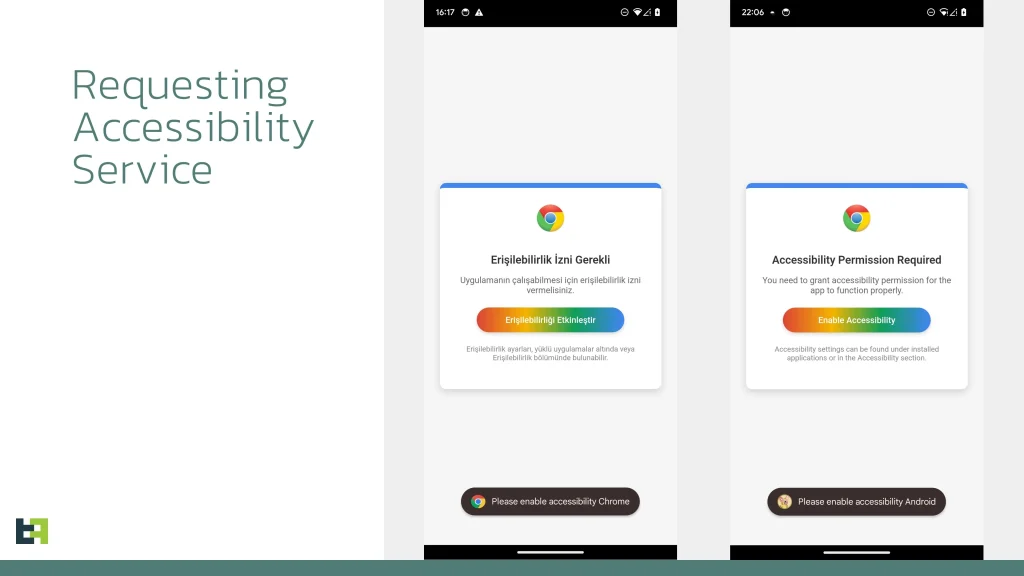
What sets Crocodilus apart is its disguise: it masquerades as the Google Chrome browser, adopting the deceptive package name “quizzical.washbowl.calamity.” This ruse enables it to bypass native Android defenses and install itself even on devices running Android 13 or later. Once launched, the app demands accessibility permissions, unlocking extensive capabilities for further exploitation.
By connecting to a remote command-and-control server, Crocodilus can fetch a list of target applications, download phishing HTML templates, and receive tailored instructions for manipulating the compromised device. Beyond traditional banking apps, it also targets cryptocurrency wallets. Rather than presenting fake login screens, it displays urgent messages urging the user to “secure their seed phrase,” warning of potential asset loss. By following these prompts, users inadvertently reveal critical credentials, which the malware siphons off through its accessibility permissions.
Crocodilus does not merely record keystrokes or monitor open applications—it observes all screen events and can capture screenshots, even within highly protected apps like Google Authenticator, thereby making the theft of two-factor authentication codes a real possibility.
To remain hidden, the malware can activate a black screen, mute system audio, and erase visual indicators of its activity, significantly lowering the chances of detection. Among its broad functionality are: launching specified apps, sending SMS messages to contacts, compiling a list of installed applications, issuing push notifications, receiving incoming SMS messages, and assigning itself as the device’s default messaging manager.
Additionally, it can request device administrator privileges, mute the system, activate keylogging, alter C2 server settings, and self-delete after completing its objectives.
ThreatFabric’s analysis concludes that Crocodilus represents not merely a new malicious app but a fully developed, mature threat with a feature set more typical of long-established trojans. Its meticulous design and polished execution suggest a deep understanding of mobile security. The presence of Turkish-language strings and debugging messages in the code strongly implies that the malware originates from Turkey.
The appearance of Crocodilus coincides with another active campaign distributing the Grandoreiro banking trojan via phishing emails themed around tax-related lures. This campaign, aimed at Windows users in Mexico, Argentina, and Spain, employs obfuscated Visual Basic scripts to deliver its payload—underscoring that banking-focused cyberattacks continue to evolve in parallel across both mobile and desktop platforms.


