Developers of .NET applications who integrate the CefSharp framework to embed Chromium-based browsers into desktop software now face the risk of serious security vulnerabilities. A new tool, CefEnum, unveiled by the team at DarkForge Labs, exposes critical flaws that could lead to remote code execution, persistent access, and stealthy attacks within Windows environments.
CefSharp serves as a wrapper around the Chromium Embedded Framework, enabling developers to embed web interfaces into desktop applications. One of its primary advantages lies in its bidirectional communication between JavaScript and internal .NET objects. However, this very feature often becomes a vector for exploitation when developers neglect stringent security practices.
According to a report published by DarkForge Labs, vulnerabilities such as cross-site scripting (XSS) within these “fat clients” can escalate into full system compromise. If an attacker gains access to trusted .NET objects via a vulnerable web interface, they may execute arbitrary code on the victim’s machine. As a demonstration, researchers showcased the BadBrowser application, where a JavaScript snippet can write a file to disk using the command window.customObject.WriteFile("test.txt").
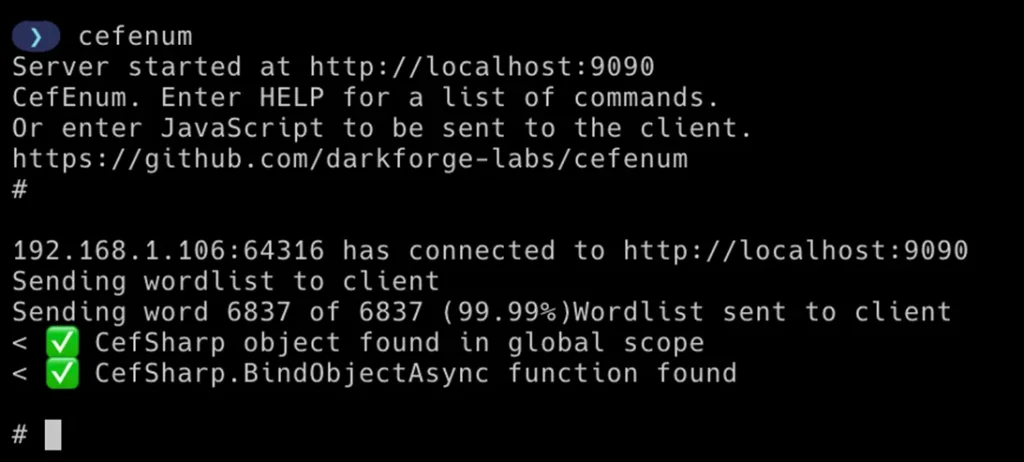
CefEnum, now publicly available on GitHub, is designed to identify CefSharp implementations during security testing. It spins up an HTTP server on a configurable port (defaulting to 9090) and sends connected clients a dictionary to brute-force object names at a rate of up to 2,000 attempts per second.
To detect accessible objects, CefEnum leverages the CefSharp.BindObjectAsync() and CefSharp.IsObjectCached() methods—allowing discovery even of components not visible without access to the source code. Once identified, CefEnum can conduct brute-force introspection, enabling an attacker to invoke vulnerable methods directly from the browser.
These capabilities underscore the urgent need for tighter control over which classes and methods in a .NET application are exposed to the browser. According to the authors of the report, the risk is especially acute when web interfaces load external resources without strict source validation. Even with a whitelist of trusted domains, an XSS vulnerability on an approved portal could allow attackers to inject malicious code into a “trusted” environment.
DarkForge Labs advises developers to rigorously reevaluate their application architecture: reduce the surface of exposed methods, enforce strict whitelisting of trusted sources in native code, and perform comprehensive security audits of their CefSharp integrations.
Despite CefSharp’s widespread adoption in the enterprise space, its insufficient security posture could yield severe consequences. The emergence of CefEnum is not merely a cautionary signal—it is a practical tool to help developers uncover and remediate vulnerabilities before malicious actors exploit them.


