The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has announced that, moving forward, it will publish only...
Security
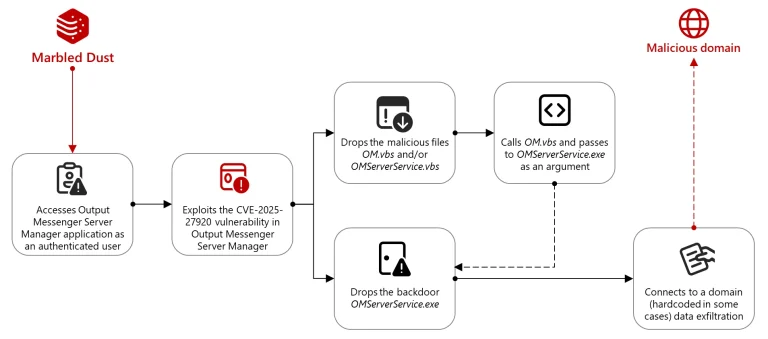
The APT group known as Marbled Dust, believed to be affiliated with the Turkish government, has orchestrated...
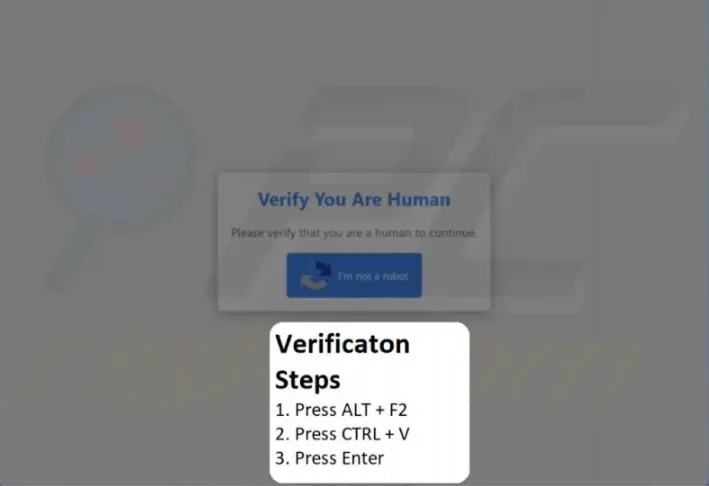
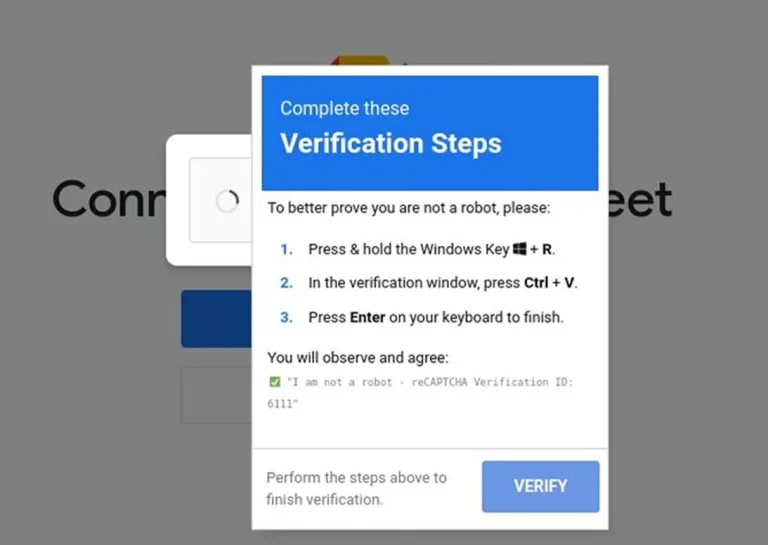
The ClickFix method, rooted in social engineering, has now extended beyond Windows. Researchers at Hunt.io have uncovered...
Google has agreed to pay the state of Texas $1.375 billion in settlement of two lawsuits alleging...
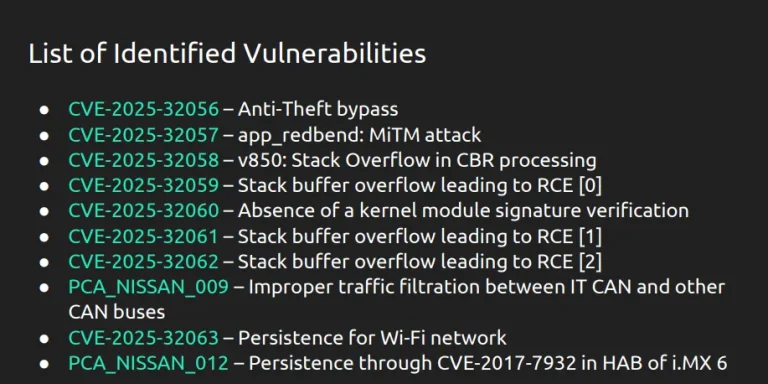
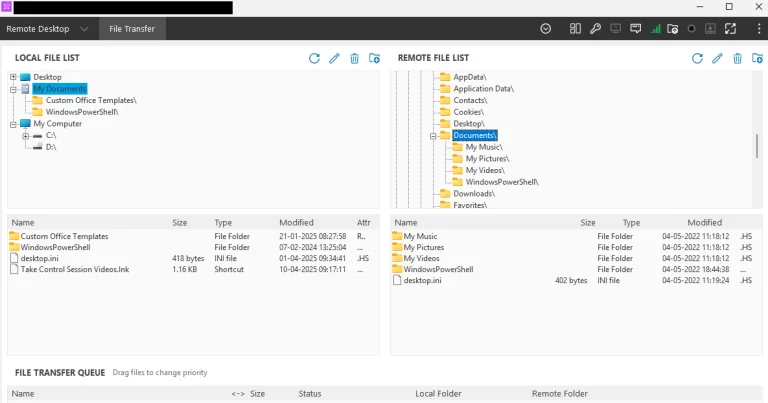
A group of European white-hat hackers from the Budapest-based company PCAutomotive has demonstrated a remote hack of...
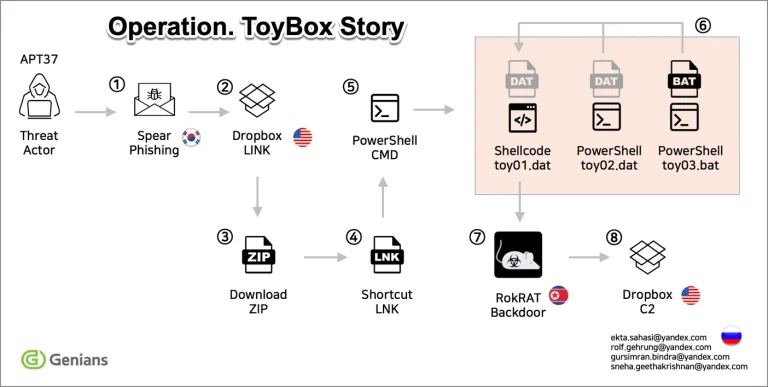
In March 2025, cybersecurity specialists from South Korea’s Genians Security Center uncovered a new operation orchestrated by...
Shelves at the British retail chain Co-op remain partially empty two weeks after a cyberattack disrupted the...
The credentials of an employee affiliated with two prominent U.S. government entities—the Cybersecurity and Infrastructure Security Agency...
Researchers at Socket have uncovered a new attack targeting the macOS version of the popular source code...
U.S. Senators Jacky Rosen (D-NV) and Bill Cassidy, M.D. (R-LA) have introduced a bipartisan bill aimed at...
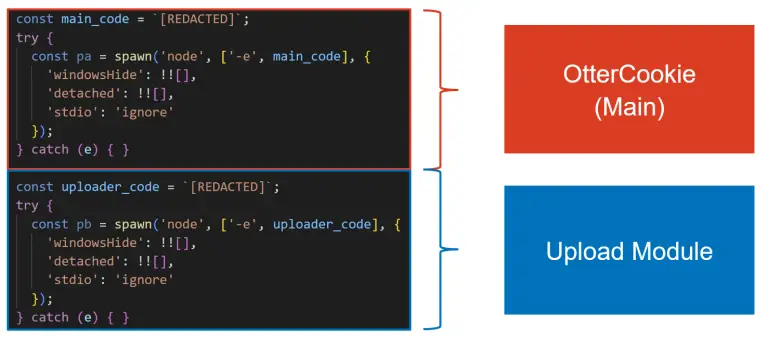
The North Korean cyber-espionage group behind the Contagious Interview campaign continues to evolve its multifunctional malware, OtterCookie—a...
Since the beginning of 2025, Cisco Talos specialists have been tracking a new malicious campaign targeting Portuguese-speaking...
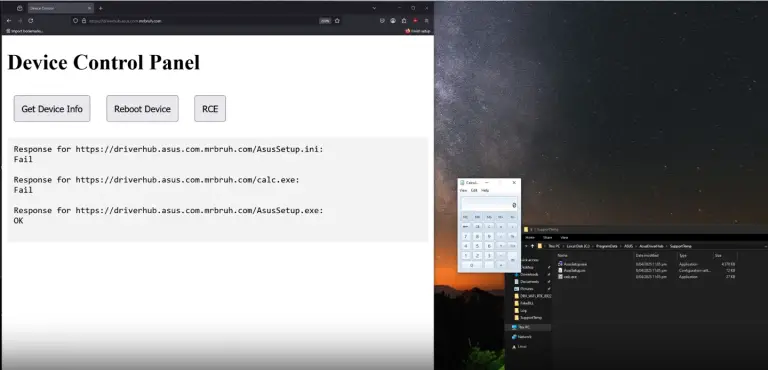
A user who had purchased an ASUS motherboard discovered that the driver installation software—automatically triggered via the...
An unusual social engineering attack was recently discovered on the website of iClicker, a widely used educational...
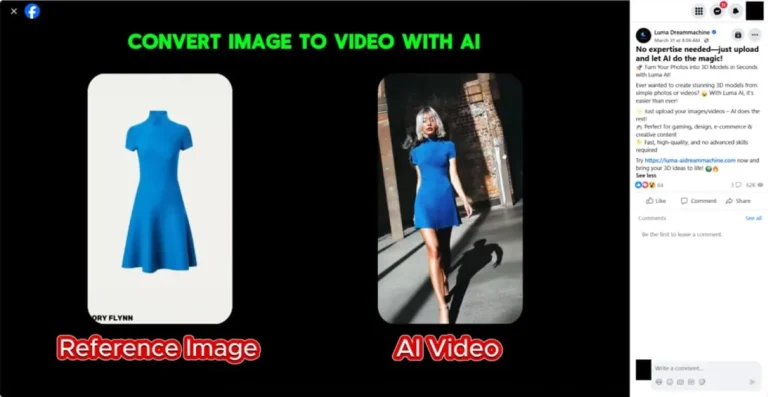
Fake AI-powered video generation platforms have emerged as a new front for disseminating a dangerous malware strain...