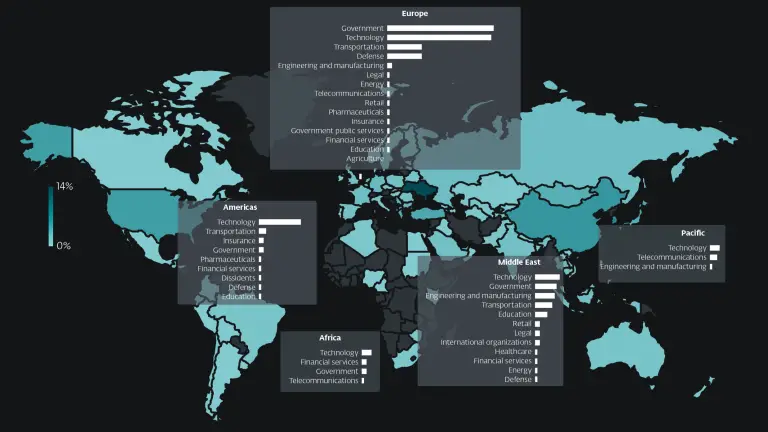
Researchers at ESET have uncovered the operations of a little-known yet active cyber-espionage group linked to China,...
Security
The high-profile cyberattack on the British retail chain Marks & Spencer has taken a new turn. Sources...
Since February 2024, the Chrome Web Store has been hosting malicious browser extensions disguised as useful utilities,...
Every smartphone owner knows the first essential step with a new device: enabling screen lock. Most users...
A 19-year-old college student from Worcester, Massachusetts has pleaded guilty to orchestrating a large-scale cyberattack on PowerSchool—one...
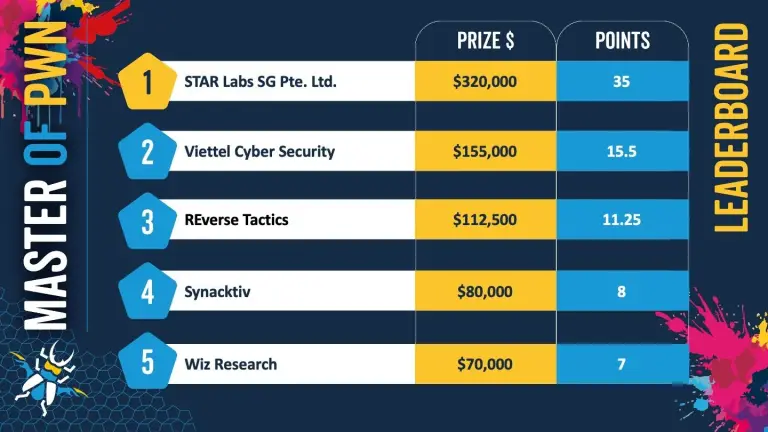
Pwn2Own 2025 has concluded in Berlin, marking one of the most significant showcases of zero-day vulnerabilities in...
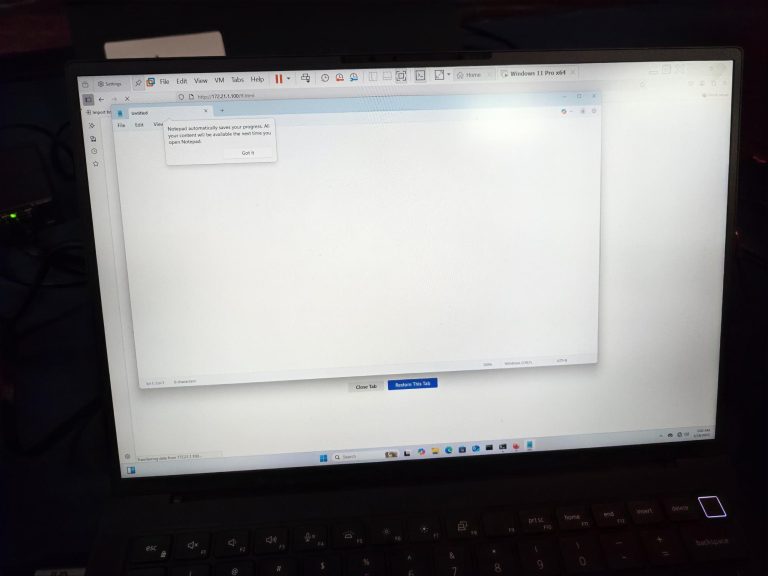
Mozilla has released emergency security updates for Firefox—just hours after the conclusion of the Pwn2Own Berlin 2025...
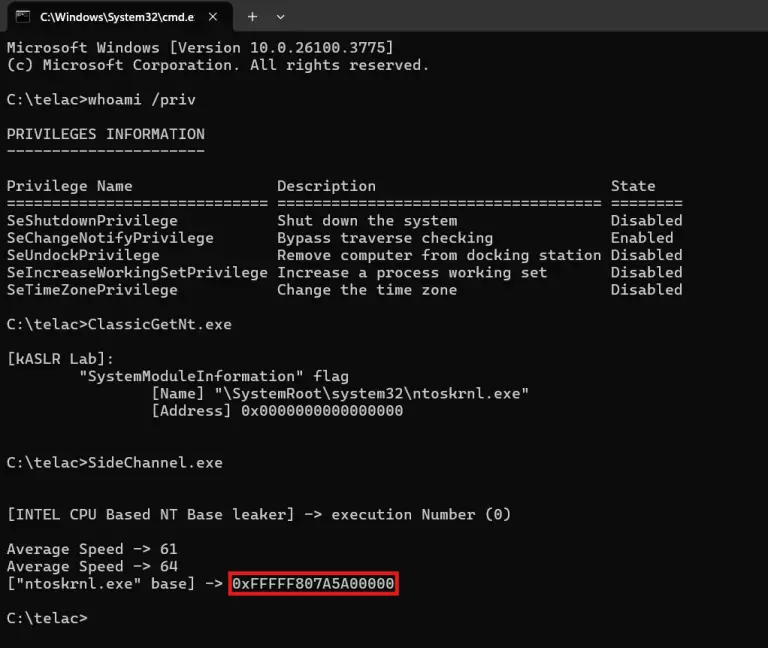
Security researchers have unveiled a method for circumventing KASLR—one of the kernel’s principal defense mechanisms—on fully updated...
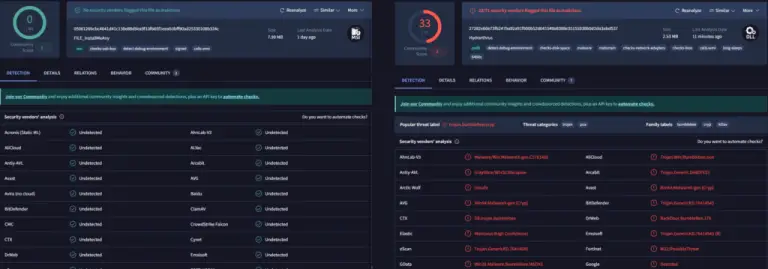
Hackers have compromised the official website of RVTools—a widely used utility for managing VMware virtual infrastructures—and replaced...
The developers have released updates for several versions of the Linux kernel, including 6.14.7 and other actively...
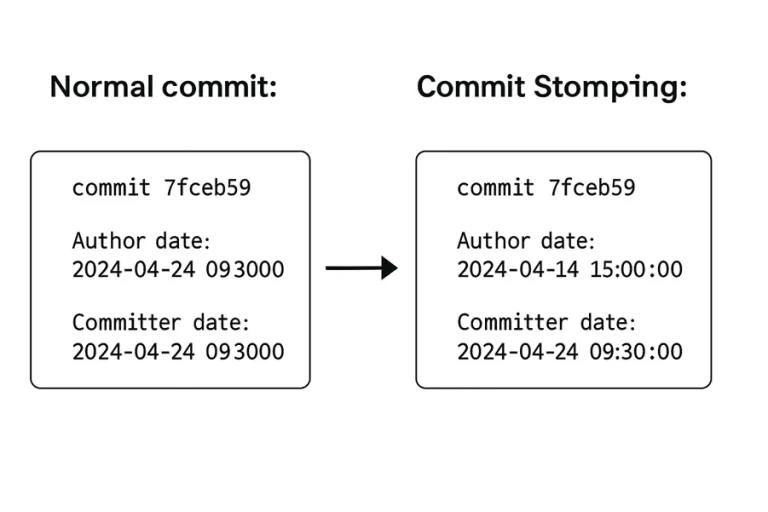
A method for concealing change history has been uncovered in Git, capable of misleading even seasoned digital...
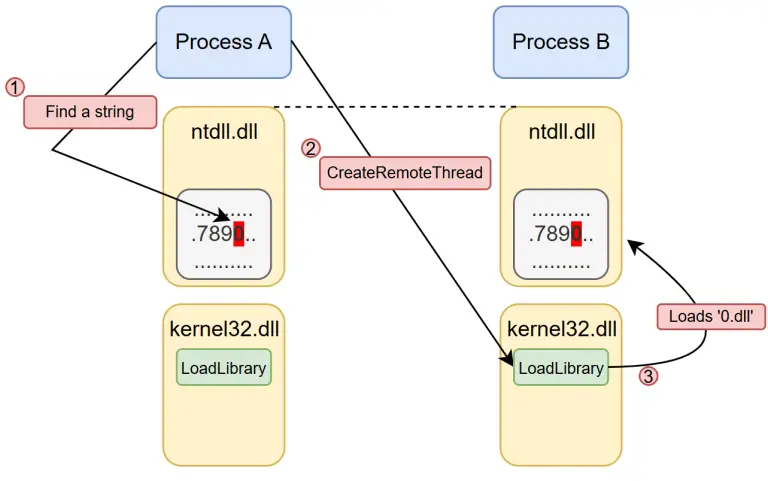
Recent research has demonstrated novel techniques for injecting malicious code into Windows processes without relying on traditional...
The Eventin plugin, widely used for event management on WordPress websites, was found to be vulnerable to...
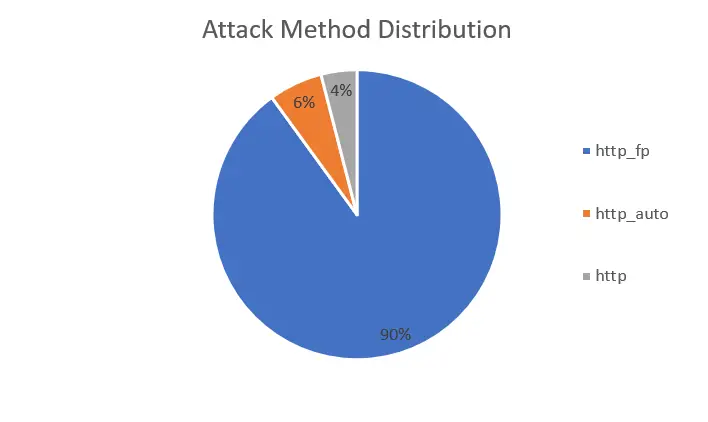
Experts at the Chinese cybersecurity firm NSFOCUS have identified an active campaign involving a new botnet known...
For at least six months, official software for Procolored printers had been silently distributing malware — including...