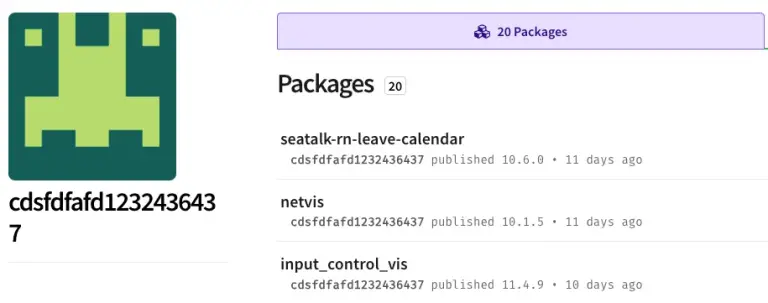
Researchers at Socket have uncovered over 60 malicious packages in the npm registry that covertly harvest data...
Security
Three zero-day vulnerabilities have been discovered within the networks of major telecommunications companies with direct exposure to...
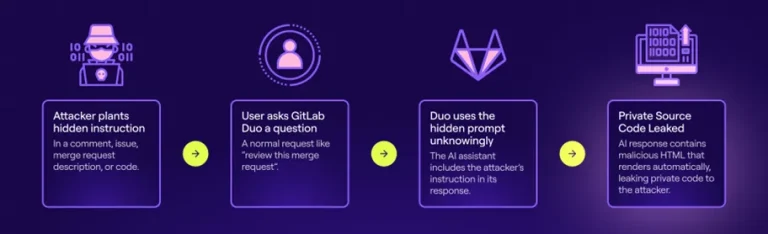
Artificial intelligence tools, heralded as indispensable companions for software developers, are increasingly revealing themselves as vectors of...
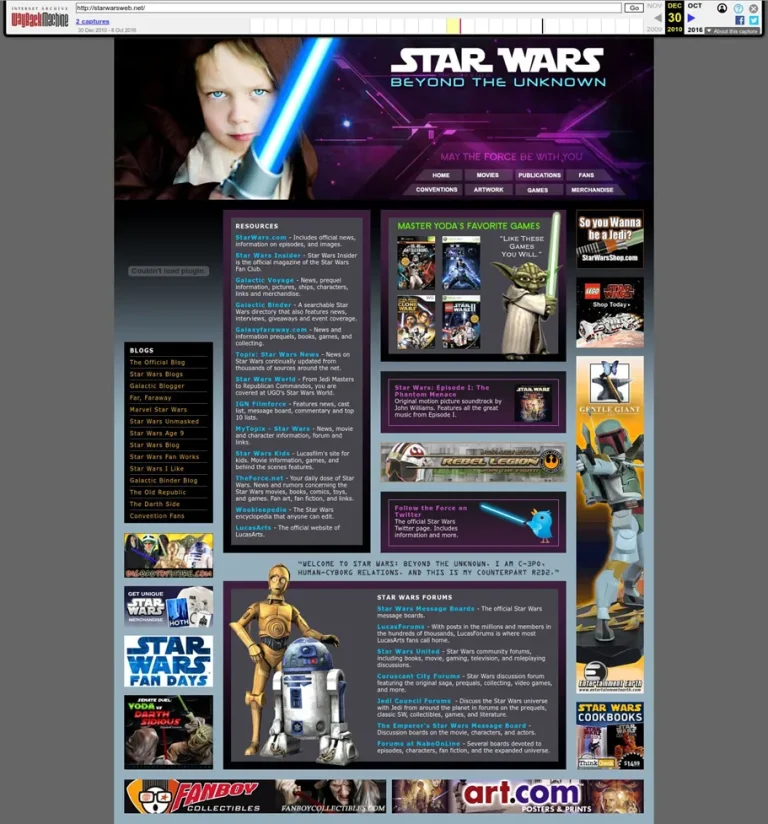
At first glance, starwarsweb.net appears to be a typical fan site from the golden age of the...
Over the past six months, SVG files have unexpectedly emerged as a favored weapon in the arsenal...
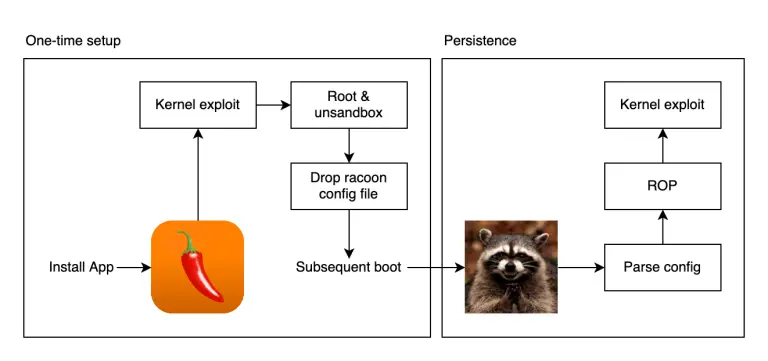
Five years ago, on May 23, 2020, the jailbreak community witnessed a historic precedent: the public release...
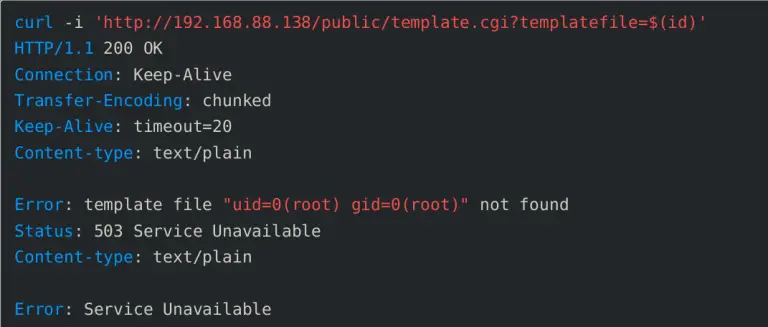
The ONEKEY Research Lab team has uncovered a critical vulnerability in the firmware of MeteoBridge—a compact device...
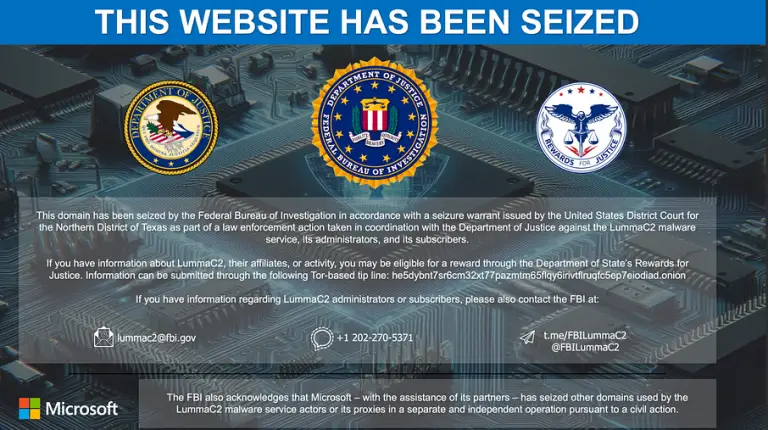
Following the resounding announcement by Microsoft and the FBI regarding the complete dismantling of the Lumma Stealer...
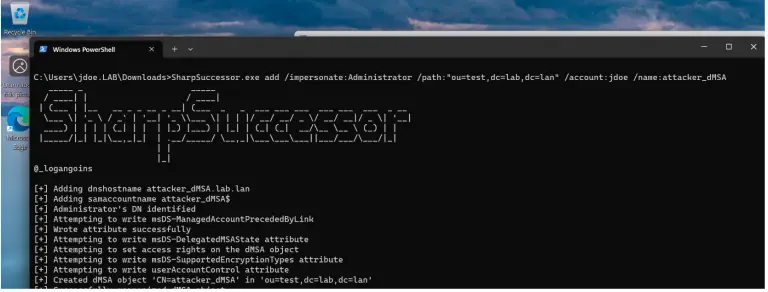
A fully functional exploit tool has been released for the previously discovered critical vulnerability in Windows Server...
The American cybersecurity apparatus now faces a dual threat: the escalating activity of cybercriminals and sweeping cuts...
The hospitality industry has become a veritable haven for cybercriminals, largely due to catastrophically weak passwords safeguarding...
The decentralized exchange Cetus Protocol has become the victim of one of the largest heists in the...
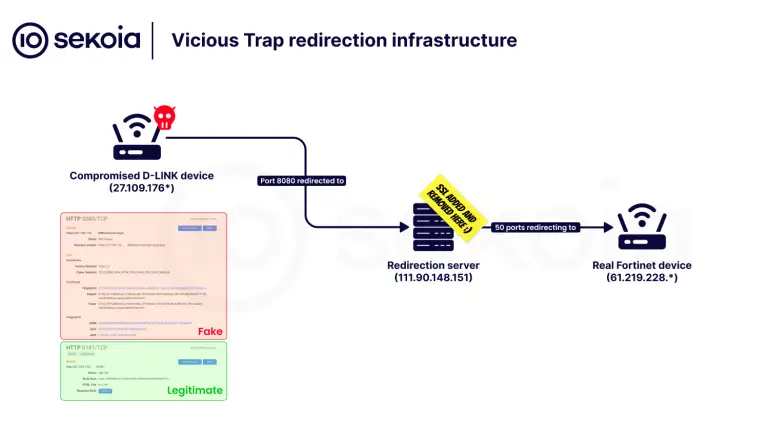
Cybersecurity experts at Sekoia have uncovered a large-scale campaign in which an unidentified group, operating under the...
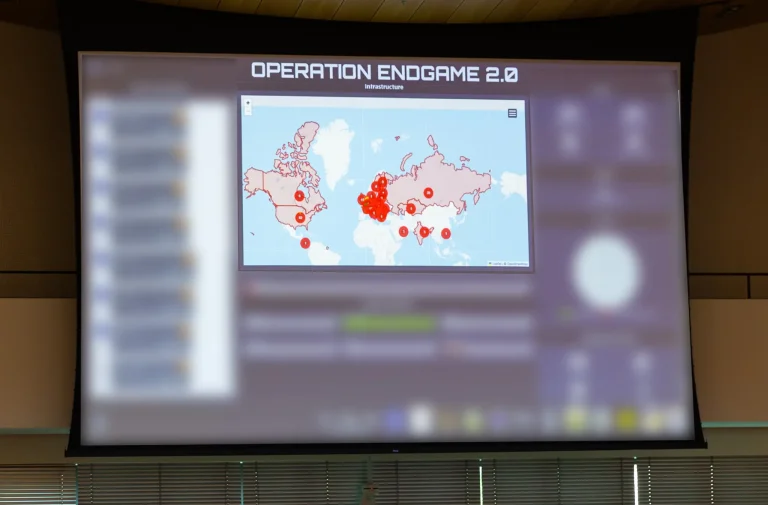
Police operations targeting cybercriminals and dark market traders are gaining unprecedented momentum. Two major international campaigns—Operation Endgame...
A cyberattack targeting the cloud infrastructure of Commvault has resulted in unauthorized access to customer data, specifically...