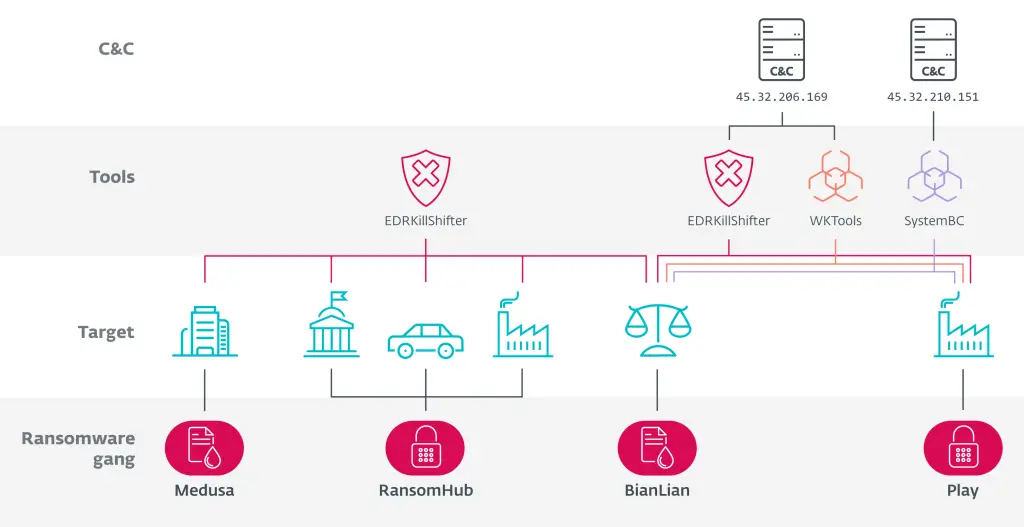
Schematic overview of the links between Medusa, RansomHub, BianLian, and Play | Image: ESET
A recent investigation conducted by ESET has uncovered intricate ties between several ransomware groups — RansomHub, Medusa, BianLian, and Play. The common thread linking them is a specialized tool designed to disable security systems, known as EDRKillShifter, originally developed by operatives affiliated with RansomHub. Despite the closed nature of their respective distribution models, this tool is now being employed in attacks carried out by other groups.
EDRKillShifter leverages a technique known as Bring Your Own Vulnerable Driver (BYOVD). In essence, attackers install a legitimate yet vulnerable driver on the compromised system, exploiting it to deactivate threat detection and response mechanisms. This maneuver clears the path for ransomware payloads to execute without interference from antivirus or endpoint protection solutions.
Researchers observed that ransomware developers seldom update their encryptors, aiming to avoid introducing bugs that could damage their reputation. As a result, security software often adapts swiftly, learning to detect these static threats efficiently. In response, affiliate operators increasingly resort to disabling security tools in advance, thereby ensuring the ransomware executes unimpeded.
Particularly noteworthy is the fact that EDRKillShifter was originally tailored for RansomHub affiliates, yet has surfaced in operations attributed to Medusa, BianLian, and Play. The latter two groups are especially known for maintaining strict trust boundaries and rarely accepting new members, indicating a potential cross-pollination of tools between otherwise siloed threat actor collectives.
ESET suggests that some participants within these closed Ransomware-as-a-Service (RaaS) ecosystems, despite their internal isolation, may be sharing tools with rivals, including less established actors. Such behavior is highly uncharacteristic for groups that typically rely on a curated arsenal of vetted intrusion methods.
Analysts believe that a single operator, provisionally dubbed QuadSwitcher, could be behind a series of recent incidents. Several hallmarks of these attacks align closely with tactics commonly associated with the Play group, hinting at a possible direct affiliation.
Moreover, EDRKillShifter has also been observed in attacks linked to another affiliate, CosmicBeetle, who reportedly used the tool in at least three operations attributed to RansomHub and LockBit.
The BYOVD technique is gaining traction, particularly within corporate environments. In 2024, the group Embargo employed a tool known as MS4Killer to neutralize security solutions, and more recently, Medusa was found to be using a custom driver called ABYSSWORKER to achieve similar results.
To mitigate such threats, organizations must ensure that adversaries are blocked before obtaining administrative privileges. It is imperative to enable detection of potentially unsafe applications and to vigilantly monitor driver installations—especially those involving components with known vulnerabilities.


