Abstraction of Bring Your Own Installer EDR Bypass | Image: AON
In early 2025, incident response specialists from Aon’s Stroz Friedberg team uncovered a novel technique for bypassing the protective mechanisms of Endpoint Detection and Response (EDR) solutions. This method, dubbed Bring Your Own Installer (BYOI), enables attackers to circumvent security controls and deploy malicious software.
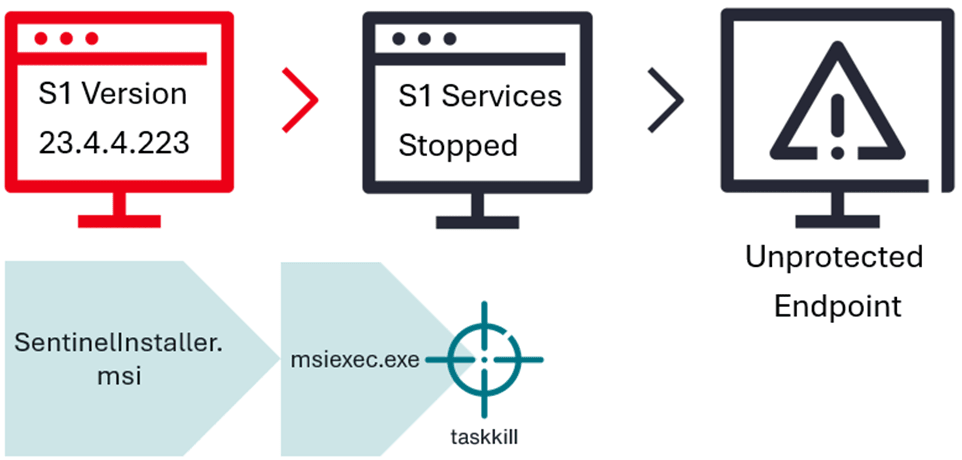
During an investigation into a corporate network breach, the experts discovered that the attackers had leveraged a legitimate installer for SentinelOne. At a precise moment in the update process—immediately after halting system services but before the installation was finalized—the adversaries interrupted the installer’s execution. This brief window of unprotected operation was exploited to activate ransomware on the targeted system.
Unlike other EDR evasion strategies, this technique did not involve third-party drivers or malicious components. The vulnerability resided within the update mechanism of the agent itself. According to John Ayls and Tim Mashni of Stroz Friedberg, the malicious actions were executed with administrative privileges previously acquired through a separate vulnerability in the client’s infrastructure. Testing revealed that the technique was effective across multiple versions of SentinelOne’s software and was not dependent on the specific version installed at the time of the attack.
Following the publication of the report, SentinelOne was informed of the vulnerability and issued mitigation guidance to its clients. The principal recommendation is to enable the “Online Authorization” feature, which is disabled by default. Once activated, this setting requires confirmation via the SentinelOne management console before any installation, removal, or downgrade of the agent can proceed—effectively closing the loophole exploited in the attack.
Despite these advisories, Stroz Friedberg’s analysts observed during subsequent assessments that some organizations had yet to activate the recommended setting, leaving their environments vulnerable to similar exploitation. In addition to notifying its clients, SentinelOne also shared information about the discovered technique with other leading EDR vendors to help preempt broader exposure to the threat.


